Migration Plan for Threat Report; Cybersecurity and Fraud Mitigation
Executive Summary
Cybersecurity helps to mitigate fraud activities like phishing, hacking and many more activities. All these activities are illegal and the government of Australia is also trying to stop this kind of activity with the help of Cybersecurity. Monitoring risk factors with the help of an intrusion detection system helps to deal with this kind of activity. All those things are going to be highlighted and how B&C Insurance companies avoid this kind of thing are going to be discussed in this report.
Introduction
In every industry, there are some threats that exist and every organization tries to mitigate this issue with a proper plan. This kind of plan is known as a threat mitigation plan. Currently, every organization is trying to focus on providing better security by improving its issues in the organization. This thing can help to secure data as well as privacy to any intruder. An intrusion detection system is a good alternative but it is better to prevent that activity rather than just defending the issue in the organization. Risk reduction and better optimization of security is the main aim of any organization. Cybersecurity issues are rapidly increasing and it causes severe damages to the organization. In this report, a mitigation plan or guidance to avoid cyber threat-related issues are going to be discussed and how B&C Insurance companies implement proper action in their organization are going to be analyzed. The company need to manage the risks here properly and according to that some key parts are going to be discussed. The report is going to explore threat model for the B and C company and the strategies for mitigating those risks.
Threats prioritization
Threat prioritization is the most important process as it helps to take proper actions after analyzing the risk level. Cybersecurity issues can affect organizational growth very badly and it can create an economic factor in the business (Vasiu & Vasiu, 2018). Identifying each risk event is the primary aim to do this kind of analysis. Dimension of information security depends on some factors. Wider knowledge in the IT field can make a negative impact if they abuse the information (Siponen, 2018). It is important to know risk factors closely in order to make a substitute plan or any defence mechanism to avoid any threat activity in the organization. Planning is necessary and identifying risk priority is more important than planning as it is not possible to prepare a plan without proper threat identification with their harmful capability.
| Risk level | Description |
| Extreme (E) | After analysing the present condition of B&C Insurance company, the most important risk is associated with phishing. This is a big threat for the company as it helps to steal data without notifying the user. It is possible that an employee clicks on a link and he gives access to the company’s data unintentionally. Phishing related awareness is required to make a sustainable business (Dodge, Carver & Ferguson, 2019). |
| Height (H) | Ransomware is another big threat for the organization as it takes access without any notification and this malware is highly programmed. The programmer can make demands to give the access back. This kind of thing is on the second priority list when it comes to threat prioritization. |
| Medium (M) | DDoS is highly treatable but this kind of activity can be tracked with the help of an intrusion detection algorithm that is why it comes on the third list of prioritization. This kind of attack can interrupt the operation mechanism. |
| Low (L) | Malware can make changes in the system but it is not a threat like phishing or ransomware. Malware can send data but systems can recognise this kind of threat that is why it comes last on the threat priority list. |
Table 1: RISK priority
(Source: Self-Created)
Analysis of the case in terms of risks
- Disconnection with the server
It is very important to establish a stable connection when it comes to business. It is very possible that this thing happens because of the phishing links in the organization. A company’s crucial information and data sets can be leaked in the business market and competitors can take this advantage. If anyone gets to know the server-id and IP address then intruders can modify the network and deploy a huge loss to the company. Passwords and critical information related to the organization can get leaked if any employee unintentionally clicked on a phishing link. It is also a potential threat to information security (Moti et al, 2020). The main reason behind this disconnection is to give unauthorized access and this thing can be mitigated if every employee started avoiding unknown links and emails.
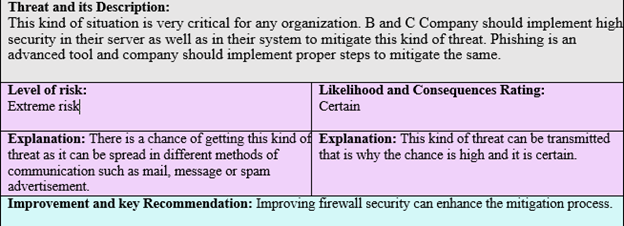
Threat and its Description:
This kind of situation is very critical for any organization. B and C Company should implement high security in their server as well as in their system to mitigate this kind of threat. Phishing is an advanced tool and company should implement proper steps to mitigate the same.
Level of risk:
Extreme risk Likelihood and Consequences Rating:
Certain
Explanation: There is a chance of getting this kind of threat as it can be spread in different methods of communication such as mail, message or spam advertisement. Explanation: This kind of threat can be transmitted that is why the chance is high and it is certain.
Improvement and key Recommendation: Improving firewall security can enhance the mitigation process.
