ABSTRACT
Enterprise Infrastructure Convergence: Path to Cloud Computing Cost Optimization and Management
Dependency on IT has proved to be advanced in the Modern World than before due to increased dependency and reliance on IT. Moreover, for us to ensure that there is safety, it is important that data protection be upheld as well as ensures that maintenance of IT infrastructure is done regularly at a low budget cost. However, despite the efforts to combat these challenges sustainably, the complexity of the data centers continues to compound management of data. Several data centers today are suffering from issues on multiple fronts that include; lack of adoption and implementation plans, poor financial resource management that has become a major constraint in handling massive data. As a result, Organizations head up to dissolve already established data centers due to advancement in technology that occurs because of economic pressures. Additionally, organizations strive to acquire new enterprises as a way of influencing customer demands within a short period. This leads to increased desire to change the design and manner in which data centers are being managed. Our project takes up the opportunity identify the probable solution for the integration of different components in a manageable manner through exhaustive analysis. Our results demonstrate that, Converged infrastructure is a well-suited approach to data center management. This is because data centers have become retrogressive, outdated and requires new approach to the management. Converged infrastructure methodology that formed enabling modular architecture promises to minimize the compatibility issues. Examination and investigation of the path to converged enterprise level development of IT infrastructure that allows modular architecture for Cloud Computing were conducted. The results that will be derived from this research study promises to establish a basis for optimal approach/embrace of the converged infrastructure methodology. This is by either newly adopting it, or transforming from the current platform to a CI environment.
Cloud Computing model has infinite potential to offer significant performance about Response time and Costing. The exploration of the management complexities in multitier IT infrastructure was done by evaluating Cost optimization techniques. Thus, the cost of Cloud services per labor consumption was analyzed in comparison to data centers for customer adoption of converged infrastructure. The resulting outcome is a workable framework derived from IT companies who aim at incorporating modular architecture into their IT environments. To have future references, a strategy will be formulated as a guided reference for the organization as well. The guideline provides all the aspects that could cause challenges during the consolidation of IT.
Chapter 1. INTRODUCTION
1.1 Overview
‘Converged Infrastructure’ refers to an initiative aimed at bringing together a multiple number of technological advancements in IT into a single unit of optimized computing package. These components include servers, networking equipment’s, data storage devices and software used under management of IT infrastructure for automation and transposition. This converged infrastructure could appeal to data centers that are under pressure to bringing their applications composed rather than incurring a tremendous amount of money in IT costs. It is challenging to have hardware components to meet higher user demand and excellent levels of multi-tenancy and advanced resource controls (Georgakilas et al., 2012). These are the reasons why companies opt for converged infrastructure and “Cloud Computing” as the most efficient and possibly suitable solutions. IT industries take advantage of Converged infrastructure to centralize the management of IT resources, and have efficient utilization of resource at minimal costs, by précised resource utilization through ROI calculation. “Cloud Computing” in a straightforward and sensible way is a new evolution of IT service industry, where all business applications are moving to the cloud. The traditional business world turns towards ‘Cloud Computing”; considering that the amount and variety of hardware and software used in data centers are daunting. This is because of the fact that it requires the entire expert team to install, configure, test, run, secure and update, thus remains very complicated and expensive. With the support of Cloud Computing, these problems can be eliminated as they are freed up from having and maintaining software and hardware. This is because it serves as a utility, where organizations have to pay for what they need; hence, upgrades are done automatically. Cloud Computing is not a new technology or methodology. Leonard Kleinrock, a scientists of what was previously “Advanced Research Projects Agency Network (ARPANET)” project in 1969 said that during that time, the use of computers was still something that was at its infancy. However, as growth is being realized over the years, the IT infrastructure continues to become sophisticated. This means that spread of “computer utilities” will be the order of the day in computing IT field. This is comparable to the advancement in electric and telephone utilities, where the service has been widespread in personal places of residence and places of work across the country. This therefore, means that in the twenty first century, services utilized in computing are predicted to be available based on demand just like any utility available in the society. This is particularly based on service provision model that is anticipated to cause enormous levels of transformation in the computing industry. Consumers have to invest no longer heavily or stopover on constructing and maintaining the data (Georgakilas et al., 2012).
Out of the numerous benefits, one of the reasons for having demanded by the IT sector is fast problem resolution, speed delivery of services, localized service and much more. This is accessible remotely, through either Internet or Intranet connections. Cloud Computing enhances existing data center infrastructure through modular architecture and enables better support for converged infrastructure. As a result, organizations are moving to Cloud Computing for various reasons. These reasons include; cost reduction, fast provision of new applications and services, and aiding the achievement of their specific business objectives. This is because; it can deploy new services without lengthy and expensive applications. This makes it one of the biggest business benefits, therefore, shifting the focus to making improvements in their core business (Harris, 2010).
It is important to take into consideration what IDC, a market research firm, that the enterprise executives such as chief financial officers (CFO) hold the key to unlocking the next innovative phase of cloud computing. This is because its adoption serves as a promising strategic differentiator instead of serving as a means to cost reduction. Therefore, Cloud Computing remains an accurate and effective solution for data handling (Congdon and ProCurve, 2010). Large and trusted technology companies that provide Cloud services are demonstrated as shown in table 1 below:
Table 1: List of large and trusted technology companies that offer cloud services
| Cloud Service Provider | Cloud Storage Solution |
| Amazon | Amazon EC2 |
| Apple | iDisk, iCloud |
| Dropbox Inc., | Dropbox |
| Good | Google Docs, Google Apps, GDrive |
1.2 Problem Statement
Data center was one of the most important aspects of our lives formerly. However, today, data centers continue to face problem and challenges on multiple fronts. This is because of lack of strategies for adoption and addressing of issues related with resource/financial allocation in handling huge data. Because of these constraints, IT teams are under pressure to ensure that they fast track the process of deployment and improvement of organizational performance. This is said to be achieved through appropriate utilization of resources thus reducing costs (Kannan et al., 2012). A solution should be derived to enable ubiquitous, convenient and quick responsive network access on-demand to share pool of configurable computing and identifying the advantages and the disadvantages from the perspective of both finances and IT. Converged infrastructure remains as a promising solution to the problems facing IT organizations. Examination of the path and investigated the development of converged enterprise level IT infrastructure. The best way to approach Converged infrastructure methodology will be to adopt Cloud Computing or by shifting an existing platform to a CI environment in multitier IT. Additionally, identify strength, weakness, opportunities and threats for the Converged infrastructure. The solutions that will be obtained will inform the process of formulation of a set of recommendations for converging infrastructure models with the support and steering leadership of IT managers. The hypothesis of this research study will be accomplished through the appropriate restructuring of the future of data centers. This involves shifting an existing platform to Cloud computing through a simplified modular architecture. The most suitable and effective strategy in Converged infrastructure is achieved through deployments in IT multitier. This leads to reduced cost of design manipulation during the process of managing complexities thus making the management process simple during the shift between converged solutions.
1.2.1 Hypothesis
H1) the concept of Converged infrastructure is quickly transforming the future of datacenters
H2) the phenomenon of Modular architecture serves as a means through transfer of companies towards adopting the use of cloud computing is simplified
H3) the most optimal and efficient deployments are in multitier IT infrastructures
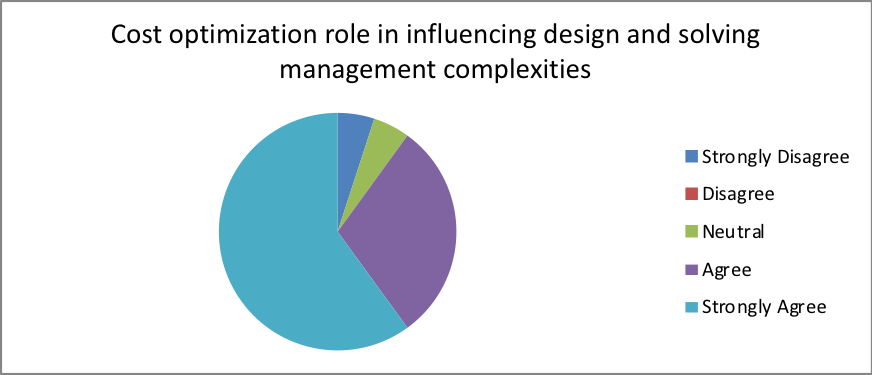
H4) the concept of cost optimization plays a key role in dictating the direction that management complexities take
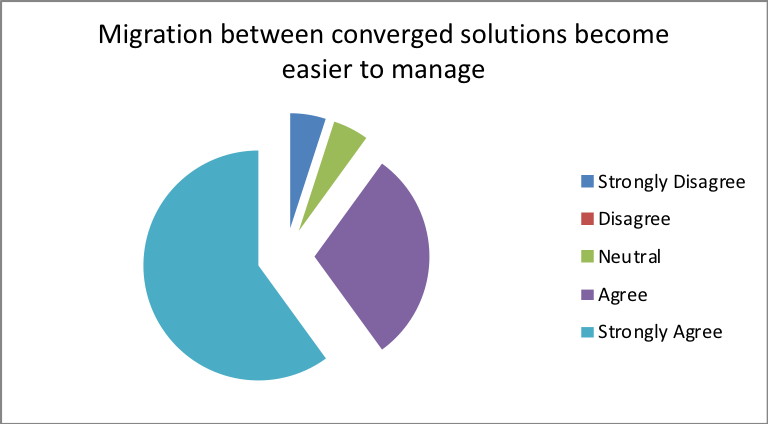
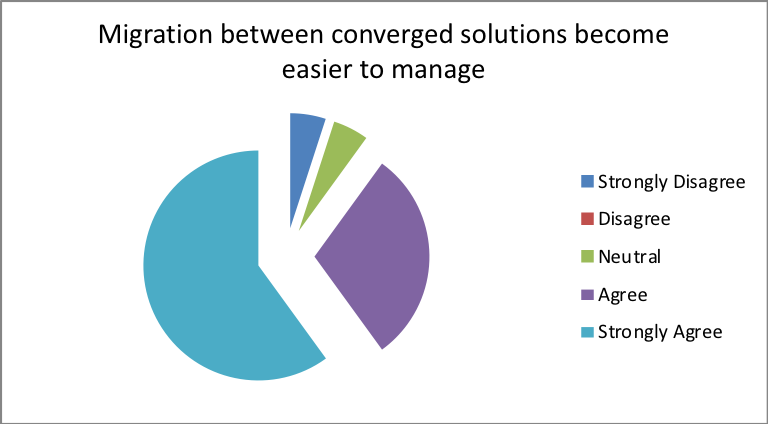
H5) through the adoption of Converged infrastructure, data migrations between converged solutions are easier to manage
1.3 Approach
Examination and investigation of the pathway and the development on converged enterprise level IT infrastructure, permits modular architecture to take on the role of Cloud Computing. Heedful study will be conducted to understand the risks of data breaches in this new approach. Additional research will be carried out with reference to technology and business related issue that is contiguous to Cloud Computing. A stud will be conducted to provide a point of comparison with the current study results that have been reported along with the case studies that will be conducted in the future. This is in order to confirm the study results. Exploration of management complexities in multitier IT infrastructure is achieved through evaluation of Cost optimization. Risk management process encompasses the possible roadblocks that often threaten validity of the study results. These include;
- Lack of data because of security issues in the organizations where the study was conducted. This problem is possibly solved through a data shift to a different GCC country such as UAE
- Problems associated with Internet connection.
