Abstract— In this research paper, the researcher focused on impact analysis of attack and defense modeling approach to cyber security which is one of the significant research problem in the real word. Researcher used the real time monitoring, anomy detection, impact analysis, and mitigation strategies. In addition, an attack free formulation based on control networks which is used to evaluate the system by identifying the system’s adversary objectives. The fundamental level, researcher used the methodology that involves port auditing or password strength in the power system control framework is determined based on existing cyber security conditions. Cyber security strategies include identity management, risk management and incident management, which encompasses numerous hardware and software technologies, and can be applied on any level, including personal, corporate or governmental devices or networks. Passwords are a cyber-security tool that people encounter nearly every day. The research focused on some of common cyber security tools include: anti-virus, malware, software, patches, firewalls, two factors authentication, encryption which are the significant components to prevent valuable data and highly sensitive information from unauthorized persons. The researcher developed an attack and defense modeling approach to solve the cyber security problem in the organizations or enterprises.
Keywords—NIST, IS, CIS, MIA, CYBER ATTACK, DEFENSE
I. Introduction
Cyber security is the protection of internet-connected systems, including hardware, software and data, from cyber-attacks. In a computing context, security comprises cyber security and physical security — both are used by enterprises to protect against unauthorized access to data centers and other computerized systems. Information security, the researcher stated that cyber security is one of the significant research issues in current computing environment, which is designed to maintain the confidentiality, integrity and availability of data, is a subset of cyber security.
1.1 ELEMENTS OF CYBERSECURITY
Ensuring cyber security requires the coordination of efforts throughout an information system, which includes:
- Application security
- Information security
- Network security
- Disaster recovery/business continuity planning
- Operational security
- End-user education
One of the most problematic elements of cyber security is the constantly evolving nature of security risks. The traditional approach has been to focus resources on crucial system components and protect against the biggest known threats, and to protect system from the external environments which are creating problems in the computing en and which meant leaving components undefended and not protecting systems against less dangerous risks.
The researcher focused the current research problems and research issues in the computing environments, to deal with the current environment, advisory organizations are promoting a more proactive and adaptive approach. The National Institute of Standards and Technology (NIST), for example, recently issued updated guidelines in its risk assessment framework that recommend a shift toward continuous monitoring and real-time assessments.

1.2 TYPES OF CYBERSECURITY THREATS
The process of keeping up with new technologies, security trends and threat intelligence is a challenging task in the computing environment. However, it’s necessary in order to protect information and system security and other assets from cyber threats, which take many forms.
- Ransom ware is a type of malware that involves an attacker locking the victim’s computer system files — typically through encryption and demanding a payment to decrypt and unlock them.
- Malware is any file or program used to harm a computer user, such as worms, computer viruses, Trojan horses and spyware.
- Social engineering is an attack that relies on human interaction to trick users into breaking security procedures in order to gain sensitive information that is typically protected.
- Phishing is a form of fraud where fraudulent emails are sent that resemble emails from reputable sources; however, the intention of these emails is to steal sensitive data, such as credit card or login information.
1.3 WHAT CYBERSECURITY CAN PREVENT?
The researcher focused on the current research issues and significant impact on use of cyber security can help prevent cyber-attacks, data breaches and identity theft and can aid in risk management. When an organization has a strong sense of network security and an effective incident response plan, it is better able to prevent and mitigate these attacks with respect to computing environment. Cyber security refers to preventative methods used to protect information from being stolen, compromised or attacked. It requires an understanding of potential information threats, such as viruses and other malicious code.
II. LITERATURE REVIEW
Chee-Woo Ten et. al(2010) emphasized on disruption of electric power operations can be catastrophic on national security and the economy. Due to the complexity of widely dispersed assets and the interdependences among computer, communication, and power infrastructures, the requirement to meet security and quality compliance on operations is a challenging issue. In recent years, the North American Electric Reliability Corporation (NERC) established a cyber-security standard that requires utilities’ compliance on cyber security of control systems.
Atul Bamrara et.,al(2013), the researcher focused on organizations cannot sustain without communication networks linking the vast sources of information spread all over the globe and information technology experts are struggling to design the high performance hardware and software which can cater the needs of today’s’ hi tech firms. The potential threat to secure enormous volume of data with a varied community of cyber criminals is a challenge in the current digital era. The present study is an attempt to reveal the varied cyber-attack strategies adopted by cyber criminals to target the selected banks in India where spoofing, brute force attack, buffer overflow and cross side scripting are found positively correlated with public and private sector banks.
