Blockchain Technology in the Healthcare Domain
2 LITERATURE REVIEW
2.1 Introduction
This chapter explores existing information and knowledge available in this research field and critical analysis of the gap. The focus of the literature review is on describing the sharing of confidential information, authentication in decentralized system, blockchain technologies, hashing algorithms, blockchain types and features, and distributed ledger technologies. Based on these descriptions, it would be possible to identify research gaps that need to be filled.
2.2 Sharing Confidential Information
The trends of using the latest technological devices are overgrowing. The confidential data is shared between organizations via a securing messaging system like e-mails or save the data in portable encrypted storage or using centralized systems. Most organizations still use e-mail to share crucial data. When looking from a secure data sharing perspective, many concerns arise, which include:
- Security
- Privacy
- Authentication
- Integrity
Security is a critical issue of concern in all aspects of life. The security risk is more pronounced on the internet, where data is shared faces the risk of being accessed by unauthorized people through hacking.
2.2.1 Sharing Medical Information
When examining the previous studies conducted in sharing medical information, most of the concerns address the following:
- The sensitive and the highly personal information that they possess in the Electronic medical records
- Many patients sometimes take extraordinary measures such as physically carrying the health documents over long distances
- The use of centralized systems characterized by various challenges such as high privacy and security risks, failure, and delayed access to data
The following table presents the current state of sharing data in the healthcare domain and the advantages tied to sharing of data using Blockchain:
Table #: Traditional Healthcare Vs. Blockchain
| Healthcare domain-Current state | Blockchain Advantages |
| Healthcare Data is centralized- only hospitals connected to the system can access the data | Data is distributed between organizations and Stakeholders |
| There is no trust – Data might be changed | Blockchain brings Trust and records are immutable |
| Patients have to do the same test multiple times due to improper data exchange | Time, effort, and money are saved as data is available in one application |
| A patient has no control over his data | A patient has full control and can share his data with any doctors inside or outside the country |
| A patient consumes time and effort to get his medical report | Medical Reports can be accessed immediately from the application and can be shared with any doctors in any hospitals |
2.2.1.1 Methods of Sharing Patient Medical Report
In the UAE, the patients can ask for their medical report using two methods:
- Physically– Going to the hospital to apply for a medical report from the reception and waiting 5- 12 days to receive a hard copy or receiving it via e-mail.
- Smart Portal– Apply to the request using a smart portal that offers a service for providing such documents to patients without going to the medical center receiving the report via e-mail.
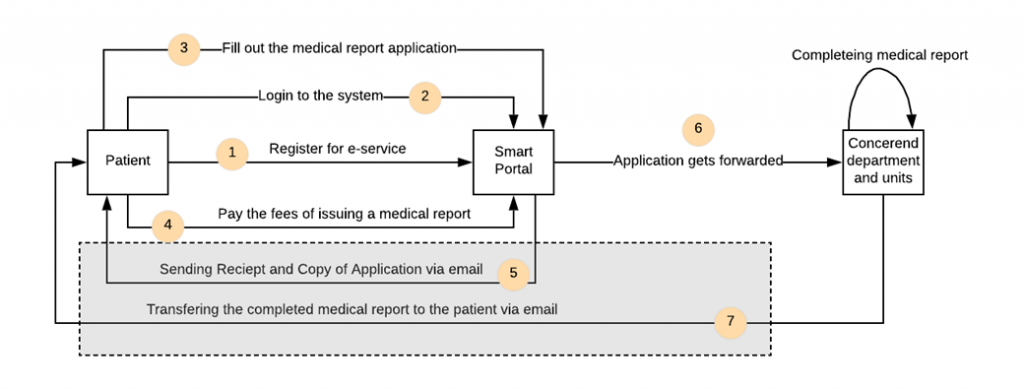
The scenarios provided below explain how the method used to transfer medical reports to patients using a smart portal allows the patient to get the report via e-mail. The concerns on transferring confidential documents through e-mail are that it is not secure and exposes the patients’ privacy by a third party (man-in-the-middle). The following diagram illustrates the procedure and steps to asking for a medical report using a smart portal:
Figure#: Steps of sharing patient’s medical report via smart portal service of the ministry of health and prevention (MOHAP)
Registering an account is essential to allow access to Smart Patient Portal and access the system personally through a personal account. The steps for registration include:
- The user is supposed to utilize the menu at the home page to access My Profile then Register. This leads to the display of the registration form on the screen. The patient portal account can be set up by booking an appointment with the practitioner through a smart online booking or an access link provided by the practitioner. When the user books an appointment with the health practitioner, the system prompts them to create an account.
- Fill the form with the necessary information regarding username, e-mail, password, and confirm password. The username is supposed to be unique, meaning that it will prompt an individual to change it. The e-mail is also supposed to be unique and valid since the link for account confirmation is supposed to be sent there. The password must be strong enough, consisting of at least six characters or numbers or both. The password will always be required every time the user wants to pass the login procedures.
- Once the user accesses the system, fills out the medical report with the required details, and pays the required fee, the receipt and copy of the application should be sent through the mail. Sharing the receipt and copy of the application will involve selecting the document through clicking on the file without opening it or CTRL-click to select many documents. Share the document with the practitioner once it are uploaded into the system.
2.2.1.2 Common Challenges in e-mail
The use of e-mail increases unauthorized persons’ access. One of the risks of file sharing through e-mail attachments is accidental information sharing to the wrong recipient, i.e., human error. Once the e-mail is sent, it is gone, and the sender loses control over it. E-mails are also easily targeted by hackers. According to Mahmoud, Grigoriou, Fuxman, et al. (2019), there has been an increase in the number of hackers targeting e-mail accounts. The problem has worsened because most of these hackers are currently found at an affordable rate and sleuth. The strategies currently being applied to net them are as effective as the evasive strategies they apply.
Furthermore, e-mail allows the transfer of almost any type of data file. Unfortunately, the wide-ranging functionality leaves a vulnerability to malware. The older e-mail programs used to open messages automatically to make it convenient for the user in the past. However, this led to virus infection that did not involve the user, making it highly insecure. The feature was improved in the newer versions of e-mail programs since they could not open the attachments automatically (Haider, 2016). This helps to minimize infections that emanate from the automatic opening of documents. The methods used in hacking the newer e-mail programs involve the hacker enticing the recipient to open the attachments manually. New tactics are being developed daily to entice users into opening malicious programs and unknowingly installing them. Some of the tactics include customized personal messages such as “Dear buddy,” spoofing the sender to make them feel as if they know them, making the message appear friendly, making attached file appear as harmless as possible, and making the message appear threatening: “your account may be compromised unless you follow the attached guidelines…” (Derouet, 2016; & Hughes, Sibert & Steggles, 2001)
The only way that the situation can be improved is by refraining from sending or sharing sensitive files through the mail. More control over the sent files can be attained through uploading the file in the cloud and creating password protection. In this case, the e-mail and password are shared separately, meaning that the sender is likely to realize it when they have sent the mail to the wrong person. It would be unlikely to make the same mistake twice.
2.2.2 Traceability
This refers to the provision of the system to allow one to track the path by which data has gone through. This is essentially helpful in retrieving information of patients.
2.2.3 Trust
When information is keyed into the system, it is expected that it should be to the discretion of the one who is given the custody. When this one is breached, one is liable to the rule of law.
2.3 Authenticity
It is a key aspect in information sharing. The one keyed into the system should be verifiable. If this one is not met then the system is problematic.
2.3.1 Decentralization
Giving ultimate power to one user is sometimes very challenging especially of the workload is something to worry about. To ease this burden, the best way it to allow others have access to information but notably, only through clearance given by the system.
2.3.2 Integrity
The term “integrity” refers to the ability to avoid any alteration of data exchanged between parties as it is being transported from point to point over communication media.
2.4 Blockchain Technology in the healthcare domain
Much research has been conducted on Blockchain and its various uses, especially in this era of improved industrial and technological development. While describing the nature of Blockchain, Aste, Tasca, & Di Matteo (2017) argue that Blockchain technology promotes transactions between two parties without the need for the involvement of a trusted third party. Specifically, Aste and colleagues indicate that Blockchain systems are characterized by various appealing features, including security and interoperability, “Blockchain systems have several appealing features, their power resides in the interoperability, in the absence of vulnerable single point of failure and in the community-based verification process through consensus mechanism” (Aste, Tasca, & Di Matteo, 2017, p. 7). Blockchain has numerous applications and adaptability to the changing technological environment. Agbo, Mahmoud & Eklund (2019) argue that the main benefit of the use of Blockchain is that it eliminates the need for a centralized, trusted third party (TTP) that may malfunction, fail, or be compromised maliciously, making the system insecure. Blockchain is characterized by a decentralized, shared database that possesses the capacity to provide the required transparency and safety of the various transactions. Having been initially utilized for cryptocurrency, Bitcoin, over time, Blockchain use has significantly advanced. It is being adversely utilized for business functions in various platforms such as Etherium and Hyperledger Fabric (Buterin, 2014 & The Linux Foundation Projects, 2020). Transactions are validated by validators (miners) in a decentralized manner. According to Lin & Liao (2017), blockchain technologies are characterized by six key elements: decentralized, transparent, open, automated, immutable, and anonymous.
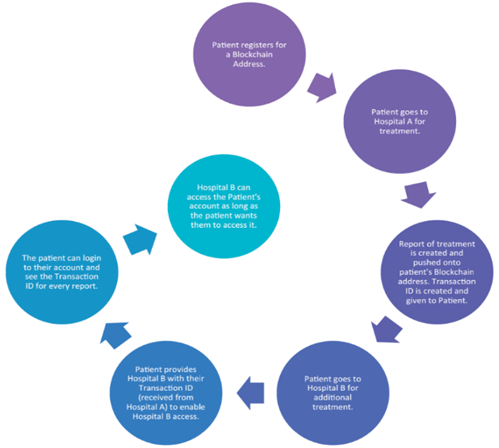
Blockchain has numerous applications, with healthcare being one of the potential sectors likely to benefit. Zhang, Douglas, Schmidt, and White (2018) indicate that the various uses of Blockchain in healthcare include prescription tracking to identify any instances of over-prescription or overdose, data sharing between the modern discoveries in healthcare and traditional care, sharing data and information related to cancer, safekeeping of the personal health records, and management of the digital identity of patients (Siyal, Junejo, Zawish, Ahmed, Khalil, & Soursou, 2019). An example of the utilization of Blockchain in healthcare is illustrated in the below figure.
Figure : Source: Hughes & Morrow, 2019, p. 6.
2.4.1 Satoshi Nakamoto
By definition, blockchain refers to the technology that facilitates the existence of cryptocurrency. In essence, without blockchain technology, cryptocurrency, such as the bitcoin, which was invented by Satoshi Nakamoto, a presumed pseudonymous person or group of individuals who invented the bitcoin, wrote the bitcoin white paper, and developed bitcoins original reference implementation, would not exist. Currently, bitcoin is one of the most popular cryptocurrency, the one for which blockchain was invented. Despite the existence of cryptographic elements, bitcoin took too long to appear in the digital scene. The reason for its awaited appearance resides in the adage “Timing is everything.” By the time bitcoin emerged, the technological environment was perfect for its success.
In essence, the integration of specific DLT features into blockchain offered the necessary environment and time for the improvement of the bitcoin. The first feature of DLT evidence in blockchain technology is the shared database. As a shared database, blockchains are logs of records shared using blocks that form a chain. As such, the blockchain is not linked to a single entity. Rather, it is shared among nodes.
Notably, blockchains are recognized for their implementation of cryptographic signatures. In particular, the blocks, which form a chain, in the blockchain are closed by a hash. The next block commences the same hash, allowing the verification of the encrypted data (He, Qiu, & Sun, 2002). The use of cryptographic signatures enables the creation of immutable and secure storage. Consequently, the data cannot be altered.
2.4.2 Blockchain Concepts
The first notable blockchain concept is permissioned versus permissionless blockchains. Concerning this concept, a blockchain can exist either as permissioned or permissionless (“Bird & Bird & Private Blockchains,” n.d.). A permissioned blockchain, restricted to a group of companies, requires prior approval before use (Kim, Turesson, Laskowski, & Bahreini, 2020). By contrast, permissionless blockchains, such as bitcoin, are public and can be accessed by everyone.
The second concept is blockchain algorithms, referring to conventions through which all participants in blockchain agree on the current state of information. Through such algorithms, the parties trust unknown peers in a distributed environment. Some of the algorithms include voting systems, Proof-of-Work (POW), or Proof-of-Stake (POS). Regarding voting algorithms, the parties vote for their preferred validators to assist in the consensus state of new blocks. When using the POW algorithm, the parties use data from block header as an input and continually run it through the cryptographic hash function.
Another important concept is consensus. Regarding cryptocurrency, a consensus mechanism refers to an approach utilized in computer and blockchain system to attain the required agreement on either a single network state or data value among the distributed processes or nodes. Blockchains deploy global consensus across all the nodes. Unlike the distributed ledger technology, DLT can create an agreement among nodes devoid of having to validate across the whole blockchain.
Cryptography is also an important concept linked to blockchains. Cryptography comprises mechanisms for securing communications by allowing only the sender and the intended recipient to view message contents. As a growing list of records, blockchains are linked using cryptography. Worth noting is that every block comprises a cryptographic hash of the previous block, transaction information, and timestamp.
In general, blockchains might be a catchall phrase, as depicted by many success stories in the previous years. Despite such depictions, it is necessary to consider that the underlying implementation of blockchain is a DLT. Differentiating the DLT and blockchain is important when seeking blockchain technological solutions.
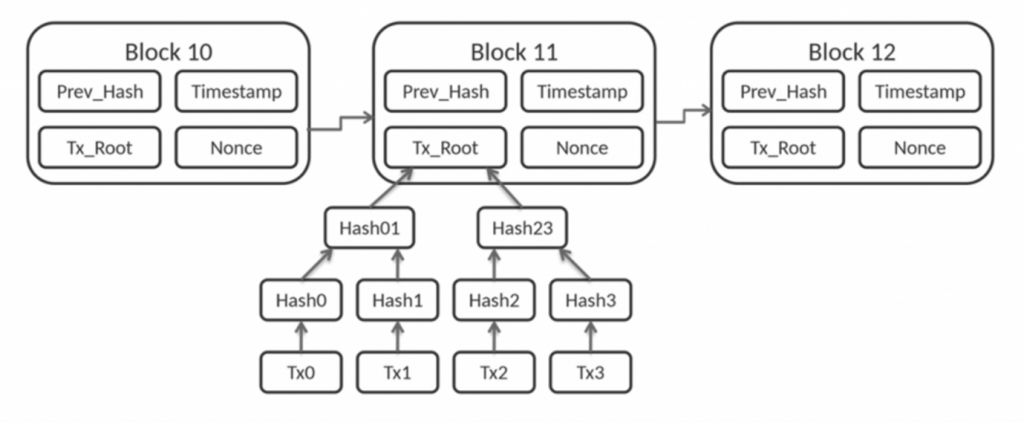
2.5 Merkle Tree
The Merkle or hash tree accounts for a significant success of blockchain technology. In cryptography, Merkle trees encode blockchain data securely. Every node in the Merkle tree is labelled with cryptographic hash. Merkle Trees are a fundamental component of blockchains, underpinning their functionality. In essence, the function of this tree is to allow secure and efficient data structure verification, and potentially boundless data sets in the case of blockchains. The implementation of Merkle trees in Blockchains has multiple effects. In particular, it facilitates blockchains to scale while also facilitating the hash-based architecture ensuring data integrity.
2.5.1 Hashing Algorithm
In algorithms of blockchain, hashing is used to determine the state of the network or information. Blockchains are linked lists that contain data and a hash pointer that points to the previous block, creating a chain of connected blocks, hence the name “blockchain”. By linking blocks of data in this format, each resulting hash of the previous block represents the entire state of the Blockchain. In addition, all of the hashed data of the previous blocks is constituted in one hash. The hash is the fingerprint of the entire transaction happened in the previous block. The below an example of the hash in the blockchain:
2c1b4e44776f22652e9a5b69b25a3558e29714e1649bdfb6c3d33f5611aff627
The hash allows for resolving data integrity issues as well as mapping of the data through the entire Merkle tree
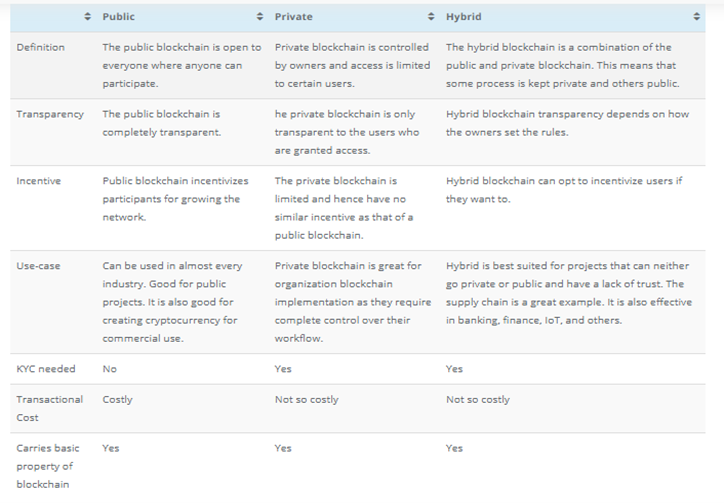
2.6 Blockchain Types
Entities started to implement Blockchain applications for various purposes as cryptocurrency transactions, agreements, identities, data storage, property rights, and data sharing. There are multiple types of blockchain public blockchain, private Blockchain, Hybrid blockchain, and consortium Blockchain. The following sections will explain each type in details:
2.6.1 Public Blockchains
Public blockchains are open networks that allow any participants to join and participate within the Blockchain. When inspecting public blockchains, which are the most widely adopted until now, many security concerns arise if they are to be used for secure data transactions (Lin & Liao, 2017). Most evident of which is the DoS (Denial of service) attack that can be executed by a smart contract application running on this Blockchain, the reason which drove developers to hard-code a cost to the transaction that is to be advertised by the application, this is applicable for cryptocurrency applications where the cost translates to real value, but in private blockchains and non-crypto currency based applications, this cost doesn’t exist, and the need of another method to mitigate the risk of DoS attack is necessary (Wessling, Ehmke, Hesenius, & Gruhn, 2018). Second, the need for confidentiality of the smart contract logic, the ledger state, or the transaction data are necessary to run a secure data transaction platform.
Looking further into the risks surrounding blockchains, eclipse attacks have been discussed in previous research (Heilman, Kendler, Zohar & Goldberg, 2015). This particular method involves masking all of a victim’s connections to the network from several sources, which involves using several IPs for this kind of attack. The scale of the resources needed by the attack highly depends on the size of the network. In a private network, the size is relatively small since these attacks have been studied to scale up to an enormous public blockchain like Bitcoin network. However, to attack such a large blockchain, the resources needed are accessible only to ISPs or governments, but it is still possible. While private blockchains tend to be secured on the nodes participating in the network, but the risks of the public Blockchain should be taken into consideration when designing a private network because an application layer above the Blockchain usually handles the access method and permissions, and the possibility of this layer misbehaving or being attacked must be accounted for.
2.6.2 Private Blockchains
In some circumstances, public blockchains might not be appropriate. For instance, parties in a blockchain network might want more accountability on the management and running of the blockchain. In a public blockchain such needs might not be met since there is no entity in charge of the blockchain. Private blockchain is the blockchain that permits only selected entry of verified participants to join the system. Private blockchain are frequently referred to as permissioned blockchains. In contrast to the public blockchains, where any individual can download the software, create a node, view ledger, and interact with the blockchain, private blockchains are frequently managed and run by a trusted intermediary (Sharma, n.d.). The intermediary in charge of the blockchain controls the type of access rights of each entity. For instance, some entities might be limited to viewing some or all of the data while others might be allowed to submit new transactions for recording on the blockchain. The following are some of the private blockchain features:
Focus on privacy- The restricted access to private blockchains implies that they hold crucial information that cannot be made public. Due to the significance of such information, private blockchains are likely to be hacked. In other words, unauthorized individuals might attempt accessing information without the approval of the trusted intermediary, making private blockchains more prone to hack and data breaches.
High Efficiency- Despite being prone to hacking, private blockchains can be highly effective. The isolated nature of private blockchains implies that the number of entities can be regulated. The granting of different permissions to different entities also increased the efficiency of private blockchains. Due to the high efficiency, private blockchains might by typified by quick transactions compared to public blockchains.
Scalable – Besides being high efficient, private blockchains are also highly scalable. The scalability of private blockchains can be attributed to the placement of accountability on a single entity (McConaghy et al., 2016). The trusted entity can add and delete nodes and services based on the needs of the blockchain.
2.6.3 Hybrid Blockchain
Hybrid blockchain can be described as a blockchain that utilizes both public and private blockchain solutions. In a perfect world, hybrid blockchain would imply freedom and regulated access at the same time. This type of blockchain is differentiated from the rest due to the fact that they are open to every individual while offering features, such as transparency, security, and integrity (Desai, Kantarcioglu, & Kagal, 2019). Naturally, they are entirely customizable and entities can choose who can engage in the blockchain or determine which transactions are made public (Geroni, 2021). Subsequently, hybrid blockchain tries to optimize the benefits of both private and public blockchains while eliminating their drawbacks.
2.6.4 Consortium Bockchain
Blockchain consortium refers to a form of blockchain network in which different organizations maintain and run the system. Nevertheless, it is not public but private. Although it might sound similar to private blockchains, the main different is that it can offer a decentralized structure (Anwar, 2021). A consortium blockchain is comparatively new approach of implementing the Satoshi’s blockchain technology for enterprises. If the public blockchain is accessible to everyone and the permissioned blockchain services one entity, a consortium is a hybrid of the two types although it has more resemblance to the private type of a DLT.
Comparison of Blockchains
Figure 1: Comparison of blockchains
2.7 Blockchain Features
2.7.1 Distributed Ledger Technology (DLT)
A distributed ledger is a decentralized database shared by several participants in which each participant manages and updates a synchronized copy of the data. The distributed ledger allows participants in the network to verify, execute, and record their transactions without relying on an intermediary such as central authority (Sultan, Ruhi, & Lakhani, 2018). The Distributed ledger makes fraud more complex and more complicated for hackers.
2.7.2 Smart contracts
A smart contract is a computer program or transaction protocol designed to automate the execution, control, and documentation of legally valid events and activities following the terms of a contract or agreement (Norta, 2016).
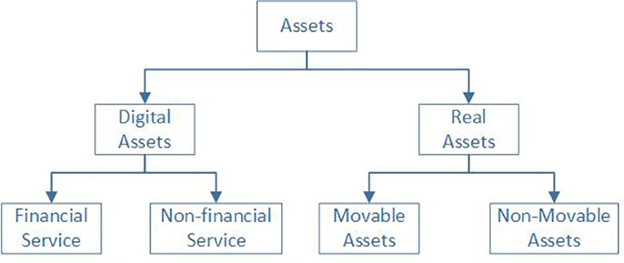
Noteworthy examples of smart contracts include Ethereum and Tron. The Ethereum smart contract can input information and value and change its status and value after entering, as suggested by Buterin (2014). According to Richard (2015), smart contract is computer application running on copiab;e and shared books, and it has the capacity to process, receive and store information while changing its value. Researchers, such as Eze et al. (2017), suggested a smart contract based on the blockchain technology. In particular, the model is decomposed into technical, legal, and business models. To support their model, Eze et al. (2017) divided assets into four groups (See Figure 2).
Figure 2: Asset classification
2.7.3 Consensus
The consensus mechanism is one of the fundamental layers of Blockchain. It validates and update the transactions in the ledger. Consensus protocol reject any bad transactions in the ledger and determines the order of all transactions occur.
Byzantine Fault – Byzantine robots are the robots that show faulty and malicious characteristics that could be used to violate the security either of data stored or in transit by storing the records of the data in a decentralized log (Strobel, Castelló Ferrer, & Dorigo, 2018). The robots working together to provide protection are referred to as a swarm (Strobel, Castelló Ferrer, & Dorigo, 2018)
2.7.4 Peers
A blockchain network constitutes mainly a collection of peer nodes. Fundamentally, peers are crucial the network since they host smart contracts and ledgers (Dickerson, Gazzillo, Herlihy, & Koskinen, 2019). Each of the peers can hold copies of smart contracts and copies of ledgers. Consequently, they are fundamental nodes in a blockchain.
2.7.5 Hash
Each transaction in a blockchain network is linked to a hash. In a block, all the transaction hashes are hashed at least once. The outcome of this hashing process is the Merkel root, which is the hash of all the hashes in the block (Merkle, 1987). With the use of hashes, it is possible to securely validate whether a transaction has been accepted by the network.
2.8 Hyperledger
Hyperledger project is one of the fastest-growing blockchain applications (Hyperledger project, 2016). This open-source project aims at developing an enterprise-grade framework and codebase for distributed ledger technology to be used in the various industries that harness the power of blockchain technology.
In the recent years efforts started to direct towards other kinds of blockchains, most interesting of which and one of the fastest-growing in the Hyperledger project, presented in 2016 (“Hyperledger project”, 2016). This open-source project aims at developing an enterprise-grade framework and codebase for distributed ledger technology to be used in various industries harnessing the power of blockchain technology. This introduced two new kinds of blockchains, Consortium blockchains and private blockchains, opening a new concept of blockchain use cases without the concerns of being open to public access and review like traditional blockchains (Lin & Liao, 2017). The first project to come to light was the hyper ledger fabric project, which was introduced in the same year, 2016 (Cachin, 2016). Like most of the blockchain applications known for requiring smart contracts to be written in certain languages, such as Ethereum network and EVM applications written in Solidity language, the project launched the first platform to make use of the permissioned blockchain approach without dependency on a cryptocurrency (Androulaki et al., 2018; Wood, 2014; Hirai, 2017). Unlike public blockchains, which usually rely on economic incentives to run their consensus algorithms either proof of work (POW) (Nakamoto, 2008) or proof of stake (POS) (Siim, 2017), private blockchains tend to utilize less costly consensus due to the scarcity of participants. The incentive factor is not applicable or needed in an enterprise application or intra-organizational private processes.
Byzantine-fault tolerant (BFT) consensus is used in the hyper ledger fabric, an asynchronous state-machine replication in a fault-tolerant system, which existed well before blockchain and used for enhancing online services availability and resilience (Castro, Liskov, & Massachusetts Institute of Technology, 2003). The following section explains the different types of Hyperledger.
2.8.1 Types of Hyperledger
| POC | |||||
| Brief Description | A modular blockchain client with a permissioned smart contract
interpreter developed in part to the specifications of the Ethereum Virtual Machine (EVM). |
A platform for building distributed ledger solutions with a modular architecture that delivers a high degree of confidentiality, flexibility, resiliency, and scalability. This enables solutions developed with Fabric to be adapted for any industry | A distributed ledger that provides tools, libraries, and reusable components purpose-built for decentralized identity. | A blockchain framework designed to be simple and easy to incorporate into enterprise infrastructure projects. | A modular platform for building, deploying, and running distributed ledgers. Sawtooth features a new type of consensus, proof of elapsed time (PoET) which consumes far fewer resources than proof of work (PoW). |
| Modularity | Modular | Modular | Non-modular | Modular | Modular |
| Smart Contracts | EVM Interpreter | Authored in general-purpose programming languages | Not supported | Not supported | Using transaction families—A smart contract abstraction that enables users to write smart contract logic in the language of their choosing. |
| Access | Permissioned | Permissioned | Permissioned write access only | Permissioned | Permissioned |
| Consensus | Tendermint | Pluggable consensus protocols | RBFT | YAC | PoET |
Table #: Different types of Hyperledger
When inspecting public blockchains, which are the most widely adopted, many security concerns arise. The question is; if they are to be used for secure data transactions or not. The most common security concern is the DoS (Denial of service) attack that can be executed by a smart contract application running on this blockchain. The DoS is the reason that drove developers to hard-code a cost to the transaction that is to be advertised by the application, this is applicable for cryptocurrency applications where the cost translates to real value. Still, in private blockchains and non-crypto currency-based applications, this cost doesn’t exist, and the need for another method to mitigate the risk of DoS attack is necessary. The second security concern is the need for confidentiality of the smart contract logic, the ledger state, or the transaction data necessary to run a secure data transaction platform.
2.8.2 Scalability
The world of technology is fast growing. In the health sector, the e- health data is growing and scalability is a major issue due to data storage on chain which further leads to the centralization of the Blockchain.