- Inadequacy of the required resources utilized in affirming the results of the framework. This is important in carrying out comparison with the results obtained in another IT rich environment.
In this paper, a structured survey/ questionnaire relevant to Converged infrastructure was presented. This was to understand the potential problem faced by the organization, their need for migration and benefit achieved through adoption of Cloud Computing. The responses that were obtained from participant IT companies through their employees helped the researcher obtain viable and reliable information about Converged infrastructure. The results obtained from this research study will serve as a benchmark framework through which other researchers will base converged infrastructure methodologies. This is either through first time appreciation or through shifting an existing platform to a CI environment. The project progression was evaluated regularly to ascertain the quality and validity of the outcome. Additionally, quality assurance of the whole research process was assessed to ensure that the results drawn from the research meets the requirements for quality project deliverables. This ensured that the set standards of the research was fulfilled hence paving way for improvements where necessary. This also ensured that the appropriate corrective action measures are put in place to rectify the problems that could arise in the implementation period. Additionally, this can be achieved through conducting quality audits that ensures the research processes followed the stipulated set of procedures. Moreover, regular consultations with the research supervisor, sponsor among other important stakeholders in the study was done to ensure that all the entities important in the research were up to date with the research activities and findings throughout the period of the study.
1.4 Outcome
The derived solution after exhaustive analysis and data study will be an alternative solution prepared to smartly handle modern data center demands. This will be a practical kind of platform used by IT companies. The main objective of these companies is to adopt the modular architecture into their IT environments. Additionally, a proposal to develop a terms of reference for the companies and enterprises offers a great avenue through which all the aspects causes challenges are removed. This is important during the consolidation of IT and set of recommendations for the organization to provide and manage this upgraded technology for converging infrastructure models, process and procedures (guidelines and partial frameworks).
The execution of the modular architecture should not distract functionalities and capabilities existing in the current model, and will remain as a security for the existing technologies. Deployment of Cloud Computing played a significant role to;
- Offer a visible control over data center applications.
- Manage lop-sided traffic flows during transaction between devices and data center.
- Integrate security and compliance challenges through the network.
Figure 1: Demonstration of cloud computing infrastructure
Chapter 2. BACKGROUND AND REVIEW OF LITERATURE
2.1 Background
Based on the study that was conducted by Groben, Leek and Smith (2010), the organization reserving over 10 of its overall project budget for training reasons, it is rated at over 80% chance success upon implementation. Additionally, in a situation where the organization manages to align its system with its goals and objectives, the success rate is likely to increase (Park, & Young, 2009). In this case, the Enterprise Project (ERP) implementation cost often is estimated to hit over million targets. However, in an ideal situation, adequate time and resource allocation is effective for each project task. Despite the presence of the ideal, in reality, the budget-overruns are similar to those recorded by ERP projects. Because of these short-comings, “user’ training serves as a primary factor that plays a key role in paving way for development and testing (Cramer, 2010).
The return on investment (ROI) as reported by the ERP systems among other IT systems, have been considered a delicate matter for quite a very long time. Based on several previous researches that have been conducted, there is clarity that researchers have demonstrated concerned over the utilization of ROI in training fields. This is because of the fact that allocation of monetary value to subjective benefits is difficult (Esteves, Pastor & Casanovas, 2002). However, it is important to note that it is a challenge for one to attempt to quantify and accord a fiscal value to the returns achieved from training. Comparing the returns from training with the original training costs is always impossible.
According to a report by Lockyer (2014), the recession that hit the Unites States in 2008 resulted into a slow economic growth due to the collapse in financial institutions that served as great pillars to the country. Due to the heavy devastation that the recession brought, most business organizations opted for means through which they could enhance their efficiency while cutting down on costs. IT budgets were required to ensure that there is reduced cost. However, the streamlining of these IT operations while ensuring the competitiveness of the business was a great challenge. Unlike the past when the organizations would piece together their data centers and networks, scaling up in this case meant putting together legacy instruments without necessarily carrying out an evaluation of the system. Because of this, an infrastructure that met the needs of clients was developed but this was accompanied by great complexity associated with the maintenance. This therefore, served as a wakeup call for organizations thus leading to the emergence of converged infrastructure courtesy of collaborative relationship between Cisco, VMware and EMC (2009).
2.2 Literature review
2.2.1 Converged infrastructure
Bernard (2014) argues that with the increased growth and expansion of various approaches employed in converged systems, there are different categories that these methodologies employ; integrated infrastructure system, integrated stack system and integrated reference architectures. Integrated stacks systems represents applications that include servers, storage and network hardware. This promotes the functionality of the converged system. Integrated infrastructures are representative of the computing system that carries out pre-processing activities such as VCE Vblock systems. Integrated reference architecture refers to a set of parts that play a role in allowing the user to make configurations choices from a list of optional commands to select (Batchellor and Gerstel, 2006).
Each of the approaches as mentioned earlier has its strengths, but the most advantageous one is a truly converged system that is termed an integrated infrastructure. A single unit management characterizes this kind of infrastructure while meeting the IT needs of the organization (Bernard, 2014). Once all these guidelines have been satisfied, customers enjoy the full benefits of a converged system as discussed below.
2.2.2 Top Benefits of Converged Infrastructure
With the increasing demand on IT organizations, the organizations’ management often place a high value the factors that will enhance the objectives of the business. This is achieved through scalability, service delivery and adoption of new services. All these activities have to be done with less capital expenditure incurred during operations. This, therefore, is the essence of converged infrastructure (Buyya, Broberg and Goscinski, 2010).
Mikkilineni and Sarathy (2009) stated that Converged infrastructure makes infrastructure management simple. This is because the primary role of converged infrastructure is to centralize the management of server, network, and storage. As a result, day-to-day maintenance that entails less personnel, less training while equating with preceding data centers is made possible. Secondly, CI reduces cost. This is because it leads to shifting to a single-use console that is characterized by a single point-of-contact and only a few components to be managed and troubleshot. This causes an overall reduction in the data center footprint. Laterally, while reducing data center costs, it also eases the cost financed on the individual vendors, streamlined maintenance and reduces storage costs. Expenses spent on overall IT resources and general cross-trainings over the enterprises are reduced.
The principal objective of adopting converged infrastructure is to boost efficiency and speed. This is because it can reduce virtualization and production time from a three-week provisioning time to less than an hour. Additionally, CI is characterized by flexibility and elasticity (Bingham, Strauss, and Edwards, 2003). This is perhaps the most significant benefit of converged infrastructure because it has control in one distinct place and manages multiple functions and devices across. Entire data capacity can be accustomed quickly and can in line the upcoming demand from the user base during converging infrastructure. CI increases agility by virtualizing IP and fiber channel storage networking (primarily used to connect computer data storage); consolidating overall components into a single console management (Jiang and DeSanti, 2008).