Eric Goetz et.,al(2002) emphasized on cyber-attack techniques are constantly evolving and making use of lessons learned over time. To keep pace with attackers and protect critical information systems in our ever more connected world, defense mechanisms must also become more sophisticated. Often understanding attack techniques more clearly is the first step toward increasing security. Intrusion detection systems (IDS) have been around for a number of years to warn of cyber strikes, but the way they currently analyze data offers a restricted view of cyber-attack activity.
Alexander Kott et. al(2018),The success of a business mission is highly dependent on the Communications and Information Systems (CIS) that support the mission. Mission Impact Assessment (MIA) seeks to assist the integration of business or military operations with cyber defense, particularly in bridging the cognitive gap between operational decision-makers and cyber defenders.
Beyza Unal and Patricia Lewis (2018) focused on nuclear weapons systems were first developed at a time when computer capabilities were in their infancy and little consideration was given to potential malicious cyber vulnerabilities. Many of the assumptions on which current nuclear strategies are based pre-date the current widespread use of digital technology in nuclear command, control and communication systems.
Hamad AL-Mahanadi (2016) focused on cyber-attack is a sensitive issue in the world of Internet security. Governments and business organizations around the world are providing enormous effort to secure their data. Understanding attack models provide more insight into network vulnerability; which in turn can be used to protect the network from future attacks. In the cyber security world, it is difficult to predict a potential attack without understanding the vulnerability of the network. So, it is important to analyze the network to identify top possible vulnerability list, which will give an intuitive idea to protect the network.
Duic et. al(2017) focused on the opportunities provided by the information and communications technology, with a special emphasis on the Internet, have become an integral part of life. However, are we sufficiently aware and prepared as individuals, nations or the international community for the threats coming from cyberspace or for the denial of the use of that dimension of communication, commerce and even warfare? Namely, despite the growing number of users, the Internet is still beyond or below minimum regulation. Those are precisely the conditions for the organization and realization of hostile action in cyberspace.
Caroline Baylon(2014),this research paper is part of Chatham House’s Project on Cyber Security and Space Security, a multiyear research project within the International Security Department examining the security challenges at the intersection of cyber security and space security, drawn from think tanks, academia and industry, set out their views on their country’s cyber security and space security policies. Part II presents international institution perspectives, with contributors from three major bodies (the European Union, the Organization for Economic Cooperation and Development and the UN) providing high-level assessments of challenges at the intersection of cyber security and space security.
Tiong Pern Wong(2011),With increased dependency on the Internet, cyber attacks are fast becoming an attractive option for state adversaries, in part because of the ease of hiding a perpetrator’s identity. In response, governments around the world are taking measures to improve their national cyber defences. However, these defences, which are generally passive in nature, have been insufficient to address the threats. This thesis explores the possibility of employing active cyber defences to improve cyber defences at the national level. Active cyber defines refers to the use of offensive actions, such as counter hacking and pre-emptive hacking, among others, to defend against cyber-attacks. This thesis studies the typologies of active cyber defines and examines how this approach can enhance a state’s cyber defines posture.
Clive James (2016), the researcher focused on technology continues to evolve so also do the opportunities and challenges it provides. We are at a crossroads as we move from a society already entwined with the internet to the coming age of automation, Big Data, and the Internet of Things (IoT). Attack vectors such as botnets, autonomous cars and ransom ware. • Threats including data manipulation, identify theft, and cyber warfare. Tangential issues such as data sovereignty, digital trails, and leveraging technology talent. Every industry has its own lexicon, and the cyber world is no different. While built on technological foundations that we all know – computers, the internet, smartphones, and similar – as you delve deeper into the subject you start to encounter acronyms and technical concepts that you may not be familiar with.
Bryan Watkins (2014), the researcher focused on private business has a significant impact on economic and national security and governments want to have a stake in protecting critical private infrastructure as it does with other government assets. As nations push to boost their cyber capabilities the ability of government to incentivize the private sector to share information in a timely manner will greatly impact the effectiveness of cyber security management. In 2013, NSA Director General Keith Alexander stated that cyber-attacks on private industry were gaining so much that governments would need to step in to defend the private sector without a change in security posture.
Timothy M. McKenzie(2018), focused on a strong US cyber deterrence strategy will have the most immediate effect on nation-states whose actions can be influenced by US instruments of national power. However, nations such as North Korea and Iran have shown an incredible resistance to US political and economic pressure and may be difficult to deter without credible threats of military actions. The United States should also pursue a strategy to deter common hackers, criminals, violent nonstate actors, and other non-nation-state actors.