Figure 1: Threat description 1
(Source: Self-Created)
- Unable to access the system
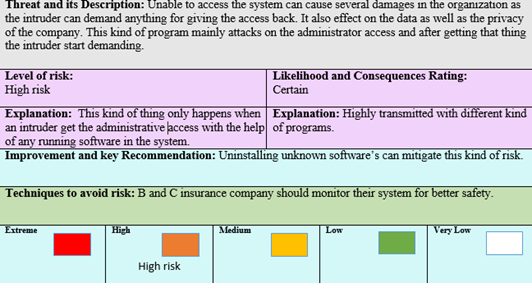
This is the second common failure due to unauthorised access. It is a kind of similar activity to disconnection with the server. This thing happens because of the second threat known as ransomware. This programme can control the system and it is very dangerous for the organization as no one can get administrator access. This issue can be mitigated by uninstalling
Level of risk:
High risk Likelihood and Consequences Rating:
Certain
Explanation: This kind of thing only happens when an intruder get the administrative access with the help of any running software in the system. Explanation: Highly transmitted with different kind of programs.
Improvement and key Recommendation: Uninstalling unknown software’s can mitigate this kind of risk.
Techniques to avoid risk: B and C insurance company should monitor their system for better safety.
Figure 2: Threat description 2
(Source: Self-Created)
- Malfunctioning website
In most case studies, it has been found that every organization faces this kind of issue in their organizational life. It is also known as a malfunction of a network. This kind of issue can be solved by implementing better website security. Client handling rates can be controlled with the help of software. Monitoring website security can also help to avoid this kind of risk when it comes to any business organisation such as B and C Insurance Company.
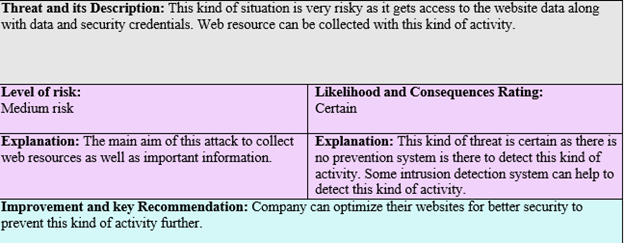
Threat and its Description: This kind of situation is very risky as it gets access to the website data along with data and security credentials. Web resource can be collected with this kind of activity.
Level of risk:
Medium risk Likelihood and Consequences Rating:
Certain
Explanation: The main aim of this attack to collect web resources as well as important information. Explanation: This kind of threat is certain as there is no prevention system is there to detect this kind of activity. Some intrusion detection system can help to detect this kind of activity.
Improvement and key Recommendation: Company can optimize their websites for better security to prevent this kind of activity further.
Figure 3: Threat description 3
(Source: Self-Created)
- System failure
System failure is a common failing and this kind of thing mainly happens because of malware. Sometimes systems fail to remove small malware and this makes this happen. Too many software can do the same thing but removing malware is the most important thing in order to complete each process easily. B and C Insurance Company can mitigate this kind of threat by implementing a monitoring system such as antivirus. Wannacry attack is an example of a malware attack (Offner et al. 2020).
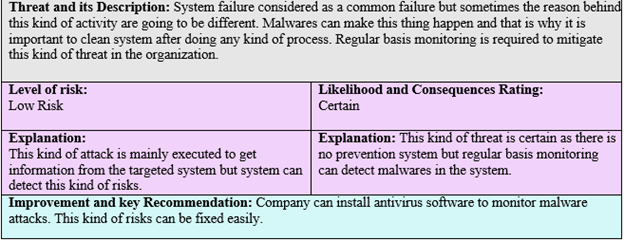
Threat and its Description: System failure considered as a common failure but sometimes the reason behind this kind of activity are going to be different. Malwares can make this thing happen and that is why it is important to clean system after doing any kind of process. Regular basis monitoring is required to mitigate this kind of threat in the organization.
Level of risk:
Low Risk Likelihood and Consequences Rating:
Certain
Explanation:
This kind of attack is mainly executed to get information from the targeted system but system can detect this kind of risks. Explanation: This kind of threat is certain as there is no prevention system but regular basis monitoring can detect malwares in the system.
Improvement and key Recommendation: Company can install antivirus software to monitor malware attacks. This kind of risks can be fixed easily.
Figure 4: Threat description 4
(Source: Self-Created)
Strategies for mitigating risks
- Information security awareness
It is very important to spread awareness on every aspect to maintain organization growth with proper security implications. Employees can click on vulnerable links and this is why it is important to spread awareness in the organization. According to McCormac et al. 2018 Information security awareness is related to job stress. So it is important to maintain a healthy relationship with employees to give them proper awareness lessons to mitigate risks in the organization. A phishing attack can be mitigated with this kind of strategy.