2.2.3 Reason for IT shifts to Converged Infrastructure
Several factors have contributed towards the marked shift of IT towards converged infrastructure framework in business organizations. These factors include; Cost efficiency towards maintenance and IT Staff. This is because modern application gets the pool of resources like Virtualized server, storage, and network capacity; under a single console. This makes it faster and much less expensive than the traditional architectures. By having a centralized management, daily maintenance takes considerably less time (Lockyer, 2014).
Secondly, there are operational improvements that are strategic that has ensured the benefits of agility, flexibility by reducing problems and increases performance. The realistic/ Structured approach will be put in place during implementation process (Linthicum, 2009).
Thirdly, Buyya, Yeo and Venugopal (2008) argue that security and disaster recovery characterize the shift. This serves as a way that protects organization data and operations regardless of their location. Prioritization provided on the value of the business processes and initiatives aim towards disaster recovery.
2.2.4 Converged Infrastructure and Cloud Computing
Figure 2: Demonstration of different forms of cloud models
Converged infrastructure plays a critical role in facilitating platforms for private and public Cloud Computing service. These services include; IaaS (Infrastructure as a service), PaaS (Platform as a service), and SaaS (Software as a Service). These features make converged infrastructure well suited to cloud deployments. It can be availed as the below-mentioned clouds; but the decision has whether to implement Private or Public Cloud or Hybrid Cloud mix has to be made (Armbrust et al., 2012).
- Private – Delivered from a business data center to internal users that offer versatility and convenience. It preserves management, control and security (Zhang, Cheng, and Boutaba, 2010).
- Public or Hybrid – Delivers the cloud services over the internet. It is sold on-demand, charges placed on the CPU cycle, storage or bandwidth utilized by the organizations (Armbrust et al., 2012).
2.2.5 Research towards on Global Center Traffic
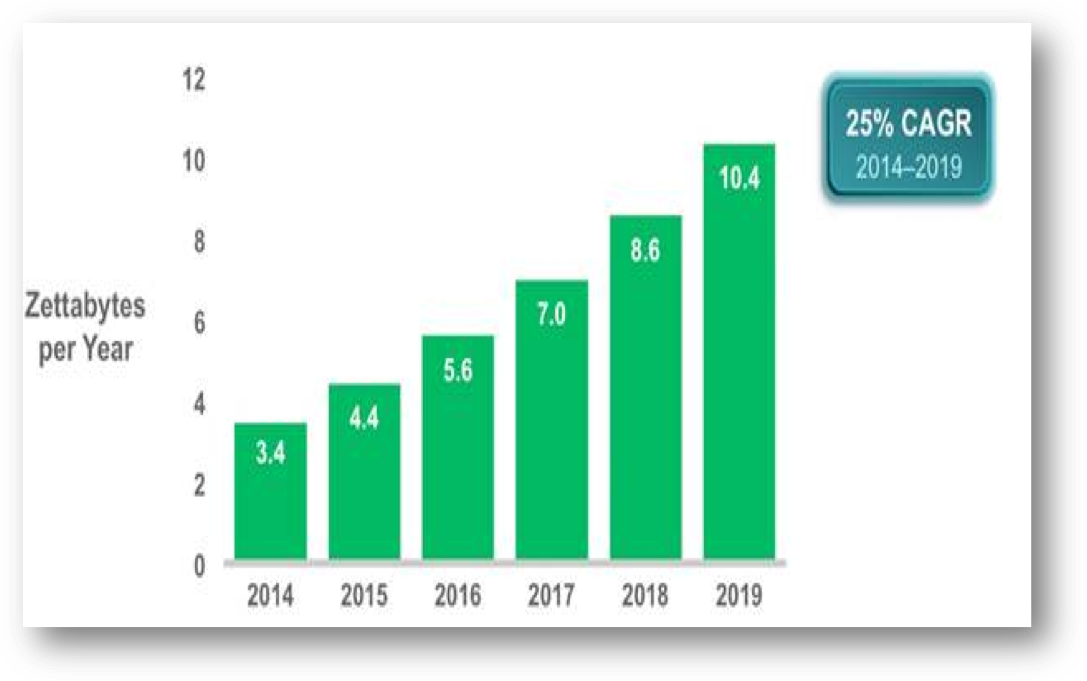
Expenditure incurred during IT shift to converged infrastructure was estimated at approximately $17.8 billion in 2016 according to the projection by research firm IDC that represents the significant increase it had in 2012 of $4.6 billion (Lim et al., 2009).
Most important reason on why modern IT organization focuses on Converged infrastructure is to include quick data service delivery, increased performance of applications, and efficiency in operations. However, in the case of data centers, the connectivity gets slow due to most internets traffic (Bari et al., 2013).
Figure 3: Summary of the forecast on data center IP traffic growth from 2014 – 2019 (Cisco Global Cloud Index, 2014–2019)
Chapter 3. ANALYSIS AND DESIGN
3.1 Introduction
This chapter aims at providing extensive depth of analysis and explanation of methodologies utilized in the study. This will provide an elaboration of the techniques employed in data collection as well as the approaches of data analysis in this study. It will also give a detailed coverage of the different type of data collected in the study. This chapter is important in detailing the justification for the validity and reliability of research results obtained from the study. This includes an apparent justification for the choice of technique used in the approach and its suitability for this research.
The methods employed guide the research design and the collection of data. This was formulated within the confines of the research objectives, research questions and the subject of the study. Additionally, quality of data collected is dependent on the method employed. It is important to note that the amount of sample used in this study has to be a clear representation of the entire population.
3.2 Abductive Approach
The current research under study employed the use of an abductive approach to the exploration of the comparative relationship between the existing case-study findings with the future research findings to ascertain the study results. This approach facilitated the evaluation of Cost optimization techniques performed during an examination of the management complexities in multitier IT infrastructure. Additionally, risk management process encompassing the possible barriers that might affect the validity of the study results was conducted using this approach (Scott, 2015).
This approach is necessary for the interpretation of the research findings. This offers an avenue through which insight into the analogical elaboration of the scientific and sociological phenomena of IT is understood. Additionally, this offers an explanation concerning societal issues important during the study (Scott, 2015).
3.3 Research Design
This research focuses on a collection of quantitative and qualitative data for the realization of the research objectives. The qualitative data derived from a collection is essential for the interpretation of the various research questions and, therefore, attaching the results of which to Converged Infrastructure phenomenon. Alternatively, the quantitative approach permitted measurement of the quantifiable aspects that the organizations employ in the use of CI. The quantification in this research study was employed in cost optimization process by various organizations that were used in the accomplishment of the current study. This was used in the evaluation of data traffic by data centers and the relationship it has from the time before Converged infrastructure implementation in IT to the time of its adoption. This will then be represented in percentage performance and ratios (Scott, 2015).
The qualitative approach in this article was relevant to answering the ‘how’ and ‘what’ questions that research aims to answer. This includes determining the effective application of converged solutions to help in establishing a cloud environment through a modular approach. Additionally, the research will uncover the correct level of recovery and data management in different IT organization. This also includes the use of data tokens and the migration process in influencing the performance of different IT infrastructure organizations.
3.4 Data Collection
Quantitative and qualitative data that was obtained from this study was collected using two major criteria namely; primary and secondary data collection.
3.4.1 Secondary Data
This refers to existent data that is relevant to the establishment of a credible research background. In this case, the secondary information that was derived in this study gave a deeper insight into the facts concerning Converged infrastructure. This also paved a way for the creation of a legal framework that guides the future of the converged infrastructure and its role in reshaping data centers. The secondary data depicted an evolution of the data centers from using crude means in data handling, storage and transfer (network usage) to the implementation of converged infrastructure in their systems. This, therefore, shed light on the factors that have contributed towards the transition and the changes that have occurred because of this shift. A clear understanding of the basics and the framework of converged infrastructure in data centers was necessary for this particular study for cross analysis (Shivakumar, 2012).
Therefore, this means that a comparative study can be done to establish the patterns and the relationship between the past and the future case-study findings to ascertain the study results. These trends revealed the impact of frameworks adopted by organizations in making the process of data handling easy and manageable. This is because the autonomy of these institutions and particularly the data centers plays a crucial role in the determination of growth and expansion rates of these companies. The secondary data was derived from magazines, newspapers, books, journals, annual reports as well as peer-reviewed articles that shed light into the modalities of operation, dynamics and the merits & demerits of incorporating a converged infrastructure by organizations (Kryvinska, 2001).
3.4.2 Primary Data
Primary data was collected from various agencies that are known to handle large chunks of data to ascertain the frameworks that they use in data handling and whether they use Converged infrastructure. This provides reliable information that permits and informs the next step of action taken for improvement. In this study, the use of surveys/questionnaires designed for the collection of relevant data from the stakeholders in the IT organizations. The study also employs the use of guided interviews that were conducted in various organizations among their employees working directly in the data centers. The responses from the study will inform the recommendations and the basis for discussion.
The use of online surveys/questionnaires was employed to enhance the ease and wider coverage throughout the major organizations that handle large data throughout the US. The study generated a list of the email addresses of these organizations and access to their employees for use of the online survey. A copy of the survey questionnaire was sent out to the potential respondents who were requested to fill the questionnaires to help the research. The sample size of the respondents used in this study was 100. This was deemed as representative of the whole population and was sufficient to draw conclusions and inferences concerning the research area. The questionnaire used is present in the appendix.