Afraa Attiah et. al (2018),Most of the cyber security research focus on either presenting a specific vulnerability or proposing a specific defense algorithm to defend against a well-defined attack scheme. To analyze the interactions between the attacker and the defender as a non-cooperative security game. The key idea is to model attackers/defenders to have multiple levels of attack/defense strategies that are different in terms of effectiveness, strategy costs, and attack gains/damages. Each player adjusts his strategy based on the strategy’s cost, potential attack gain/damage, and effectiveness in anticipating of the opponent’s strategy.
Michael Robinson et.al (2015), focused on cyber warfare is a vast one, with numerous sub topics receiving attention from the research community. We first examine the most basic question of what cyber warfare is, comparing existing definitions to find common ground or disagreements. We discover that there is no widely adopted definition and that the terms cyber war and cyber warfare are not well enough differentiated. To address these issues, we present a definition model to help define both cyber warfare and cyber war. The paper then identifies nine research challenges in cyber warfare and analyses contemporary work carried out in each. We conclude by making suggestions on how the field may best be progressed by future efforts.
Eric M. Hutchins et. al(2005) focused on the conventional network defense tools such as intrusion detection systems and anti-virus focus on the vulnerability component of risk, and traditional incident response methodology presupposes a successful intrusion. An evolution in the goals and sophistication of computer network intrusions has rendered these approaches insufficient for certain actors. A new class of threats, appropriately dubbed the “Advanced Persistent Threat” (APT), represents well-resourced and trained adversaries that conduct multi-year intrusion campaigns targeting highly sensitive economic, proprietary, or national security information.
Kenneth Geers (2011), the researcher argues that computer security has evolved from a technical discipline to a strategic concept. The world’s growing dependence on a powerful but vulnerable Internet – combined with the disruptive capabilities of cyber attackers – now threatens national and international security. Strategic challenges require strategic solutions. The author examines four nation-state approaches to cyber-attack mitigation.
Stuart Fowler (2018), the researcher focused on within Defense, cyber resiliency must be incorporated across the entire capability lifecycle, and the associated policy development needs to be cognizant of this holistic need. The specification of cyber-resiliency requirements needs to be improved, further importance needs to be placed on cyber security in the architecture and design phases, and cyber-security test and evaluation needs to be an integral part of overall test activities. To achieve this, a new Defense organization has been proposed and its broad responsibilities outlined.
III. problem statement
Cyber-attack is one of the significant research issues in current computing environments. The semantic meaning of cyber-attack is disrupting the computing services with immediate effect in organizations or enterprises. The researcher focused on the some of the current research issues of the cyber-attack and detection with the help of case study.
IV. RESEARCH OBJECTIVES
The researcher stated the some of the current research issues with respect to cyber-attack and detection. In this research paper, the research stated the some of the research objectives to find out possible solution in case of system or workstations are affected by cyber-attack.
- To study the causes of cyber attack
- To study the factors which are responsible for cyber- attack.
- To identify the solution in case disruption by cyber -attack.
V. attack and defence modeling approach
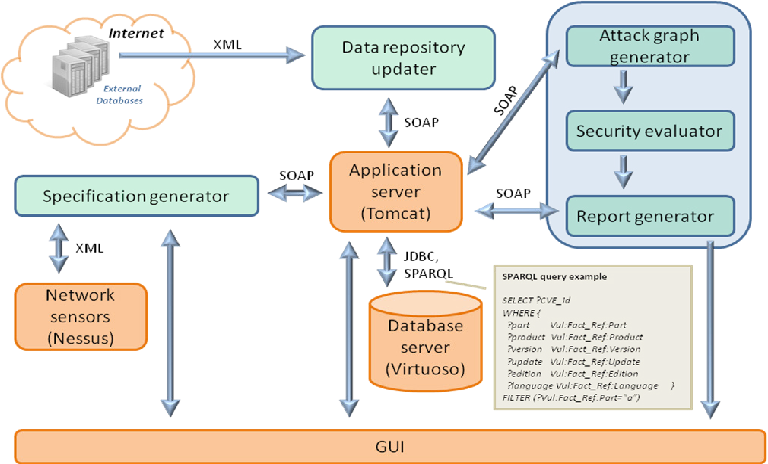
Fig.1.1: Attack and Defense Modeling Approach
The researcher developed a framework of the research study to identify the cyber-attack and defense modeling approach. It constitutes an attractive trade-off in terms of readability, modeling power, scalability and quantification capabilities. This paper develops and completes the theoretical foundations of such an adaptation and presents new developments on defensive aspects. In particular, detection and reaction modeling are fully integrated in an augmented theoretical framework. Different use-cases and quantification examples illustrate the relevance of the overall approach.