- Administrator assistance
Awareness training has so many effectiveness when it comes to business operations (Shaw et al. 2019). Administrator assistance is helpful when a user forgets a system password or information. Administrator assistance can verify the user before changing the administrative password. This kind of strategy is very useful when it comes to protecting a system from a ransomware attack. This is the best way to deal with this kind of situation as it will verify the user. If a user fails to verify its identity then administrator assistance will automatically block that user as well as secure the system.
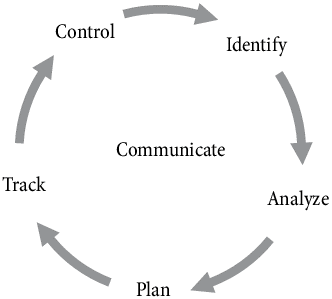
- Continuous risk management
Continuous risk management is very important to make continuous growth in the organization. Managing proper risk management is one of the best strategies to develop better security in terms of the risk mitigation process. Organisational policies can spread awareness and it helps to manage cybersecurity-related risks (Pendley, 2018). B & C Insurance Company can follow specific plans to enhance the risk management process. Tracking threat information is necessary to prepare a continuous risk management strategy. The control and identification part comes accordingly after the tracking of the risk. The final stage is to analyse the issue and prepare a plan. This process should be completed to make improvements in the risk management process. This process can be helpful to reduce DDoS attacks in the system.
Figure 5: Continuous risk management
(Source: self-created)
- Proper monitoring
In every organization, there are some threats as well as opportunities. Monitoring all suspected things can help to mitigate this kind of risk issue in the B & C Insurance Company. System monitoring is the best way to protect organizational data as well as mitigating cyber threats. Security perceptions can be analysed by monitoring (Furnell, Bryant & Phippen, 2019). Proper monitoring helps to analyse system GAPs and gives an idea about system issues. Malware can be detected with a proper monitoring process and it can help the organization to get get rid of them. System hard drives such as pen drives or hard disks should be monitored to mitigate copying risk.
Possible improvements and justification
B & C Companies can get opportunities if they implement proper strategies in the organization. All those possible improvements have been discussed below-
- Better security in threat detection
If the company implement a good strategic approach then it can give better efficiency when it comes to performance (Jalali, Siegel & Madnick, 2018). The company can influence their employees to avoid phishing links by developing awareness and this process can help to detect those threats in the organization. The company can deploy security software to verify all credentials when the system starts. Enhancing security is the best way to gain success in the business market.
- More business growth
Effective security and awareness can enhance business operations tactics (Aloul, 2019). It is more important to make employees more aware of possible threats and gaps in the organization. Customers can gain their trust if they notice this kind of mitigation plan. It will enhance business growth in the organization.
Recommendation after analysing current risk level
After analysing the current risk level, the most important thing that company should consider is to mitigate phishing links in the organization. It also has a high-risk level and it is uncertain. So the company should make a monitoring strategy for reducing the threat level of phishing. Spreading awareness is the first way to reduce its capability and the second one is to implement a security mechanism or an intrusion system. Except for this risk, all other threats can be controlled by all the above strategies which have already been discussed.
Recommendation to the CEO
Decision making is an important process and B&C Insurance Company should consider this thing to get more benefits from customers. The company should look out for substitutes if any threat makes any kind of damages. The Decision-making process should be enhanced to clear employees doubts. Phishing related all information should be shared with all employees and spreading maximum awareness regarding cybersecurity can help the organization. If employees get to know the fundamental thing then it will be an easy approach to mitigate threats.
A monitoring mechanism is very important to monitor all data along with the login and log off credentials of every employee. System tracker kind of software can be used to enhance this monitoring process. The overall threat mitigation plan is good but some customizations are still required to get maximum performance from it. This mitigation plan is helpful when the risk level is low. The company should adopt new approaches to make a wider move when it comes to the threat mitigation process. These implementations are required to get enhanced performance.
Conclusion
B&C Insurance Company can enhance the risk management process by implementing different techniques and new threat detection algorithms. These things are required to ensure better security in the organization. The threat detection mechanism is very helpful when it comes to the threat detection part. Every organization makes bold movements to detect threats in their organization. B&C Insurance Company should deploy key strategies to prevent threats in their organization. After analyzing all facts and data it can be concluded that the improvement can be noticeable if they choose this kind of threat mitigation strategy. The threat mitigation process can help to sustain organizational growth as well as it will help to protect organizational data. B&C Company should think about implementing strategies and that strategy can give benefit by managing cyber-related risks and frauds. An intrusion detection mechanism can be considered as it is an efficient way to prevent cyber-attacks. The company should implement a monitoring committee to see all credentials with the help of an intrusion detection system. This is effective and that can be managed within some key aspects as well. the CEO need to observe all the design and aspects here as well and according to that some key parts need to be analyzed the software development and evaluation can be seen here effectively as well and that can help in managing some signification growth as well.