Disaster Prevention and Recovery Plan: Order by Narges Askary
Written for Narges Askary. Please be aware of frauds might be committed by Narges Askary or Narges Askaripour. She purchased several papers and after delivery she claims that she did not receive it only to get paid by her bank which is a fraud. We helped Narges to graduate from Central Texas College. We would like to warn all stakeholders including other essay writing companies to be aware of this individual. She currently lives in San Antonio, Texas and holds a government job working as an Intelligent Analyst. She previously worked as a sales assistant for Sunglass Hut at Houston Galleria Mall with her sister. So far she has committed several frauds in total around $2,000.
Email: narges_askary@yahoo.com
Phone number 813 320 7225
Address 5657 Poppy Seed Run, Leon Valley, TX 78238
Below is the paper we produced for her and she fraudulently claims she didn’t receive it:
Memo
To: The CEO, Chain Store
From: Head Manager Security Administrator
Date: April 15, 2021
Subject: Data Stolen by Employee
Findings
I have determined that the virtual private network (VPN) of the organization has been breached, following a discovery that one of the employees in the accounting department named Mr. Johnny stole company data using his company computer. The data was also accessed illegally using company computers. Based on the logs from the intrusion detection system (IDS), the remote access system and file servers, I have fully verified that the breach occurred, and Mr. Johnny is the culprit. The full extent of which kind of information was siphoned out of the facility has not been determined as I will need to personally run a diagnostic on Mr. Johnny’s personal computer. Also, I seem to be facing hurdles because Mr. Johnny has hired an attorney, who has since claimed that Johnny’s laptop cannot be identified in the system.
Tools Used to Address the Issue
I have decided to ramp up our system monitoring and log auditing tools and techniques. For instance, I have suggested to the finance tool to avail funds to buy Naigos, a robust tool that will play a key role identifying suspicious loads on the systems, peaks in the network and resource usage. Naigos is also equipped with a substantial number of plugins, and can be supplemented by my own code to enhance its capabilities. Secondly, I am planning to enforce the use of system firewalls more than before to secure all incoming and outgoing packets in the system. Lastly, I am going to ensure that encryption tools are used across the organization, so that all files are encrypted.
Steps to Prevent Breach in The Future
The major decision that must be enforced to secure the organization from future data breaches is through limiting access to the company’s most valuable data. This will help reduce the number of employees allowed to see sensitive documents, and can help zero down on a specific person in case of a breach. While it has been conducted before, I am suggesting that all employees undergo another rigorous training about cyber awareness, and the consequences of their actions should be caught participating in illegal activities in the company. Lastly, I am in the process of developing a comprehensive cyber breach response plan that will allow the organization and workers to understand potential damages should a breach occur, and limit lost productivity.
April 15, 2021
CITY, COUNTRY – Chain Store can confirm that one of its employees stole company data, which the organization is still assessing to determine the extent of damage caused. Chain Store has since taken swift actions to contain the breach, and is working with internal and external teams to carry out a thorough investigation about the incident, as well as minimize the current IT disruption caused.
While the operation was not sophisticated as earlier expected, the Store has deployed its robust protocols and procedures designed to address such events. Besides, our cyber defenses identified the breach, and quickly detained the party involved to protect user data.
Chain Store media channels, including its app and e-commerce site, remain unaffected and are running well. As said, we are not aware if the breach infiltrated personal data associated with our customers. All our critical systems are secure and functional.
Contacts
Media Relations
Name
Phone
Disaster Prevention and Recovery Plan
The plan under analysis is enforced based on a number of metrics. First, all teams must be involved in the planning process because they must understand the scope of risk and benefits of a successful plan. The plan must also seek to select critical loads, and develop and alternative power source to them. Lastly, the plan must be tested thoroughly to ensure it works as designed.
Recognize, React, Respond: The organization will plant monthly training meetings for all employees about computer security. The organization will deploy incentives to reward workers who abide by security measures. Workers must also involve the IT department in a timely manner in case of a suspected breach.