VI. RESEARCH METHODOLOGY
The researcher used the researcher methodology to prevent the cyber-attack in the computing environment. As the virtual dimension of the society, introduces the huge, complex, heterogeneous and mutually interrelated content of a cyber-security strategy. The requirements for that content are drawn either from government or from business sectors/subsectors, either nationally or internationally. A comprehensive coordination and management system need to be established and has to rely on responsible organizations from different societal sectors, regulated by different national and international laws and regulations. Strategy drafting process has to be organized with a number of diverse institutions that are stakeholders in certain parts of this huge field of cyber security. Moreover, the final proposal of a national strategy has to be communicated and harmonised on the widest level of the society to prevent cyber-attack and defence in computing environment.
The attack and defence modelling approach of a consistent strategy document with such complex requirements should be based on a method that will assure consistency of the results obtained through the various development phases and diverse stakeholders that need to participate in the strategy development process. Using such method for a strategy development should also allow for much easier way to periodically update or revise the strategy with respect to cyber-attack and defence.
III. CASE STUDY
CASE STUDY-1: A CASE STUDY OF THE 2016 KOREAN CYBER COMMAND COMPROMISE
On October 2016 the South Korean cyber military unit was the victim of a successful cyber-attack that allowed access to internal networks. Per usual with large scale attacks against South Korean entities, the hack was immediately attributed to North Korea. Also, per other large-scale cyber security incidents, the same types of ‘evidence’ were used for attribution purposes. Disclosed methods of attribution provide weak evidence, and the procedure Korean organizations tend to use for information disclosure lead many to question any conclusions. The researcher analyzed and discussed a number of issues with the current way that South Korean organizations disclose cyber-attack information to the public. A time line of events and disclosures will be constructed and analyzed in the context of appropriate measures for cyber warfare. Finally, the researcher examined the South Korean cyber military attack in terms previously proposed cyber warfare response guidelines. Specifically, whether any of the guidelines can be applied to this real-world case, and if so, is South Korea justified in declaring war based on the most recent cyber-attack.
One thing that needs to be mentioned specific to South Korea’s situation with North Korea, is that applying international law itself could be problematic. North Korea is a state with limited recognition; South Korea considers North Korea to be a part of the same nation and vice versa (Scoffed, 2005). Therefore, in theory, should an offensive cyber operation be proven to be North Korea’s doing, they would fall under Korean Criminal Law. However, in reality attempts to push South Korea’s criminal law to North Korea would more likely be detrimental. Potential solutions and responses should be found within international law; even in cases without physical damages.
CASE STUDY-2: CYBER WARFARE CONFLICT ANALYSIS AND CASE STUDIES
The first objective was to research historical cyber warfare incidents from the past to the present and capture relevant data in a data acquisition phase. The first phase needed to analyze the timeline of events in this incident and develop the necessary insight to be able to analyze the parties involved in order to mark them as status quo side or non-status-quo side. This provided an indication of motive from the no status-quo side and the progression of escalation. The second objective involved mapping the cyber-warfare incidents to MIT’s CASCON framework. The CASCON mapping presented the data collected from the incidents in a structured form, which is important since its database of kinetic warfare was extensive. The CASCON based analysis for cyber-incidents not only revealed insights into what actually happened during a cyber-incident, but helped answer key questions that could potentially cover some predictive behavior of involved states and conflicts in a region. There is undoubtedly a large amount of knowledge that is to be learned and considered, both from the historical point of view that CASCON provides and from current affairs. The results of this thesis are not meant to be conclusive, but a study of state-sponsored cyber- cases using MIT’s CASCON to map and categorize information for future learning about conflicts involving states. The researcher found that some of the following facts:
- Reduced costs compared to conventional strikes.
- Higher efficiency in achieving the goal.
- The asymmetric nature of the cyber-attacks makes defense difficult.
- The anonymous nature of the offense allows the attacking government to circumvent approval by the world community compared with a military offensive.
- Possibility to conduct cyber-attacks in peacetime for immediate geopolitical ends, as well as to prepare for possible future kinetic attacks.
VII. Conclusion
In this research paper, the researcher focused on the impact analysis of attack and defense modeling approach to cyber security which is one of the significant research issues in current computing environment. The researcher developed a modeling approach to identify and the causes of cyber-attack and providing a virtual based solution which are having limited access and usability in the computing environment. The researcher also stated the current research issues of cyber- attack and defense in computing environment. Through the modelling concept, the researcher proposed a model to prevent cyber-attack and defense which are the significant to prevent the cyber-attack services in the computing environment.
We provide a wide range of science paper writing services. Some of the research and writing services that we offer include:
– Science Assignment Help
– Science Homework Help
– Natural Sciences Writing Services
– Neuroscience Writing Services
– Data Science Writing Services
– Mathematics Assignment Writing Services
– Social Science Writing Services