Chapter 4. IMPLEMENTATION (REALIZATION)
4.1 Introduction
Primary and the secondary data obtained from this study were analyzed and interpreted. Here, therefore, gives a detailed coverage of the presentation and debate of the both quantitative and qualitative data derived from data collection. The answers that were obtained from filling the questionnaires by selected IT companies and employees were analyzed to obtain viable information about the infrastructure employed. Related case studies and the existing research findings were used to obtain valuable information on converged infrastructure. Five companies were selected for the survey with 20 employees in each company taking part in the research by filling the questionnaires.
4.2 Ethical Consideration
This study observed a strict and high degree of moral concern. This includes the privacy of the responses that the respondents gave on the survey questionnaires. The identity of the employees was kept confidential as well as the free will to give their opinions on the various aspects that the research aims at answering. The reporting of the data will not have any manipulations whatsoever, to maintain the validity and reliability of the results. This is because the findings are relevant for informing the current state of data handling and aspects regarding cost optimizations and management.
Chapter 5. RESULTS AND EVALUATION
5.1 Questionnaire results and Analysis
Part one
5.1.1 CI in reshaping the future of data centers
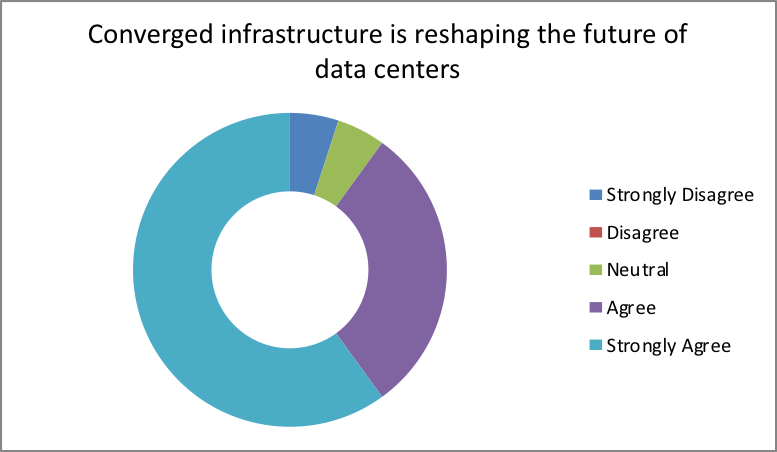
The results obtained from this study indicate that 90 percent of the participants agreed that CI is important in reshaping the future of data centers. Out of these individuals, 60 percent have a strongly agree. This indicates that Converged infrastructure has been attributed to playing a crucial role in reshaping the future of data centers. This is evident from the report by Lockyer (2014) that explained that the economy continues to grow over the years due to the adoption of a converged infrastructure. This is evident that the problems experienced during the economic downturn have slowly evolved into one that is characterized by smooth management, decreased expenses and increased agility in IT organizations.
5.1.2 Converged management
The results obtained above revealed that converged infrastructure is reshaping the future of data centers. This explains the reason 75 percent of the research participants that took part in the study agree that adoption of the CI model in IT organizations makes the management process easy. Additionally, it is evident from the research that adoption of converged infrastructure plays a critical role in solving many of the management complexities. This is because 76 percent of the participants had a favorable opinion this system has made it easy for the management. These results are congruent with the results reported by Sampson (2010). Organization A indicated that this CI system incorporation in their healthcare data center finally led to the easy installation of a new patient, tracking of patient information across various equipment as well as ease of access to information by clinicians, hence boosting on productivity.
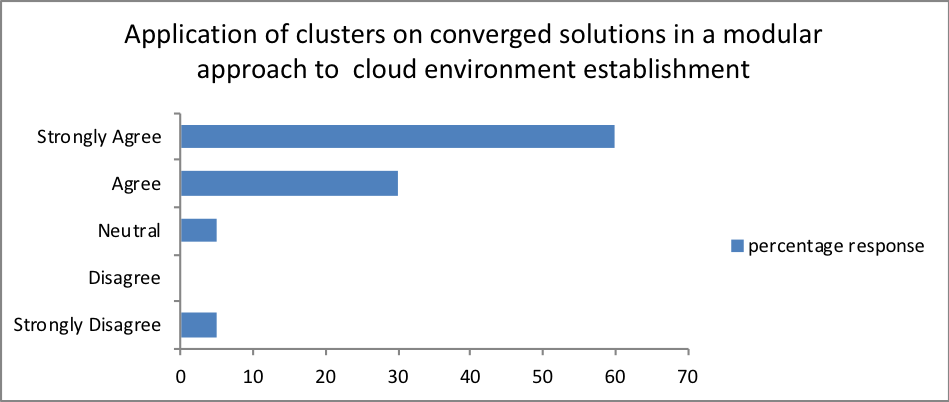
Additionally, over 70 percent of the employees from the participant organizations strongly agreed that the incorporation of converged infrastructure in their organizations would be much beneficial in creating effective and efficient operations. From the results; it is also evident that application of clusters on converged solutions in modular approach assists in the establishment of a cloud-computing environment.
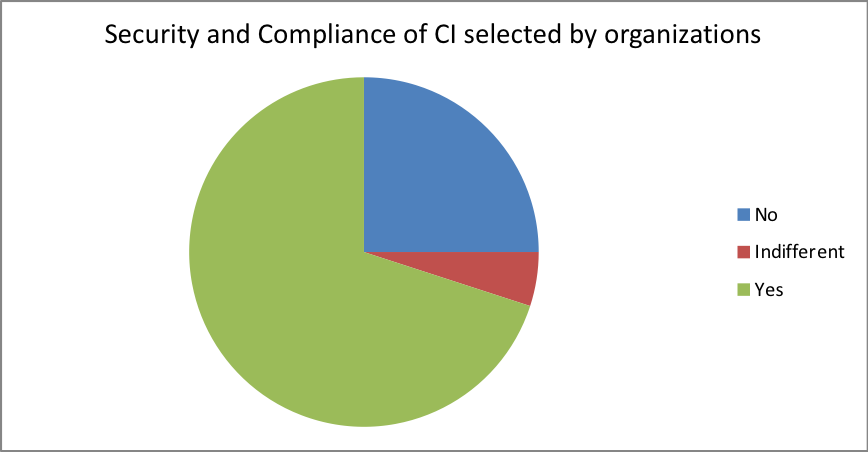
5.1.3 Security and Compliance
70 percent of the employees that participated in the research agree that their organizations have incorporated a CI system and that safety and enforcement plans are in place to protect the data in the centers. However, it is important to note that 20 percent of this indicated that there are those organizations that still have no security in place for their data handling. From this study, this 20 % of employees were from organizations that have not adopted a converged infrastructure. It is, therefore, evident that converged infrastructure plays a crucial role in security over the information that is stored on the network.
This is because the converged infrastructure had a privacy preserving cryptographically designed protocol. One of the participants from follow up interviews revealed that this protocol provided a means through which untraceable emails and payments cannot be discerned thus protecting against piracy and hacking or information falling into the wrong hands. Converged infrastructure, therefore, provides user confidentiality, universal verifiability, and eligibility.
Additionally, the interviews that were conducted revealed that their converged infrastructure spanned multiple domains managed by several infrastructure providers (InPs). These domains further explain the confidentiality because the topology and the information pertaining the resources are kept private by the suppliers’ thus boosting the security of data.
5.1.4 Cost Optimization
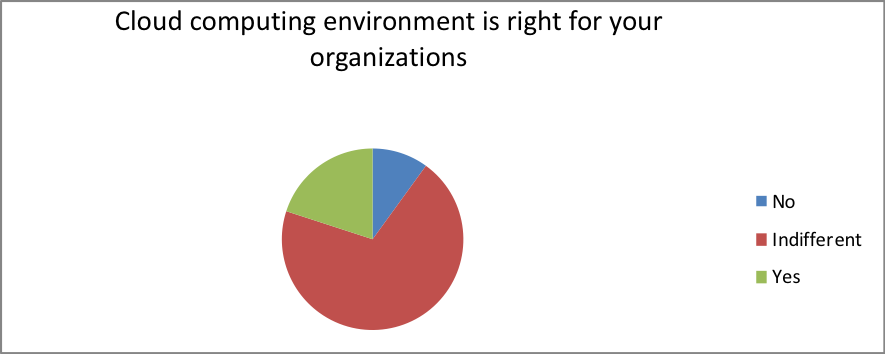
From our analysis, 76 percent of the participants agreed that cost optimization plays a crucial role in influencing the choice of the design. In spite of these results, most of the organizations were not ready to run physical or virtual appliances during the adoption of the cloud-based infrastructure. This could be because the cost of deployment of mobility protocols often relies on the choice of the network provider. Additionally, transparency of the deployment process should avoid terminal/software upgrades to minimize cost. These results are similar to those reported by Yu et al., (2014), therefore, calls for the need to develop cost efficient physical or virtual appliances across multiple domains to ensure that QoS performance is enhanced. This relies on the development of an MILP-based relaxation algorithm that increases cost optimization while providing enough virtual link delay features similar to a report by CIO report (2016).
Part 2
5.2 Data protection in the cloud
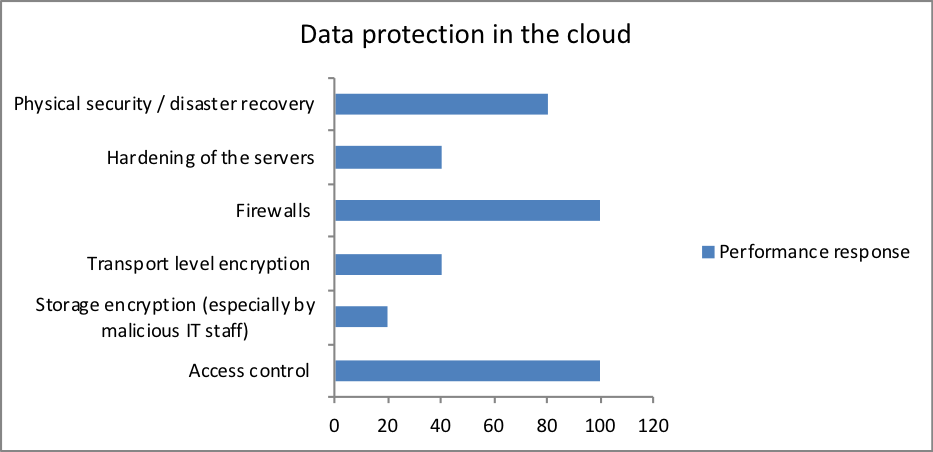
Based on the analysis, there were six means through organizations protect their data on the cloud against malicious access by unauthorized persons. From the analysis, 100 percent of the organizations utilized access control and firewalls. This could be because many people are using the converged infrastructure but may not access certain data, hence the uses of access control to restrict. Additionally, often, organizations use the internet and hence, data is protected from virus/worm destruction over the web as well as internet hacking. However, it is important to note that these twos are not enough to offer adequate security to data hence the use of other methods. From the analysis, 20 percent of the participants used storage encryption, 40 percent used to transport encryption and hardened servers while 80 percent is employed physical security.
It is evident that confidentiality and integrity of data plays an essential role in offering security to cloud computing. However, from these results, come of the organizations have incorporated converged infrastructure but have overlooked accessibility framework. These factors have to be streamlined to ensure perfect security to the data as well as a recovery in case of any losses (Berger et al., 2008).
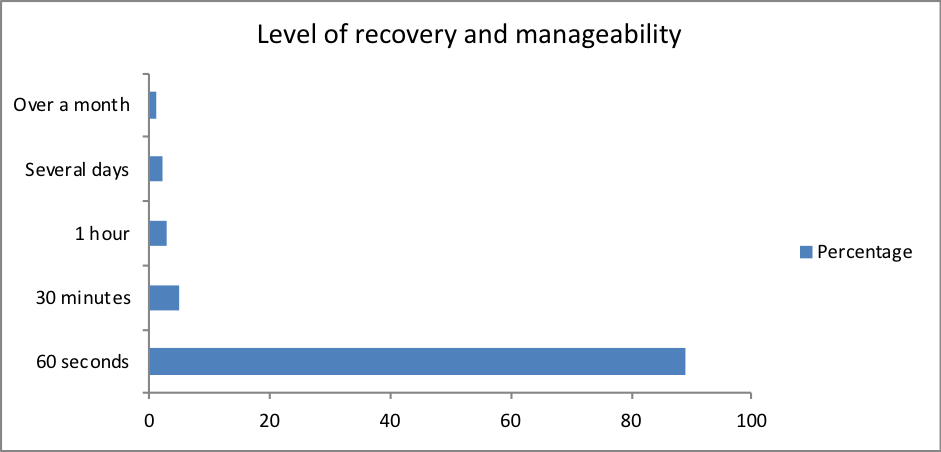
5.3 Data recovery and manageability
Based on our results, 89 percent of the participants had a data recovery and manageability system for their IT infrastructure set at 60 seconds. This is very efficient and is an excellent standard that depicts simplicity in backing up data, restoration of data in case of disasters such as system breakdown, power outages among other factors. This revealed the fact that most of the organizations employ a unified data protection solution that promoted a standard set of custom applications that ensures consistency of the data while reducing the cost of operation. This was also an indication that the organizations use a modular architecture. This means that there is increased extensibility in the IT infrastructure that plays a key role in achieving fast integration due to automation that is policy-based. This could be because of integration of such applications as a snap creator that plays a critical role in supporting physical and virtual platforms within the cloud environment. According to Berger et al., (2009), this is a good indication that most of the IT organizations have already taken precautions to ensure risk reduction and loss of data. However, there was a significant percentage of participants whose data recovery and manageability was poor. This means that the organizations have to step up and incorporate other applications into their converged infrastructure platform to promote data recovery and manageability.
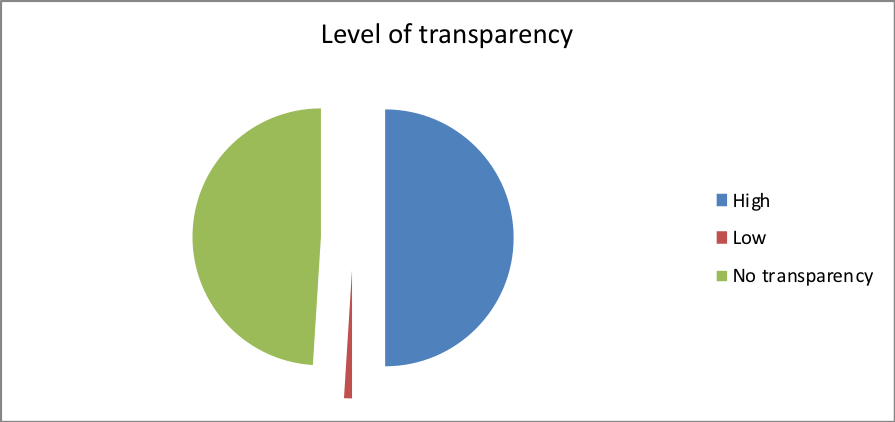
5.4 Data transfer and transparency
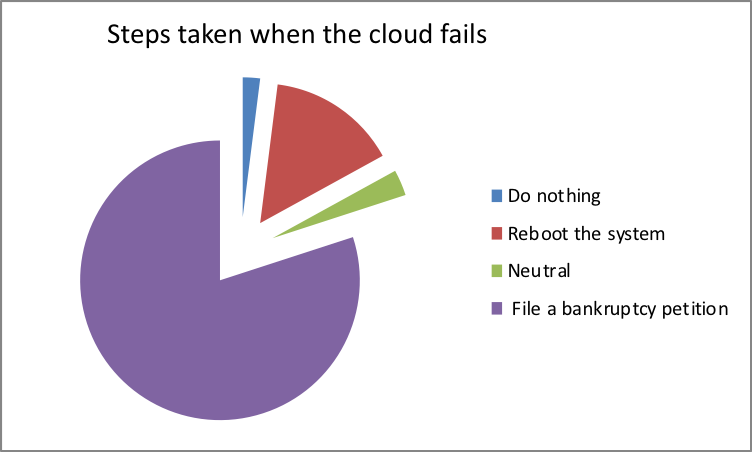
The transparency in handling data by organizations is an important factor that ensures that the integrity of these data is maintained. This study revealed that 80 percent of study participants are aware of the stringent measures to put in place in case of any breach in data security. This includes filing a bankruptcy petition that protects both the data center and the debtor (Douglas, 2013). However, 20 percent of the participants do not have policies in place to ensure data security. This means that educating the employees and organizations that handle large quantities of data on the need for this protection is a requirement.
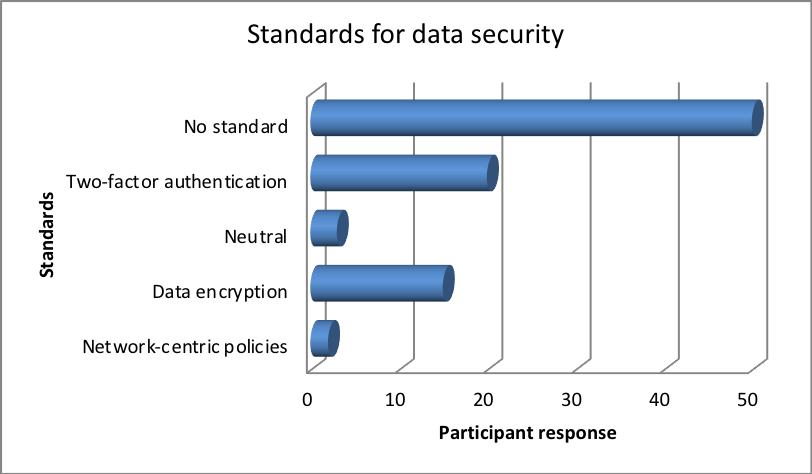
This is evident from the fact that many of the participants employed encryption, network-centric policies or two-factor authentication standards to ensure that transparency in data is only limited to persons who have authorized access. While about 49 percent of the participants had no definitive level of transparency in their data access.
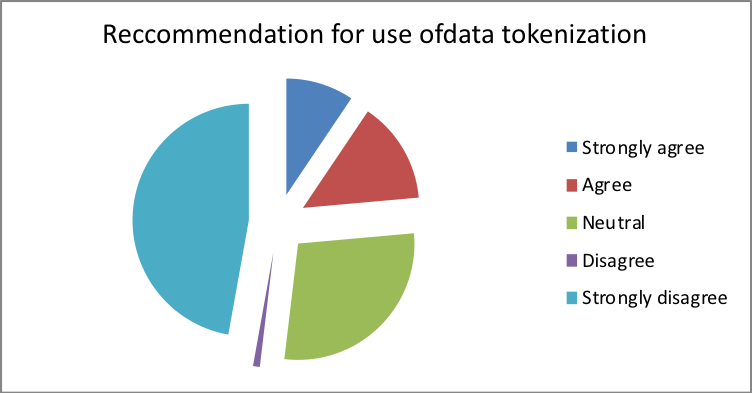
5.5 Data tokenization and migration
51 percent of the participants agreed with the usage of data tokenization in their IT data centers. However, 25 percent disagree while 30 percent remained indifferent concerning the use of data tokenization. This could be attributed to the fact that token usage within a converged system may not require a similar level of security protection for the use of primary account number (Nxumalo, 2014). This is because storing tokens in place of PANs often offer a great opportunity for reduction of cardholder data, therefore, making it easy for merchants to apply PCI DSS requirements. However, one of the reasons why some may have differed with the usage of tokens is the fact that active security control is required for efficient monitoring and performance, which may proof to be difficult and labor intensive (Pci, 2011).
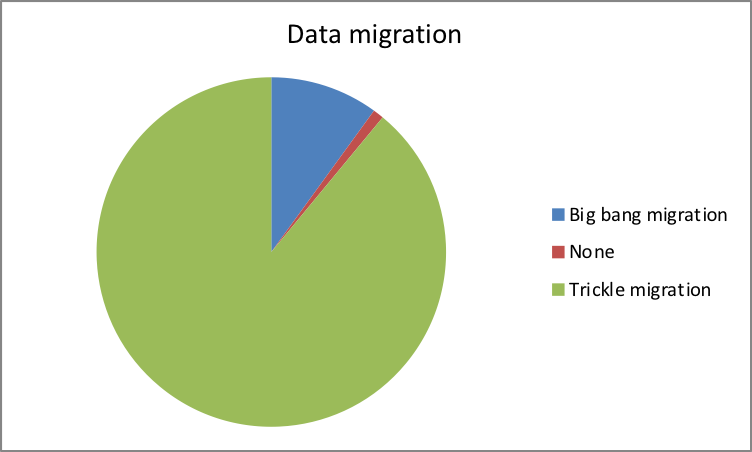
Additionally, 89 percent of the participants used trickle migration in a transfer of their data. Subashini and Kavitha (2011) argue that this could be attributed to the reason that, despite the fact that it takes a longer time to migrate data, this approach involves the use of the old and the new system running in parallel. This provides a zero downtime and can be implemented with real-time procedures hence maintaining data by passing changes into the future system of interest. However, 10 percent of the participants preferred the use of big bang migration approach because of its short defined processing window (Oracle, 2011).
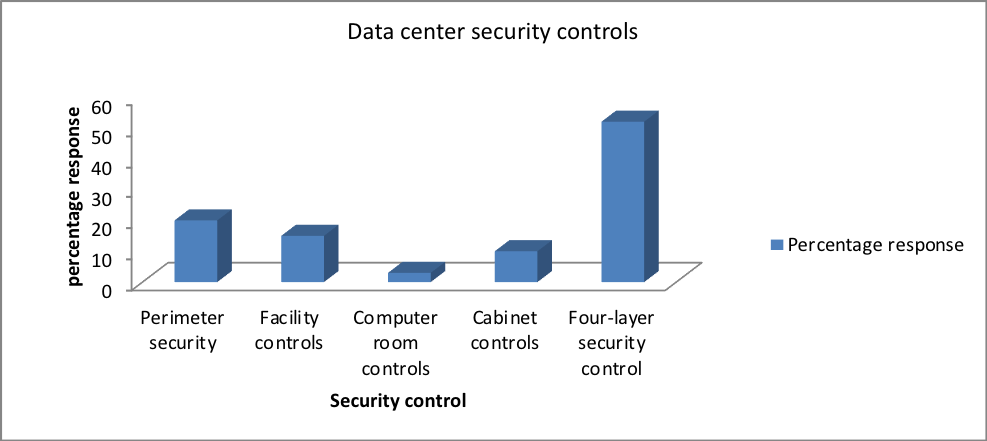
5.6 Data center security controls
From the research findings, 50 percent of the participant employees supported the incorporation of the four-layer security control to the data center. However, 20 percent said that perimeter control should be exercised, 15 percent supported facility control, 3 percent computer room control, and 10 percent cabinet control. This suggested that half of the participants preferred the implementation of a four-layer security control to protect against external as well as internal data breaches. However, some trusted the internal and preferred protecting against only external breaches. It is, therefore, important to take into consideration that even though physical security offers protection control against the external unauthorized persons, a data facility has to employ an internal layer of scrutiny that prevents against inside threats (Manjunath, Hegadi and Mohan, 2011).
5.7 Cloud computing models
5.7.1 Private cloud
Several questions were geared towards answering the reasons why analysis on the cloud was preferable in converged infrastructure IT platform. Private clouds provide the most computing power service that is characterized by high degree of agility and speed using a sophisticated pool of physical computing resources. This is because private clouds often are accessible to only a single organization, therefore, boosting the level of control and privacy of the data in their network. It is often difficult to define the exact service that the private cloud offers but can be defined based on the support it provides the client. This includes the ring fencing that is considered to have the right balance of service since it provides a high level of security to the network. Because of this network security, the organization can be able to process of private data and sensitive activities hence boosting the value of the business. This is achieved through incorporation of the private cloud in computing thus promoting the aspects of resource allocation thereby leading to financial profits made by the organization. This way then, an internal shared service is not necessary. Additionally, private cloud implementation influences the data center architecture through the incorporation of virtualization feature that is characterized by LAN system, high security and privacy, cost and energy efficiency, cloud bursting among other features (Armbrust et al., 2010).
5.7.2 Public Cloud
In this study, it was evident that Software as a service (SaaS) serves as the most familiar model application of the public computing model. However, other applications such as PaaS and IaaS provide a similar service based on their wide availability. Additionally, it was evident that 90 percent of the participants would bypass their IT department to get their applications from the cloud. This would be achieved via software-as-service (SaaS) for a monthly pay-per-user-per-month subscription-pricing model since it offers private individuals with extensive services that they might not be able to reach via a private cloud. This makes it highly efficient in the storage of non-sensitive information as well as online collaborations and emails hence avoiding capacity wastage (Zhang, Cheng and Boutaba, 2010).
5.7.3 Hybrid Cloud
Based on our findings, it is evident that hybrid clouds could be the future of IT infrastructure. This is because it offers both the public and private computing models in achieving various objectives within a single organization. This is because different clouds provide varying levels of efficiencies, therefore; organizations can maximize these advantages by using public clouds services for non-sensitive activities and private clouds where they are needed.
According to Armbrust et al., (2010), Hybrid Cloud integration into the IT infrastructure of any organization offers a high level of flexibility. This can be attributed to the availability of both secure resources that are scalable and profitable. This, therefore, provides the organization with an excellent opportunity to explore a wider range of operational avenues.
It is, therefore, evident that IT cloud services have a brokerage role in defining the future of IT infrastructure. This is because an organization can implement a hybrid cloud that hosts their commercial prospects within a private cloud that are secure and scalable while their brochures are placed on a public site making it cost effective. Additionally, IaaS plays a key role in the hybrid model, through a provision of a storage space for client data within a private cloud for a financial business. Therefore, this could permit partnership in the planning of projects documents on the public cloud. This boosts convenience in accessing the cloud by many users from different localities, as a result, all these features shapes the future infrastructure.
5.8 Validation
The choice of the research companies that were selected for purposes of meeting the research objectives in this study is well trusted to offer a high degree of validity and reliability of the results. Additionally, the employees from these companies that participated in the study contributed towards the reliability and the validity of the data obtained. This is attributed to by the consistency of the responses collected through the questionnaires. Additionally, the research sample size was representative of the whole population thereby permitting inferential conclusions drawn from the study to represent converged infrastructure for all IT companies. The results that were obtained from this study were comparable to those that were reported in previous researches. This, therefore, promotes the reliability of these findings in drawing concrete conclusions on the path to cloud computing based on management and cost optimization (Scott, 2015)
Chapter 6. CONCLUSION
The primary aim of this research work to study the role that is played by converged infrastructure in cloud computing for an achievement of a cost efficient and ease of management of the IT infrastructure. The study involved 5 major IT companies whose identities are concealed in this study for ethical reasons. From these organizations, selected research participants contributed towards a realization of the study’s objectives. It is important to note that the research was successful in answering the research questions thus paving a way for notification of areas of improvement in IT infrastructure firms in boosting their business performances. From our research, it is evident that converged infrastructure plays a crucial role in cost optimization, security control and flexibility in data transfer and management. However, in spite the fact that most of the organizations had employed the use of converged infrastructure, this alone is not enough. This is because; other adjustments have to be made to meet the constantly evolving needs of the users, clients as well as organizations. The results of this research apply to various levels of organizational growth achieved through adopting this infrastructure that drives innovation, agility and speed of the technology to heights that keep pace with the demand for an enterprise.
6.1 Lessons Learnt
We have learned that in a world that organizations are striving towards coping with the rapid changes in the market, adoption of converged infrastructure dramatically boosts agility. The solutions that are obtained from adjustments based on the research finding in this study promises to extend the benefits of convergence through a delivery of new speed levels, ease of management and efficacy. This, therefore, enables clients to exercise readiness in anticipating changes while capitalizing on the strengths of the infrastructure for the growth and expansion of their businesses.
With the adjustments and incorporation of useful cloud computing services, unified storage architecture offers a promising avenue through which cloud computing, virtualization, and application of large chunks of data reshapes the future of IT infrastructure. This is because; the challenges experienced in these regions are quickly changing the relationship between data storage, networks, servers, and application. Because of this relationship, a new level of integration across the organization is becoming a huge necessity.
6.2 Academic Application and Limitations
The results obtained from this research play a key role in academia. This is because the research questions that are derived because of this research provide avenues through which students and lecturers can explore in making the world a better place. This is because the knowledge that is obtained is essential to gaining a solid understanding of this field of study while molding the future of students’ specialties. Whether one is starting to virtualize or become an expert on the path to cloud, converged infrastructure provides a solution needed to transform IT. However, for the field of academia, the rate-limiting step is that of limited support for practical hands-on experience for the students. This, therefore, means the great ideas birthed have to be implemented in well-equipped organizations. Getting access to these facilities is usually impossible.
6.3 Business Application and Limitations
The primary goal of any business is to make profits while minimizing the cost of expenditure. This is what converged infrastructure offers the business. The results of this study demonstrate that adoption of a converged infrastructure plays a central role in cost optimization and ease in management. This is because it is mainly based on a set of standard elements that offers a pool of resource for a specified amount of IT capacity. Because of these systems, there is increased automation levels achieved through a dynamic balancing of resources, a factor critical for business-oriented applicability. This makes it easy for a business to carry out disaster recovery and security control of their data making it affordable. This can be achieved through reduced wasteful provision of hardware assets and recurrent balancing of the system as they continually evolve and a significant reduction in clustering of data centers.
However, the limitation that this has on business enterprises is the fact that a substantial initial cost has to be incurred to set up a stable and sustainable IT infrastructure. Additionally, continual training of the employees is important to keep up with the market changes to better tap into the growing opportunities in the market.
6.4 Recommendations / Prospects for Future Research / Work
From our current research, it is evident that delivery of more promising solutions on converged infrastructure is not enough. This, therefore, requires that IT organizations make suitable and sustainable adjustments in the selection of their existing products and management to exploit the potential of converged infrastructure. While taking surveys from the participants who are employees of the organizations under study, I came up with three major recommendations:
- To revamp the organization IT infrastructure to step away from a device-oriented system to one that is driven by resources through archiving, partnerships and database structures that are more likely to boost cost optimization and management.
- Implement continued the education of the employees to implement a mature centralized system that is characterized by automation hence promoting performance and installation of a structural chargeback platform.
- Embracing hybrid cloud computing model that simplifies management and improves agility while offering interoperability and shift in the application of both the merits of private and public clouds.
APPENDICES
Appendix A. Sampling
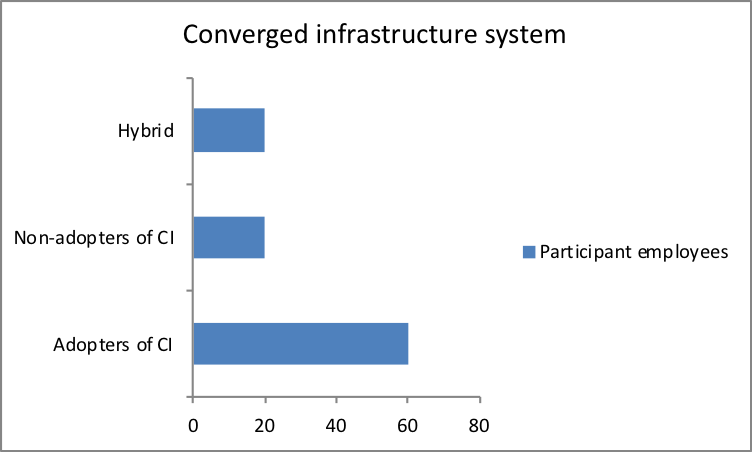
Five IT companies were selected for the purpose of realizing the objectives of the current research topic. 100 participant employees were selected from the IT companies to take part in the research in representation of their companies.
Current adopters of IT Converged infrastructure Vs non-adopters of converged infrastructure:
| Organizations | Participant employees |
| Adopters of CI | 60 |
| Non-adopters of CI | 20 |
| Hybrid | 20 |
APPENDIX B: Respondents demographics
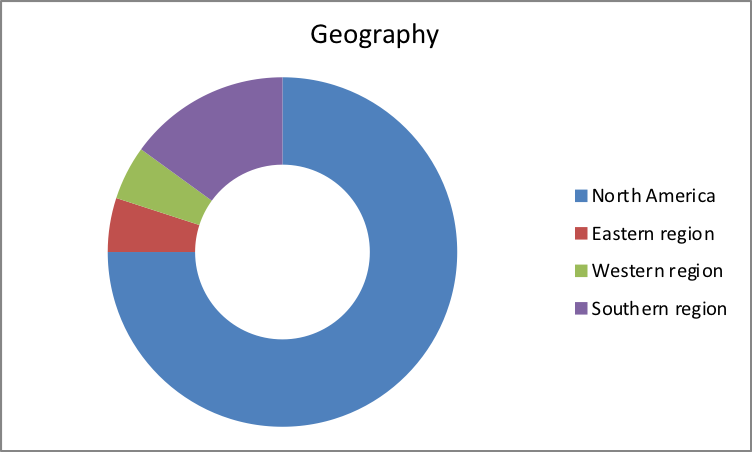
Geographic location
Given the nature of the research survey, 75 percent of the respondents were from northern America. 15 percent were from southern region, and 5 percent from east and western parts of the continent.
| Geographic location | Participant employees |
| North America | 75 |
| Eastern region | 5 |
| Western region | 5 |
| Southern region | 15 |
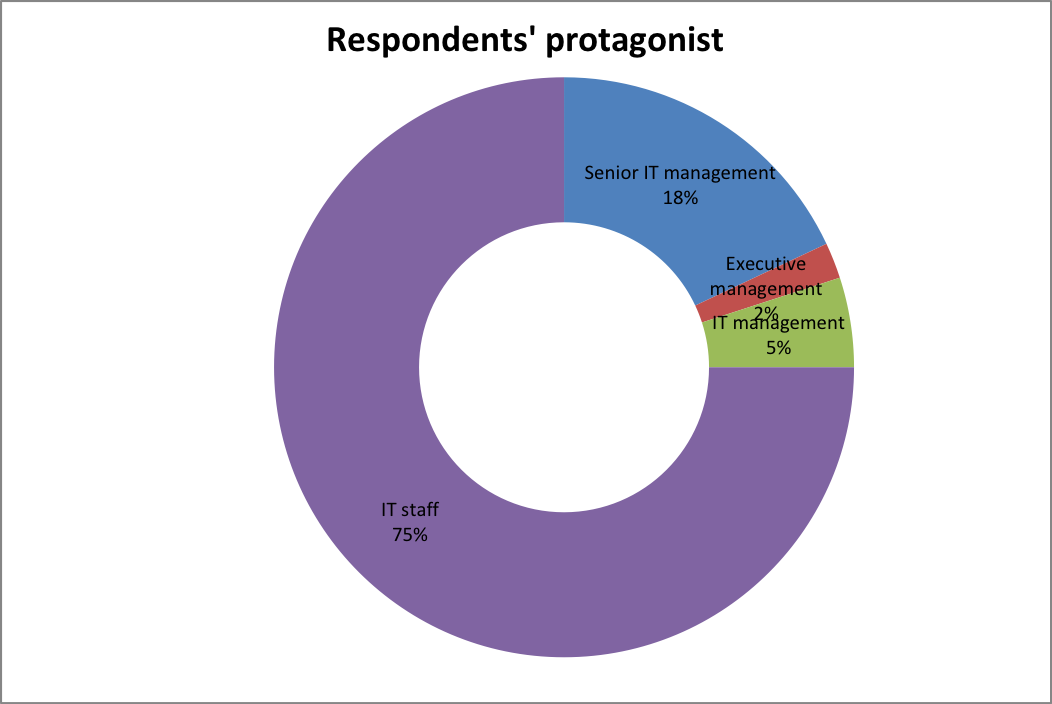
Respondents’ protagonists
The study was targeting converged infrastructure in IT companies. The respondents in the study therefore balanced the participants in terms of their roles in their respective companies.
| Current employee role | Participant response |
| Senior IT management | 18 |
| Executive management | 2 |
| IT management | 5 |
| IT staff | 75 |
APPENDIX C: Questionnaire responses
Questionnaire one
- Is converged infrastructure reshaping the future of data centers?