Computer Room Environment. The computer room at Chain store must be secure from threat such as extreme temperatures, cases of theft, overloaded sockets or bad plumbing. Therefore, the prevention plan seeks to create a secure environment by not arousing unnecessary attention to the organization’s critical infrastructure (Szuba). To this end, the room should have low visibility with minimal signs or no signs at all. The plan seeks to maximize structural protection to the room, as well as minimizing external access with few windows. The facility must also be prepared for fire emergencies with an automatic fire-extinguishing system. Moreover, the plan seeks to maintain reasonable climate in the room with robust air conditioning systems. Lastly, the facility will have guard equipment such as repair materials, protections for cables, outlets from where people walk, as well as keeping record of the equipment in the facility.
Hardware: First, removable media must be treated with care: employees must not insert an untrusted removable device to a computer system in the company. Employees must also submit all untrusted removable media to IT for evaluation. Lastly, autorun must be disabled for all computers in the virtual private network. Other hardware prevention and recovery plans include backing up data t separate disks, site and a secure cloud solution. The backed-up data must be verified to ensure that is it not incorrect, invalid or corrupted. The computer systems must also be equipped with robust firewalls and antivirus. The computer systems and servers must also be protected from power surges.
Connectivity to A Service Provider: Chain Store must ensure that its service provider used a managed security service model, which entails a case where the provider must manage the security parts of the Store’s security components and network. The provider must focus on security from the basis of enterprise. Moreover, providers must ensure endpoint security measures are maintained and identified in the security zones. The model would ensure that the provider uses such processes to secure its own backend, as well as host-based services such as mail and web servers and DNS infrastructure.
Data and Restoration: First, the organization should develop a list of all imminent or probable threats, and present them based on the level of impact to the business. The categorization of the threats would help determine the budget of combating disaster and reduce downtime in case of an attack (“5 Step Action Plan for Data Recovery for Businesses”). The organization must also seek to showcase how the business can ran in case of an attack, prior to developing a robust inventory of IT assets. Lastly, Chain Store must formulate and test a contingency plant that includes data backup and maintenance schedules.
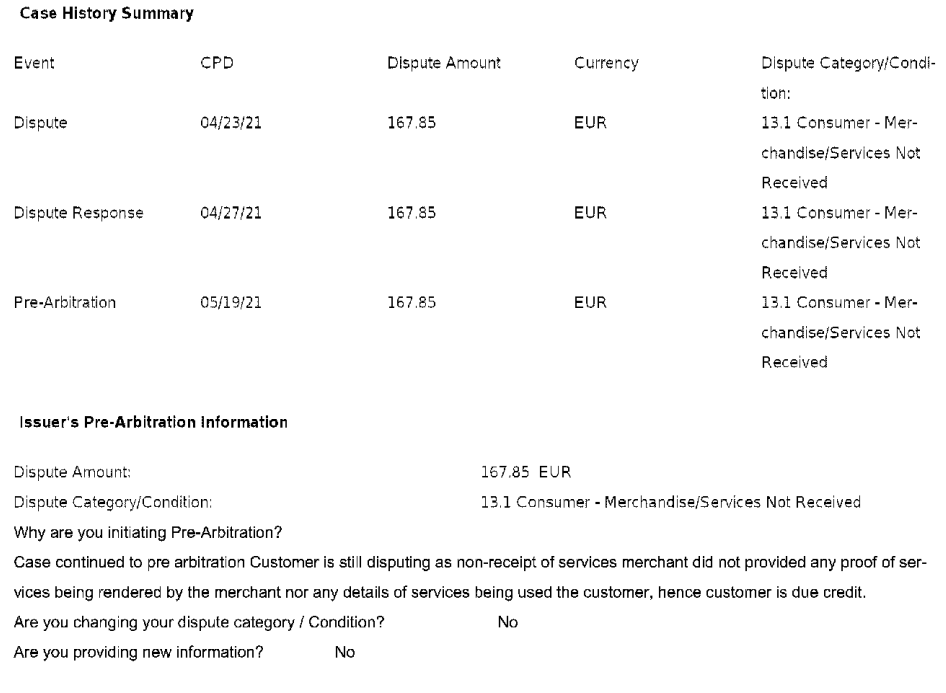
Here are the evidence of Narges Askari Pour fraudulent claims when she received the above essay: