The Life of a Stolen Credit Card
Introduction
Identity theft is mostly associated with credit card theft. The later occurs when cardholders’ financial information is obtained by unauthorized individuals and utilized with fraudulent intent. Due to the increasing sophistication of card theft and the streamlined processes of profiting from the crime, it is imperative that consumers and industry practitioners reflect on the life of a stolen credit card. To achieve this objective, this report details the strategies that “carders” use to obtain fraudulently card information and the ecosystem established to ensure that they profit from this information. The multi-page report closes with a set of recommendations and observations on how to increase card information security and reflects on unresolved and emergent vulnerabilities in the card-processing infrastructure.
Strategies for Credit Card Theft
The credit card ecosystem depends on the relationship between acquiring (i.e. accepting) and issuing banks and customers (Anderson, Manifavas & Sutherland, 1996). The issuing bank extends credit to the customer in the form of a credit card while the acquirer bank processes the credit card payment made by the consumer. The positions of these players in the payment chain represent opportunities for credit card theft and, broadly, identity theft (Anderson, Manifavas & Sutherland, 1996). For instance, vulnerabilities on the side of the issuing or acquiring bank such as insider threats or processor breaches jeopardize the security of personal information (Krebs, 2015a).
Points of weaknesses in this processing infrastructure include point of sales terminals, automated teller machines (ATMs), customer databases such as those operated by electronic commerce sites, Internet banking, and insurance firms, and user or personnel files. These technologies are, in themselves, attack vectors and threats are delivered by means of insider or outsider threats and through third party vendor breaches. This section discusses the means or strategies by which financially motivated actors steal credit card data including through ATM skimmers, point of sale (PoS) attacks, and data breaches.
Skimmers
Automated teller machine (ATM) and gas pump skimmers are often tied to organized crime (Krebs, 2015a). The link between skimmers and organized is uniquely chronicled in extant resources (Martinez, 2014; Krebs, 2015b). Information obtained through this attack vector, while likely discoverable by card associations and banks, can last numerous months and are superlatively difficult to prosecute (Krebs, 2015a).
Figure 1 – An ATM PIN capture overlay device retracted to reveal the actual PIN entry pad (Adapted from (Krebs, 2010))
Skimmers have also been encountered in the wild in point of sale terminals such as for VeriFone terminals (Krebs, 2013c), in several Wal-Mart stores in Virginia and Kentucky (Krebs, 2016d) as well as Safeway credit and debit self-checkout terminals stores in Colorado (Krebs, 2016e).
Figure 2 – An overlay skimmer retrieved from a VeriFone self-checkout terminal in use at a Safeway store (Adapted from (Krebs, 2016e))
This overlay skimmer is composed of two components. The first is a PIN pad overlay necessary to capture a user’s PIN and the second records credit or debit card data stored in the magnetic strip. Notably, while only one store using this PoS system was compromised, numerous other retailers in the United States use VeriFone terminals (Krebs, 2016d).
Figure 3 – An overlay credit card skimmer retrieved from an Ingenico self-checkout PoS terminal at a Wal-Mart store with a device (bottom) for offloading stolen data (Adapted from (Krebs, 2016d))
As with the previous overlay skimmer, this particular device captures PIN and magnetic stripe information and is easy to attach to terminals (Krebs, 2016). Additionally, skimmers have been deployed in fuel stations most notably in Arizona (Krebs, 2016f). Almost all the mostly Bluetooth-based skimmers targeted Gilbarco on-pump card readers (Krebs, 2016f).
Figure 4 – An external fuel pump-skimming device (Right) (Adapted from (Krebs, 2015g))
Figure 5 – An unaltered fuel pump card slot (Left) and a card slot with a Bluetooth-based skimming device attached (Right) (Adapted from (Krebs, 2013h))
While there have been innovations in the techniques and methods of designing and installing skimmers, it is noteworthy that a 3D-printed ATM skimmer has been retrieved from the wild (Krebs, 2011i). The ability to 3D print these devices implies that the costs will lower and accessibility to criminals will increase. This particular device comprised of a minituarized spy camera cannibalized from a smartphone to record PIN entries and data ports to allow manual offloading of stolen data (Krebs, 2011i).
Point of Sales (PoS) Breaches
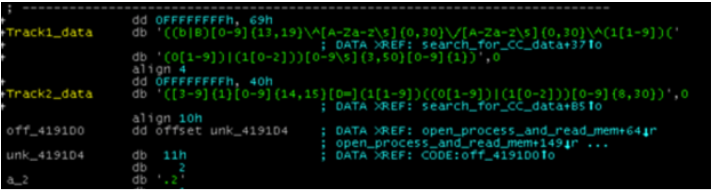
Arguably, the most popular attack vector for point of sales terminals involves RAM scrapping. This technique is achieved through the delivery of PoS malware (Krebs, 2016j). Delivery mechanisms include the use of vulnerability exploits or zero-days, e-mail phishing, keylogging, brute force attacks, Bluetooth “war driving”, and by exploiting weak passwords. Once the malware has been delivered, it then scans the PoS RAM for unencrypted payment data. Scanning us achieved through pre-specified function calls or more commonly, through regular expressions that match with the card dumps. The figures below further illustrate this process.
Figure 6 – Example of PoS malware utilizing regular expressions to match unencrypted RAM data with card dumps (Adapted from (Singh, 2015))
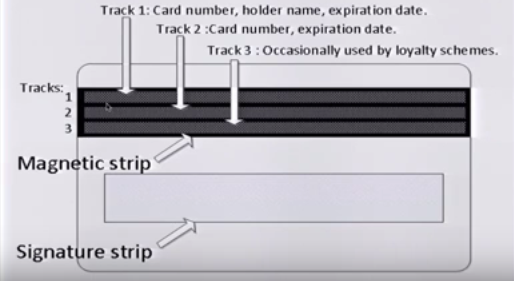
Figure 7 – Diagrammatic depiction of a prototypical magnetic strip credit card showing where Track 1, 2, and 3 data is stored (Adapted from (Singh, 2016))
Magnetic strip cards store their information in specific formats as illustrated above. The logical and sequential placement of financial information is depicted in the tracks 1, 2, and 3. This placement facilitates the automated reading of data and, coincidentally, enables exploitation by malware. Point of sale malware steal these track data dumps and convert them into actionable credit card information for fraud purposes.
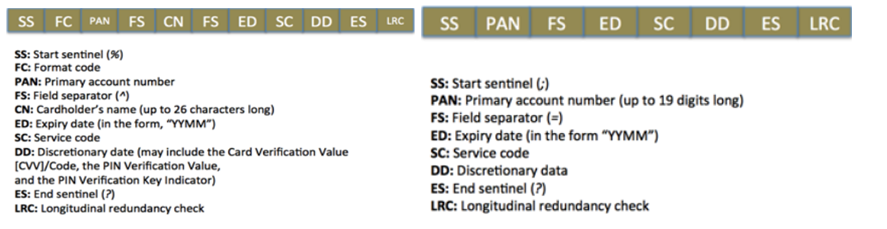
Figure 8 – Track 1 (Left) and Track 2 ( Right) data dumps showing how regular expressions match card data in PoS RAM (Adapted from (Singh, 2015))
Figure 9 – Example of Track 1 data dump containing enough information to be converted into Track 2 information (Adapted from (Singh, 2015))
The use of malicious software to “jack” public ATM machines is also another accelerating trend (Krebs, 2014k). In 2014, Kaspersky Lab documented the ATM-specific malware Backdoor.MSIL.Tyupkin that rapidly spread from Eastern European banking institutions to Asia and the continental Americas as depicted below. Several other researchers have also documented malware jackpotting of ATM machines (Borland, 2013).
Figure 10 – Malware submission of Backdoor.MSIL.Tyupkin in mid-2014 (Adapted from (GReAT, 2014))
Point of sale terminals are deployed in numerous commercial properties such as restaurants, convenience stores, supermarkets, and high street vendors among others. Restaurants and high street merchants represent the widest attack surface area and their point of sales terminals are the most common source of credit card fraud (Krebs, 2015a). Numerous PoS breaches at small vendors have been previously documented (Krebs, 2015l; Krebs, 2015m) Additionally, insider threats in the form of unscrupulous employees are another common form through which such PoS terminals are compromised (Krebs, 2015a). In both cases, consumer losses are high and chances of discovering the fraud are markedly low.
RFID Breaches
RFID-enabled credit cards are no longer a novelty and are targets, along with NFC-enabled payment solutions, of wireless identity theft. Already, 10% of card transactions in the United Kingdom were contactless by early 2016 (Webster, 2016). Although data on RFID-enabled cards in the United States is not updated with a dated report citing a circulation of 3.5% of all credit and debit cards (Consumer Reports Magazine, 2011), several significant studies and demonstrations have already detailed the inherent flaws in these wireless solutions (Newitz, 2006; Heydt-Benjamin et al., 2009; Zetter, 2009; Lee, 2012).
Large Data Breaches
Credit card fraud today is discussed largely within the context of large-scale data breaches. Financially motivated attackers use these breaches as a way to steal numerous records at a go as opposed to the relatively unscalable means of ATM skimming, malware jackpotting, and binary RFID data sniffing. Notable incidents include the 2014 Target hack, multiple Sony hacks, among others. In 2015, with the highest number of reported data breaches in history, 64.6% of reported incidents and 58% of exposed or stolen records were as result of hacking (Kouns, 2016). Privacy Rights Clearinghouse (2016) provides an exhaustive chronology of all reported data breaches between 2005 and 2016.
Table 1 – An example of data breaches
| Corporation targeted | Data/Records stolen |
| CardSystems Solutions Inc. (2005) | 40 million credit card details stolen through hacking (Federal Trade Commission, 2006; Rustad & Koenig, 2007; Hanson, 2008) |
| Central Coast Credit Union (2016) | Credit card details of 60,000 customers (Krebs, 2016n) |
The breach surface area is vast and includes weak passwords for cloud-based services amenable to brute-force attacks, digitized medical records containing valuable personal information, employee complicity or negligence, third-party vendor breaches, and the Internet of Things (Experian, 2015). Other attack vectors include vulnerability exploits and phishing.
Carding Forums
Once financial information has been exfiltrated, attackers have the choice of repurposing the stolen information to launch alternative attacks or, more immediately, selling the data through specialized forums. Carding forums or cybercrime bazaars are the most consequential component of the carding ecosystem. Credit card shops are usually run as forums where buyers and sellers interact to transact in stolen credit card information.
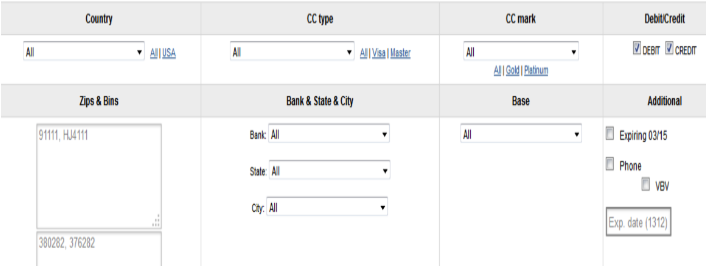
Figure 11 – Screengrab of Rescator.so, a popular carding forum (Adapted from (Singh, 2015))
This site introduced a new innovation when it first offered card dumps from the 2013 Target data breach. The site indexed the financial information by granular parameters such as ZIP code, state, and state (Krebs, 2014o). This can be seen in the figure above.
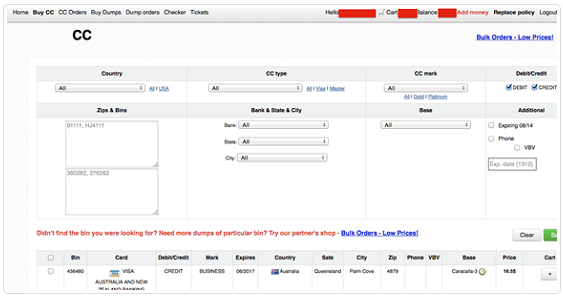
Figure 12 – Rescator panel after buyer log-in (Adapted from (TrendMicro, 2014))
Rescator was the very first carding forum to offer millions of credit card details from the two mega-breaches of Target and Home Depot (Krebs, 2015p). The individual responsible for running Rescator has been associated with other carding shops and online crime forums (Krebs, 2013q) and is considered a key, if not the key, figure in the mega-breaches of Target and Home Depot (Krebs, 2014r) among others (Krebs, 2015s). While Rescator is renowned for selling millions of card dumps from mega-breaches, newcomers such as BriansDump offer large batches of card dumps from small enterprises such as restaurants and bars (Krebs, 2015l).
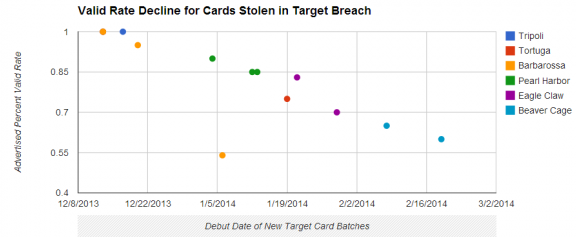
Figure 13 – Scatterplot of the % valid rate for different card batches from the Target breach on sale at Rescator.so between 2013 and 2014 (Adapted from (Krebs, 2014t))
This figure illustrates the falling price in the various card batches as their valid rates declined. The decline is primarily because card holders canelled them or issuing banks declined them. The oldest batch of cards sold on the carding shop- at the top right of the figure- have higher asking prices while newer or fresher batches- at the bottom right of the legend- fetch lower prices (Krebs, 2014t).The Tortuga batch consisted of several millions of cards stolen from the 2013 Target breach. First offered before Target acknowledged the breach in mid December 2013, the batch cited a 100% valid rate. This meant that all purchased cards would be accepted at the points of purchase. Therefore, Rescator.so could demand a higher price, up to $45 per card. For this batch (Krebs, 2014t). The Eagle Claw batch debuted with an 83% valid rate in January 21, 2014, but slid to 70% before the Beaver Cage was released, starting from February 6, with a 65% validity. The latter ended up at 60%, meaning that out of every ten card details purchased, about four would still be valid. Non-US card details, the Barbarossa batch, were often the highest priced (Krebs, 2014t).
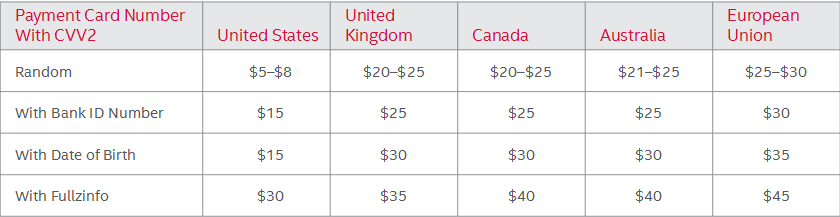
Figure 14 – Estimated per credit/debit card prices for stolen payment card data (from the following card associations: Visa, MasterCard, Amex, and Discover) [in US$] (Adapted from (McFarland, Paget & Samani, 2015))
Figure 15 – Card dump track prices, per card [in US$] (Adapted from (McFarland, Paget & Samani, 2015))
The Carding Ecosystem: Virtual Money Laundering
Online Carding
Online carding represents the process by which credit card data buyers utilize stolen identity information to purchase goods online (Singh, 2015; Vömel, Holz & Freiling, 2010; Holt, 2011). Once an attacker has sold fraudulently obtained data to a buyer, the latter then seeks out opportunities to utilize said information. Credit card data is in one of two formats: “fullz” or card details without the Card Verification Value (CVV) details. Fullz contain all the necessary identifying information required to immediately attempt to make use of the credit card (Vömel, Holz & Freiling, 2010; Holt, 2011). Cards without the CVV, while far cheaper and undesirable, demand that the buyer engage in additional activities such as phishing and social engineering to obtain the details from the original owner or compromised merchants.
However, once the CVV is obtained, the buyer then targets cardable websites (Vömel, Holz & Freiling, 2010; Holt, 2011). Cardable websites must satisfy the following requirements: 1) shipments from the site can be made to other addresses other than the original card owner’s address; 2) international shipping is available; 3) two-step verification are not enabled; and 4) additional security measures are absent or can be circumvented (Singh, 2015).
Offline Carding
Offline carding is generally defined as credit manipulation for in-store purchases, hence is also known as in-store carding (Singh, 2015). To do so, the data buyer converts the card dumps into actual plastic credit/debit cards. This process requires specialized card encoding equipment and software and, where absent, certain carding forums provide allied services (Singh, 2015). Considering that, in numerous occasions, there are no “swipe & PIN” with transactions mostly requiring a swipe and a signature (i.e. “swipe & use”), in-store carding can often prove trivial.
Specialized Services in the Carding Ecosystem
The fraud ecosystem also requires the services of specialized individuals and groups. These include runners, droppers, shoppers, and bladder truck managers. Runners often use skimmed ATM data to generate fraudulent credit/debit cards for quick, multiple withdrawals or provide bank accounts or fake (or hijacked) accounts of payment service providers such as Western Union and PayPal, charging exorbitant fees to receive, withdraw, and send monies on behalf of carders (Singh, 2015).
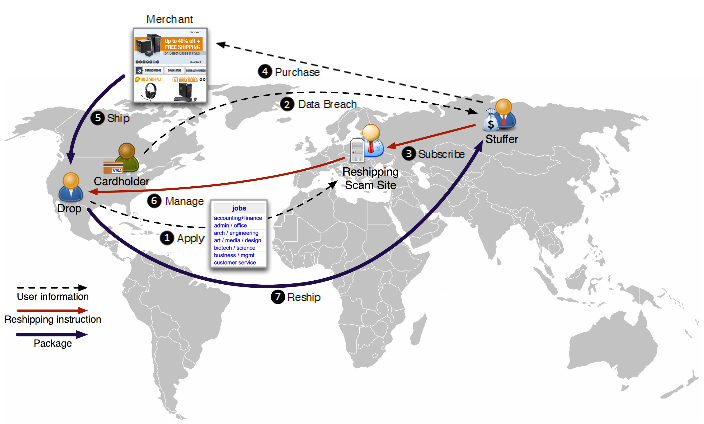
On the other hand, droppers provide actual physical or PO Box addresses to carders to receive purchase goods and facilitate overseas or international shipping for respective carders. Due to the latter, droppers are also referred to as reshipping mules. In fact, droppers are almost exclusively known for this function (Hao et al., 2015).
Figure 16 – Operational anatomy of a standard reshipping scam showing the shopper/mule or dropper applying for a reshipping job (1) through to actual reshipment (7) (Adapted from (Hao et al., 2015))
Shoppers, as the name implies, perform the emotionally grueling task of shopping for goods with the fraudulently acquired card details (Singh, 2015). Sometimes, they also double as reshipping mules.
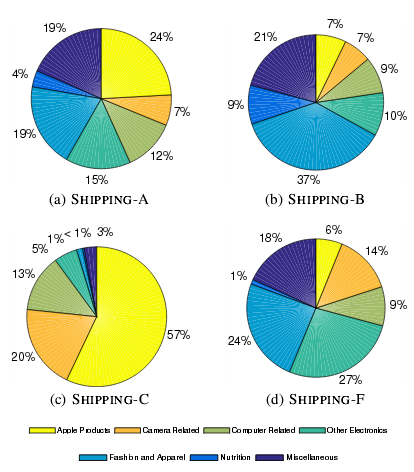
Figure 17 – The proportion of reshipped packages per reshipping scam (Adapted from (Hao et al., 2015))
The titles “SHIPPING A” through to “SHIPPING-F” denote reshipping mules that specialize on different product categories and charge different prices. For instance, SHIPPING-A and SHIPPING-C specialize on luxury items and high-value electronics respectively, but both demand a percentage cut per shipment. SHIPPING-B and SHIPPING-F are reshipping mules that focus on low-priced and medium-priced items respectively, although the former charge a flat fee per reshipped package (Hao et al., 2015).
Naturally, these niche tasks have been packaged into services. Several “white label” services already exist to organize the infrastructure behind reshipping scams for carders. These include LabelCity (Krebs, 2014u), DropForRent.net (Krebs, 2011v), and profsoyuz.biz (Krebs, 2011w). Tellingly, these services reship products mainly to Russia and other Eastern European countries. Indeed, about 85% of reshipped packages are headed for Moscow (Hao et al. 2015).
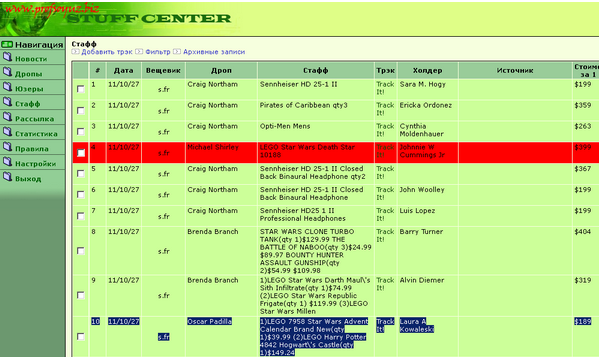
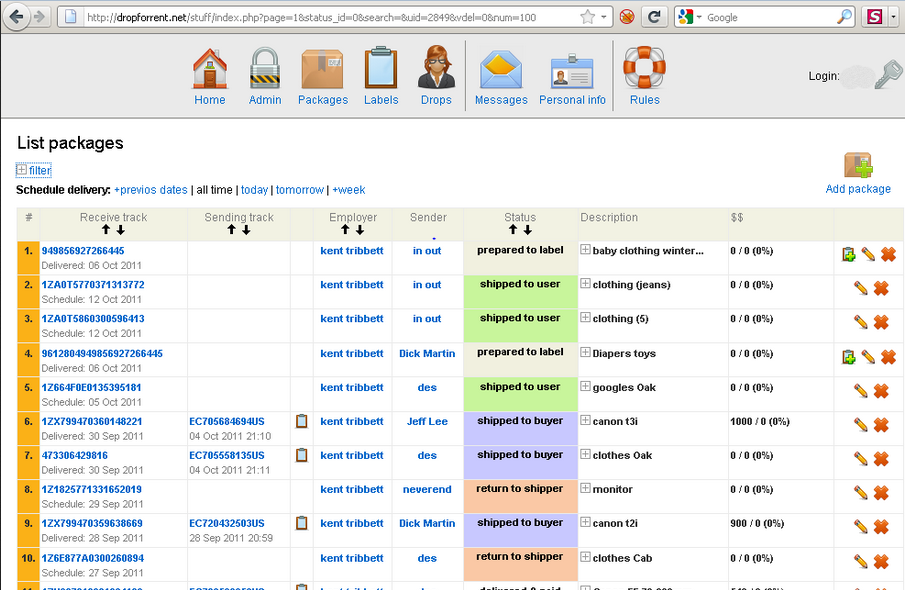
Figure 18 – Administration panel of the reshipping service profsoyuz.biz showing cardholder (“Holder” or “Холдер”), dropper (“Drop” or “Дроп”), and package contents (“Stuff” or “Стафф”) information (Adapted from (Krebs, 2011w))
Figure 19 – Administration panel of the reshipping service Dropforrent.net (Adapted from (Krebs, 2011v))
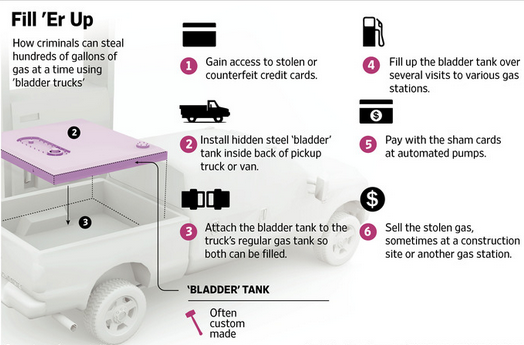
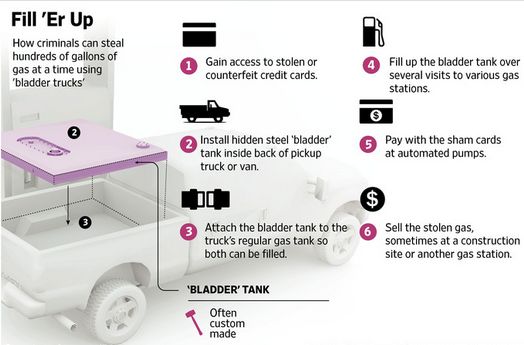
Organized crime syndicates that launder stolen card details obtained from gas pump skimmers offer a unique specialized service. These syndicates use the fraudulently obtained financial information to fill a steel tank in a retrofitted vehicle. These vehicles are referred to as “bladder trucks”. This fuel is then sold to the black market. Fuel-related fraud of this kind costs the payments-card industry $500 million in 2013 alone (Sidel, 2015).
Figure 20 – Illustration of the bladder truck scam (Modified from (Sidel, 2015))
Figure 21 – A van converted into a bladder truck (Adapted from (Krebs, 2015g))
Vulnerabilities in the Credit Card Processing Infrastructure
Magnetic Strip Protocol
The magnetic stripe protocol has demonstrable vulnerabilities including privileged and service attacks. As an attack surface, magstripe protocols utilize encoded data as opposed to encrypted data. Hecker (2016) demonstrated a variety of attack vectors in a recent presentation, expanding on previous research by Kamkar (2015).
EMV Protocol
While the EMV (Europay, Masterard, and Visa) protocol has been hailed as the (relative) gold standard in card security (Krebs, 2016x), several studies have documented vulnerabilities existing in the wild. Despite overwhelming adoption outside the USA with over 1.6 billion EMV cards worldwide, Bond et al. (2014) show that opportunities for exploitation exist. This vulnerability exists in PoS or ATM generation of an “unpredictable number” (nonce) for every transaction. The researchers report terminal flaws and protocol failures that weaken the “predictability” of the nonce, making EMV cards amenable to theft. Murdoch, Drimer, Anderson & Bond (2010) also find opportunities for man-in-the-middle attacks on chip and PIN cards that enable attackers to make payments undetected and without PIN information.
Figure 22 – Terminal supporting dip-the-chip-based EMV card transactions (Adapted from (Krebs, 2016x))
Avoiding Credit Card Theft
Structural Solutions
Regardless of the choice of card technology, it is imperative that the industry pursue stronger cryptographic protocols for card-to-terminal data exchange. The implicit trust that ensures PIN information is optionally encrypted during offline verification is a travesty that needs to be done away with. Tragically, the backwards-compatibility of EMV cards means that PIN information are not necessarily mandatory to complete transaction. This mechanism needs to be rethought to prevent man-in-the-middle attacks (Murdoch, Drimer, Anderson & Bond, 2010). Additionally, the industry must respond to the massive data breaches by requiring operating system upgrades on card-processing terminals such as ATM.
Individual Precautions
The constant deluge of news on data breaches has led to an unanticipated effect: data breach fatigue (Simpson, 2016). While the extent of data breach fatigue remains debatable (Bruemmer, 2016), cardholders need to be ever more proactive in monitoring their card expenditure, updating computer virus protections, and diligently managing passwords and PIN information. Similarly, cardholders can establish different accounts to “air gap” card accounts. For instance, debit cards should not be linked to bank accounts or used to purchase products from un-trusted terminals or vendors. These and other techniques, while incapable of stemming the tide of attacks by themselves, in concert, can alleviate the risk of having card information stolen.
Conclusion
This report has explored the strategies by which attackers obtain card information and the life of this information in the carding ecosystem. It is expected that as more transactions move online, opportunities for identity theft will only escalate and it is imperative that modern-day information security practitioners appreciate the techniques, motivations, and laundering activities of the carding underground. This report has also proposed several typical and not-so-obvious improvements to the card-payment processing infrastructure. Page limitations deny this author the occasion to explore additional high-impact interventions. Hopefully, this report presents a concise examination of the carding ecosystem and will prove invaluable in dismantling it.