The expectations on Blockchain technologies is that it will be the escape route for many organizations as the business environment becomes very dynamic. However, the main obstacle in using blockchain technology is the limited transaction throughput, particularly when comparing them to established solutions, such as distributed database systems. In this paper, we re-architect a modern permissioned blockchain system, referred to as the Hyperledger Fabric. The objective of the re- architecting the Hyperledger Fabric is to increase the transaction throughput from 3000 to 20 000 transactions per second.
The paper concentrates on the performance holdups beyond the consensus mechanism while proposing architectural alterations that decrease computation and input-output overheads during transaction ordering and validation to improve throughput significantly. The optimizations are fully plug‐and‐play not requiring any interface changes to Hyperledger Fabric.
Looking further into the risks surrounding blockchains, eclipse attacks have been discussed in previous research as well (Heilman, Kendler, Zohar, & Goldberg, 2015). This particular method involves masking all of a victim’s connections to the network from several sources, which involves using several IPs for this kind of attack. The scale of the resources needed by the attack highly depends on the size of the network, and in the case of a private network, the size is relatively small since these attacks have been studied to scale up to an enormous public blockchain like Bitcoin network. However, to attack such a large blockchain, the resources needed are accessible only to ISPs or governments, but it is still possible. While private blockchains tend to be secured on the nodes participating in the network the risks of the public Blockchain should be taken into consideration when designing a private network, because an application layer above the Blockchain usually handles the access method and permissions, and the possibility of this layer misbehaving or being attacked must be accounted for.
Since privacy was the first drawback observed since the introduction of Blockchain, some researches and projects were done to address this issue. Despite the Blockchain being anonymous, all the transactions and balances were visible to the whole network. This feature was one of the reasons giving strength and strong credibility to Bitcoin since its launch, but it is considered a disadvantage when using Blockchain for secure and private data. Apart from Bitcoin, the Ethereum smart contracts system doesn’t guarantee this privacy as well, where all the sequence of actions in a smart contract are published and recorded on the Blockchain. One of the first attempts to target the privacy issue was the Zerocash project, which demonstrates a decentralized mix where the link between the transaction and the originating address is decoupled (Sasson, et al., 2014). It significantly addresses the anonymity issue, but it is far from being a true peer-to-peer system. It doesn’t support the transfer of its coins among participants, nevertheless dividing coins to support a custom value for the amount needed to be hidden from the public. The typical application of Zerocash would be executing the transactions on another public blockchain system then passing them through this protocol to add the true anonymity factor using zero knowledge proof to preserve the participants’ balances without a link between the transaction and the user.
The previous example was one of several proposals to address the traceability deficit in the bitcoin blockchain, using the mixing method. However, according Yang (2012) and Maxwell (2013), it stands out from the others as it doesn’t require a trusted third party like the traditional mixing proposals; instead, it uses zero-knowledge proof as described before. However, it still lacks scalability, and with today’s huge public blockchain sizes, this method is inapplicable. This leads us to a more advanced method in security, illustrated in CryptoNote v2.0, which creatively addresses both the traceability and link-ability issues in a scalable manner (Van Saberhagen, 2013). First, by changing the traditional public-private key pairs with a one-time public key generation method to be shared with the sender along with a tracking key generation method to allow the receiver to identify his incoming transactions, both of them do not involve sharing any user-specific public or private information, which makes the user untraceable with regards to his transactions. Second, is using one-time ring signatures in which signatures are done by grouping a set of users, and the user signs the transaction using a key that is unique to his group, not himself (Rivest, Shamir, & Tauman, 2006). The source of the signature can be traced to a certain group but not a specific user of that group. Combining both methods achieves a high level of security in user privacy in which transactions can’t be traced back to the user. Even a set of transactions executed by the same user can’t be linked to each other.
2.9 Blockchain and AI
The literature review has shown that blockchains and AI models have been largely discussed separately by numerous studies. A couple of studies have focused on security issues regarding integrating AI and Blockchain in transmitting information between entities. Polyzos and Fotiou (2017), in their study, highlighted the need for a more resilient, robust, and security guaranteeing system. They argued that individual’s private and sensitive information controlling their everyday aspects of life, such as home security, can be collected through such systems. Zhang, Xue, & Liu (2019) speak to the pertinent challenge of private Blockchain and its applications in addressing confidential and private information. The authors observe that research in data privacy has indicated the vulnerability of leaking privacy owing to the numerous inference attacks linking connecting sensitive information to the intended users’ identity. Equally, Ammanath (2020) alludes that more adequate interventions are needed to use the AI systems to be considered safe from cybersecurity risks associated with harming the users digitally or physically.
2.10 Related Works
This section surveys the related works proposed to secure the data in e-health using blockchain technology. Yue et al. (2016) proposed the first scheme using Blockchain in the healthcare domain that mentioned a healthcare data gateway, the possibility of data sharing on private Blockchain that enables the patients to own their health data without any security violation. Several mechanisms are proposed using blockchain technology, as shown in the table.
Table #: Existing methods using blockchain technology in healthcare
| References | Addressed challenges | Challenges to be solved |
| Azaria A, Ekblaw A, Vieira T, Lippman A. Medrec: Using Blockchain for medical data access and permission management. In: 2016 2nd International Conference on Open and Big Data (OBD). IEEE; 2016. p. 25–30.
|
Access control, interoperability, secure data transfer
|
Data scalability
|
| Shen B, Guo J, Yang Y. MedChain: Efficient Healthcare Data Sharing via Blockchain. Applied Sciences. 2019; 9(6):1207. https://doi.org/10.3390/app9061207
|
Data Sharing, Data Integrity
|
Data privacy, Data scalability
|
| Jiang S, Cao J, Wu H, Yang Y, Ma M, He J. Blochie: a blockchain-based platform for healthcare infor- mation exchange. In: 2018 ieee international conference on smart computing (smartcomp). IEEE; 2018. p. 49–56.
|
Interoperability, Access Control
|
Data Storage and Sharing
|
| Jamil F, Ahmad S, Iqbal N, Kim DH. Towards a Remote Monitoring of Patient Vital Signs Based on IoT- Based Blockchain Integrity Management Platforms in Smart Hospitals. Sensors. 2020; 20(8):2195. https://doi.org/10.3390/s20082195 PMID: 32294989
|
Data Integrity, Global data access
|
Authentication, Interoperability
|
| Dwivedi AD, Srivastava G, Dhar S, Singh R. A decentralized privacy-preserving healthcare blockchain for IoT. Sensors. 2019; 19(2):326. https://doi.org/10.3390/s19020326 PMID: 30650612
|
Data privacy, Data security
|
Interoperability, Data scalability
|
| Wessling, F., Ehmke, C., Hesenius, M., & Gruhn, V. (2018, May). How much blockchain do you need? Towards a concept for building hybrid dapp architectures. In 2018 IEEE/ACM 1st International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB) (pp. 44-47). IEEE.
|
Blockchain architecture | Interoperability |
| Norta, A. (2016, November). Designing a smart-contract application layer for transacting decentralized autonomous organizations. In International Conference on Advances in Computing and Data Sciences (pp. 595-604). Springer, Singapore.
|
Global data access | Interoperability and authentication |
| McConaghy, T., Marques, R., Müller, A., De Jonghe, D., McConaghy, T., McMullen, G., … & Granzotto, A. (2016). Bigchaindb: A scalable blockchain database. White Paper, BigChainDB. https://gamma.bigchaindb.com/whitepaper/bigchaindb-whitepaper.pdf
|
Data integrity | Data scalability |
Electronic Health Records
Electronic health records (EHR) sharing systems are the most highly demanded blockchains after crypto currencies. The present methods utilized by healthcare systems, electronic or not, have so limitations that need to be solved. Blockchain technology presents a good solution to these limitations. Medical records of patients are distributed among different entities from one healthcare to another.
The control of the patient over shared data is nil and at the same time there is no guarantee for the authenticity of that data. One of the solutions offered by the blockchain technology is MedRec, which utilizes the existing data storage methods, and applying Ethereum smart contracts to govern the relations between patients and providers, giving the necessary permissions for viewing or appending the patient’s records (Ekblaw et al., 2016). In addition, within this Blockchain lies all the transactions associated with the records without storing any data on this it. Rather, it timestamps and logs for the data being transferred between different databases. The system relies on existing storages of medical records under the custody of different organizations. The organization controls the access and sharing of the records inside these databases addressing not the security of any of these providers’ databases.
However, data authorization and changes in history is stored in the Blockchain. No single point of failure as all the participating nodes hold a copy of the full ledger. Regarding privacy, where the participating identities are hidden there is still a set of transactions that can be related to the same source, through the analysis of the network traffic this data can be revealed, but as mentioned before this is a major drawback that can be addressed by methods of anonymity that were previously used in crypto currency applications.
There are some security concerns in the nature of the solution. The application will retrieve pointers to the data in the requested database, and though the Blockchain is private it gives access to a remote database that can be strongly argued from the security point of view.
Even through API requests or query access, whatever the method, it will limit the application from being used in a trustless network, or even a trustful network containing data of high confidentiality nature. On the other hand, it is notable that the system does not offer a solution for sharing large amounts of data, in a fast manner by splitting the data layer, permission layer, and the transaction log records layer, which in terms bypasses the blockchain speed limitations when handling large data.
When examining the previous studies conducted in the blockchain security area, most of the concerns are addressing two issues, the possibility of external attacks and updating the ledger records with fake entries, or possibility of network forks in which case the network nodes are split into two different chains resulting in two different versions of the data and practically consensus is lost. Research by Iuon-Chang Lin and Tzu-Chun Liao discusses blockchain technology and the security issues associated with it, mentioning the two previous problems and other speed concerns when comparing to traditional online credit card transactions (Van Saberhagen, 2013). This approach is useful when looking at Blockchain from a financial perspective to replace the conventional financial system, a good approach given the popularity of cryptocurrencies is being the most widely adopted Blockchain application. However, when looking from a secure data sharing perspective, other concerns arise: security permissions for accessing data, transaction records being visible to the network, and the network itself is public.
2.10.1 Past Studies
In recent years efforts started to direct towards other kinds of blockchains, most interesting of which moreover, one of the fastest-growing is the Hyperledger project, presented in 2016 (Androulaki et al., 2018). This open source project aims at developing an enterprise-grade framework and codebase for distributed ledger technology to be used in various industries harnessing the power of blockchain technology. This introduced two new kinds of blockchains, Consortium Blockchains and private blockchains, opening a new concept of blockchain, use cases without the concerns of being open to public access and review like traditional blockchains (Cachin, 2016). The first project to come to light was the Hyperledger fabric project, which was introduced in the same year, 2016, launching the first platform to make use of the permission blockchain approach, and most importantly that it is without dependency on a cryptocurrency like most of the blockchain applications known which require smart contracts to be written in specific languages, such as Ethereum network (Siim, 2017) and EVM applications written in Solidity language (Siim, 2017; Hirai 2017). Unlike public blockchains, which usually rely on economic incentives to run their consensus algorithms either proof of work (POW) (Nakamoto, 2008) or proof of stake (POS) (Heilman, Kendler, Zohar, & Goldberg, 2015), private blockchains tend to utilize less costly consensus due to the scarcity of private participants. In the Hyperledger fabric, Byzantine-fault tolerant (BFT) consensus is used, which is an asynchronous state-machine replication in a fault-tolerant system, which existed well before Blockchain and used for enhancing online services availability and resilience (Sasson et al., 2014; Gorenflo, Lee, Golab, & Keshav, 2020).
When inspecting public blockchains, which are the most widely adopted until now, many security concerns arise if they are to be used for secure data transactions. Most evident of which is the DoS (Denial of service) attack that can be executed by a smart contract application running on this Blockchain, is the reason which drove developers to hard-code a cost to the transaction that is to be advertised by the application, this is applicable for cryptocurrency applications where the cost translates to real value. Still, in private blockchains and non-crypto currency-based applications, this cost doesn’t exist, and the need for another method to mitigate the risk of DoS attack is necessary. Second, the need for confidentiality of the smart contract logic, the ledger state, or the transaction data are necessary to run a secure data transaction platform.
Looking further into the risks surrounding blockchains, eclipse attacks have been discussed in previous research as well (Yang, 2012). This particular method involves masking all of a victim’s connections to the network from several sources, which involves using several IPs for this kind of attack. The scale of the resources needed by the attack highly depends on the size of the network. In a private network, the size is relatively small since these attacks have been studied to scale up to an enormous public blockchain like Bitcoin network. However, to attack such a large blockchain, the resources needed are accessible only to ISPs or governments, but it is still possible. While private blockchains tend to be secured on the nodes participating in the network, but the risks of the public Blockchain should be taken into consideration when designing a private network because an application layer above the Blockchain usually handles the access method and permissions, and the possibility of this layer misbehaving or being attacked must be accounted for.
Since privacy was the first drawback observed since the Blockchain introduction, some research and projects were done to address this issue. Despite the Blockchain being anonymous, however, all the transactions and balances were visible to the whole network, this feature was one of the reasons giving strength and strong credibility to Bitcoin since its launch, but it is considered a disadvantage when using Blockchain for secure and private data. Apart from Bitcoin, the Ethereum smart contracts system doesn’t guarantee this privacy as well, where all the sequence of actions in a smart contract are published and recorded on the Blockchain. One of the first attempts to target the privacy issue was Zerocash project, which demonstrates a decentralized mix where the link between the transaction and the originating address is decoupled, significantly addressing the anonymity issue. However, the Zerocash project is far away from being a true peer-to-peer system since it does not support the transfer of its coins among participants, nevertheless dividing coins to support a custom value for the amount needed to be hidden from the public (Maxwell, 2013). So, the typical application of Zerocash would be executing the transactions on another public blockchain system then passing them through this protocol to add the true anonymity factor using zero-knowledge proof to preserve the balances of the participants without a link between the transaction and the user.
The previous example was one of several proposals to address the traceability deficit in the bitcoin blockchain, using the mixing method. However, it stands out from the others as it does not require a trusted third party like the traditional mixing proposals (Van Saberhagen, 2013; Van Manen, 2014); instead, it uses zero-knowledge proof as described before. Nonetheless, it still lacks scalability, and with today’s substantial public blockchain sizes, this method is inapplicable. This leads us to a more advanced method in security, illustrated in CryptoNotev2.0, which creatively addresses both the traceability and link-ability issues in a scalable manner (Moustakas, 1994). First, by changing the traditional public-private vital pairs with a one-time public key generation method to be shared with the sender along with a tracking key generation method to allow the receiver to identify his incoming transactions, both of them do not involve sharing any user-specific public or private information, which makes the user untraceable with regards to his transactions. Second, using one-time ring signatures in which signatures is done by grouping a set of users, and the user signs the transaction using a unique key to his group, not himself. Hence, the source of the signature can be traced to a particular group but not a specific user of that group. Combining both methods achieves a high level of security in user privacy in which transactions can’t be traced back to the user, and even a set of transactions executed by the same user can’t be linked to each other.
2.10.2 Research Gaps
The most researched blockchain application and probably the soonest to be adopted after cryptocurrencies are electronic health records (EHR) sharing systems. The current methods used by any healthcare systems, electronic or not, have so many gaps that need to be filled, and the blockchain technology can offer an excellent solution to these gaps. Patient medical records are distributed among different entities varying between hospitals, service providers, clinics etc. There is no control from the patient side over the data being stored or shared between entities; at the same time, there is no guarantee for the authenticity of the data and the exhausting process of transferring the medical record or part of it from one organization to another. One of the solutions offered by the blockchain technology is MedRec utilizing the existing data storage methods, and applying Ethereum smart contracts to govern the relations between patients and providers (Feng, Yu, Chai, & Liu, 2019). This solution gives the necessary permissions for viewing or appending the patient’s records besides the private blockchain running between the participating organizations, within this Blockchain lies all the transactions associated with the records without storing any data on this Blockchain, but rather just the timestamps and logs for the data being transferred between different databases. The system relies on existing databases of medical records under the governance of different organizations and controls the access and sharing of the records inside these databases. It does not address the security of any of these providers’ databases. However, the authorization data and change history is stored in the Blockchain. With no single point of failure, all the participating nodes hold a copy of the full ledger. Another issue is regarding privacy, where the participating identities are hidden, but still, a set of transactions can be related to the same source; through the analysis of the network traffic this data can be revealed, but as mentioned before this drawback can be addressed by methods of anonymity that were previously used in cryptocurrency applications. The nature of the solution also have some security concerns. The application will retrieve pointers to the data in the requested database. Though the Blockchain is private, giving access to a remote database can be strongly argued from the security perspective. Even through query access or API requests, whatever the method of data retrieval may be, this method will limit the application from being used in a trustless network or even a trusted network containing data of high confidentiality nature. On the other hand, the system offers a solution for sharing large amounts of data, in a fast manner by splitting the data layer, permission layer, and the transaction log records layer, which bypasses the blockchain speed limitations when handling large data.
2.11 Conclusion
Blockchain technologies have been widely studied despite being one of the recent technological innovations. However, research gaps concerning their implementation in hyperledger still exist. This study identified an opportunity to contribute to the security of data between participants. Previous studies have mainly explored the sharing of confidential information, authenticity in decentralized systems, blockchain concepts and types, blockchain features, and distributed ledger technologies.