| Response | Percentage |
| Strongly Disagree | 5 |
| Disagree | 0 |
| Neutral | 5 |
| Agree | 30 |
| Strongly Agree | 60 |
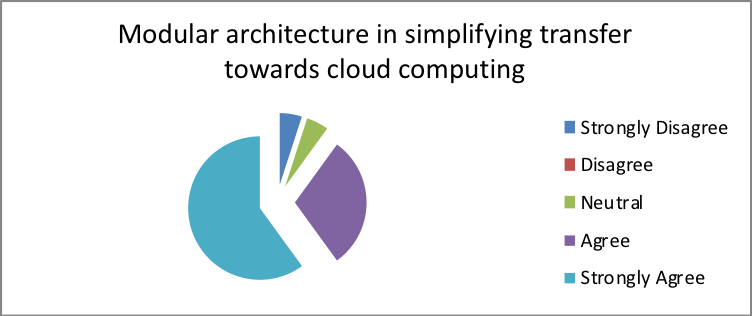
- Does modular architecture simplify the company’s transfer towards cloud computing?
| Response | Percentage |
| Strongly Disagree | 2 |
| Disagree | 3 |
| Neutral | 15 |
| Agree | 20 |
| Strongly Agree | 60 |
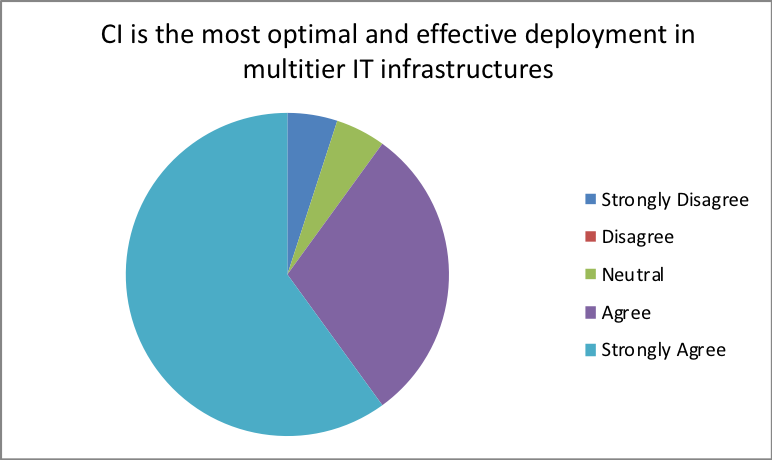
- Is converged infrastructure the most optimal and effective deployment in multitier IT infrastructures?
| Response | Percentage |
| Strongly Disagree | 5 |
| Disagree | 2 |
| Neutral | 15 |
| Agree | 15 |
| Strongly Agree | 63 |
- Does cost optimization play a key role in influencing design while taking care of management complexities
| Response | Percentage |
| Strongly Disagree | 20 |
| Disagree | 2 |
| Neutral | 2 |
| Agree | 50 |
| Strongly Agree | 26 |
- Does migration between converged solutions become easier to manage?
| Response | Percentage |
| Strongly Disagree | 20 |
| Disagree | 2 |
| Neutral | 3 |
| Agree | 5 |
| Strongly Agree | 70 |
- Can modern data centers employ converged architecture?
Response Percentage Strongly Disagree 20 Disagree 2 Neutral 3 Agree 5 Strongly Agree 70
- How effective is it applying clusters on converged solutions in a modular approach to assist in establishing a cloud environment?
| Response | Percentage |
| Not effective | 2 |
| Least effective | 15 |
| Neutral | 3 |
| Effective | 20 |
| Strongly Effective | 50 |
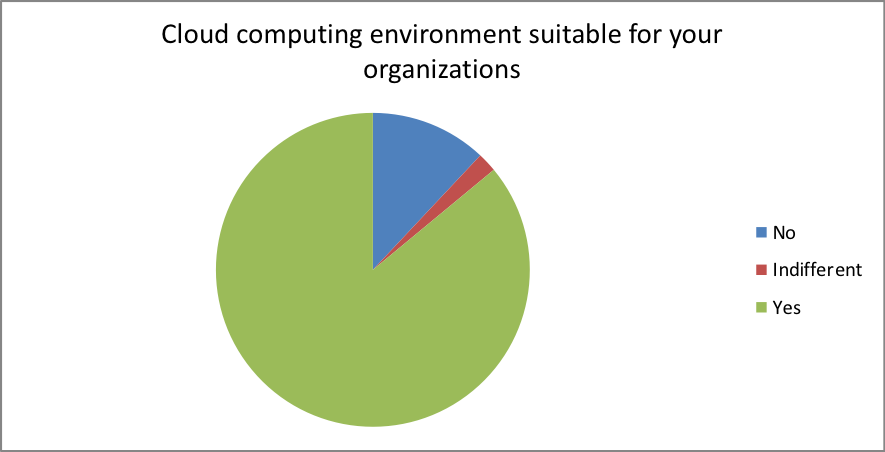
- Is the Cloud computing environment right for your organizations?
| Response | Percentage |
| No | 12 |
| Indifferent | 2 |
| Yes | 86 |
- Security and Compliance challenges – Is the organization extending its enterprise security level or policy of the Clouds been selected?
| Response | Percentage |
| No | 25 |
| Indifferent | 5 |
| Yes | 70 |
- Is the organization ready to run physical appliances or virtual appliances during consuming cloud-based infrastructure?
| Response | Percentage |
| No | 10 |
| Indifferent | 70 |
| Yes | 20 |
Questionnaire 2
- How will you protect your data in the cloud?
| Data protection in the cloud | Performance response |
| Access control | 100 |
| Storage encryption (especially by malicious IT staff) | 20 |
| Transport level encryption | 40 |
| Firewalls | 100 |
| Hardening of the servers | 40 |
| Physical security / disaster recovery | 80 |
- Data recovery and manageability
- What is the right level of recovery and manageability in your organization?
| Response | Percentage |
| 60 seconds | 89 |
| 30 minutes | 5 |
| 1 hour | 3 |
| Several days | 2 |
| Over a month | 1 |
- What security controls should you inject?
| Response | Percentage |
| Perimeter security | 20 |
| Facility controls | 15 |
| Computer room controls | 3 |
| Cabinet controls | 10 |
| Four-layer security control | 52 |
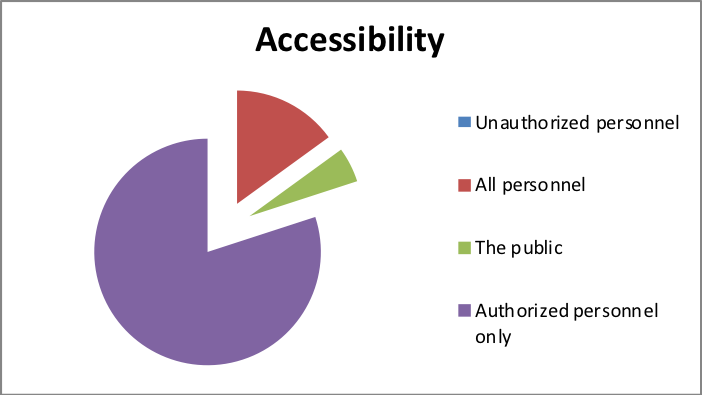
- Who will have access?
| Response | Percentage |
| Unauthorized personnel | 0 |
| All personnel | 15 |
| The public | 5 |
| Authorized personnel only | 80 |
- Should you use data tokenization?
| Response | Percentage |
| Strongly agree | 10 |
| Agree | 15 |
| Neutral | 30 |
| Disagree | 1 |
| Strongly disagree | 50 |
- How will you migrate data?
| Response | Percentage |
| Big bang migration | 10 |
| None | 1 |
| Trickle migration | 89 |
- Data transfer and transparency
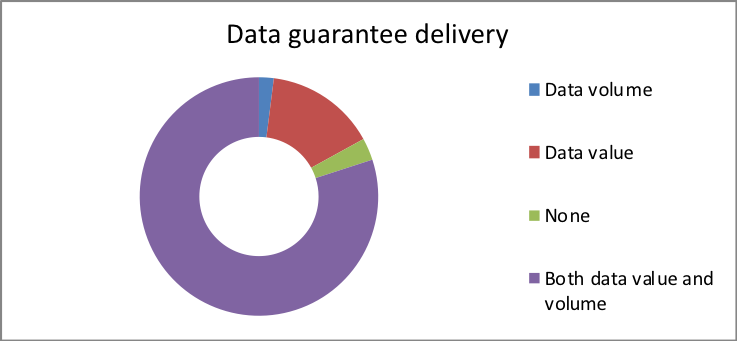
- Which will guarantee delivery?
| Response | Percentage |
| Data volume | 2 |
| Data value | 15 |
| None | 3 |
| Both data value and volume | 80 |
- What if the cloud fails?
| Response | Percentage |
| Do nothing | 2 |
| Reboot the system | 15 |
| Neutral | 3 |
| File a bankruptcy petition | 80 |
- Where are the standards?
| Response | Percentage |
| Network-centric policies | 2 |
| Data encryption | 15 |
| Neutral | 3 |
| Two-factor authentication | 20 |
| No standard | 50 |
- What level of transparency do you need?
| Response | Percentage |
| High | 50 |
| Low | 1 |
| No transparency | 49 |