Executive summary
A remote system of IoT-based remote patients monitoring systems like home, cardiac, and sensors monitoring cement emerged like an active approach to patient healthcare. The study is a layer-wise component and security analysis of an IoT application and evaluated an application developed by Cyber health Ltd. This company is taken according to case study. Added to this, the major aim of this study is to understand and analyse the weaknesses relevant to IoT-based architectural systems. As a result, security measures were also determined based on various aspects of the application. The explanation of this study dealt with encryption and security systems. After that, possible conclusions of the IoT-based healthcare system were also discussed in terms of social and economic implications. Thus, the healthcare development and medical management can be properly organised through measuring IoT-based application and monitoring systems.
Introduction of the study
The application layer of IoT (Internet of things) indicates all the applications of technological aspects are implemented, and this includes smart health, smart cities, and tracking of patients’ health. It is able to manage responsibility and provide better services to the IoT layer application and security analytics included in it. The study is mainly based on “a layer-wise component and security analysis of an IoT application”. IoT security is an activity for managing proper connections across a network along with preventing cyber-attacks and protective measures. An IoT-based remote patient is going to be developed by Cyber health Ltd. in this regard along with “Network and cyber security solutions”.
Task 1: Discuss the three- and five-layered architecture of the IoT-based remote patient monitoring system
The 3 layers and 5 layers of IoT based architectural patient monitoring system are really appropriate for managing healthcare and different system of health management. Recently Cyber Health Ltd. focuses on this kind of technological growth for healthcare services. It also connects to IoT devices via short-range communication networks such as Bluetooth, and other systems
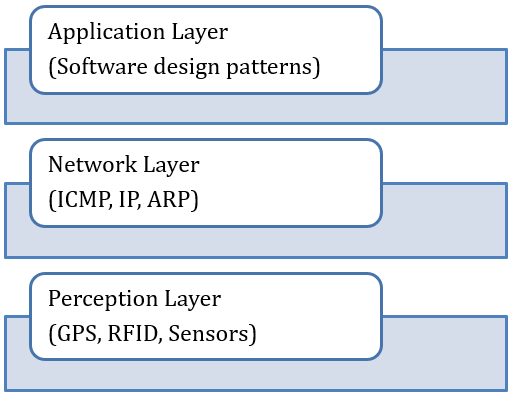
3 layers of IoT architecture
Figure 1: 3 layers IoT based architecture with components
(Source: Burhan et al. 2018)
There are three layers in IoT architecture, and these are Network IoT-based architecture, Perception IoT-based architecture, and Application IoT-based architecture. IEEE accepts this particular formation of 3 layered architecture of IoT.
Network architecture:
This is mainly focused on data transmission of the layer, and data gathering is confirmed by the transmission system (Burhan et al. 2018). Added to this, all the data and information are equipped through servers, smart objects, and network devices.
Perception:
It consists of different sensors and devices that help to gather various ranges of frequencies to its receiver part and that mostly includes edge devices, actuators, and sensors.
Application:
This layer interacts with the end-users and manages to deliver the proper services to users of the application in IoT (Farahani et al. 2018).
The system, Smartphone-based data acquisition gateway, internet scale Data storage and search system and backend analysis machine for diagnostic and prognostic purposes. With the need the advantages of electronic and IT services in the medical field are emphasized with sensors that are attached to the patient’s body to receive signals.
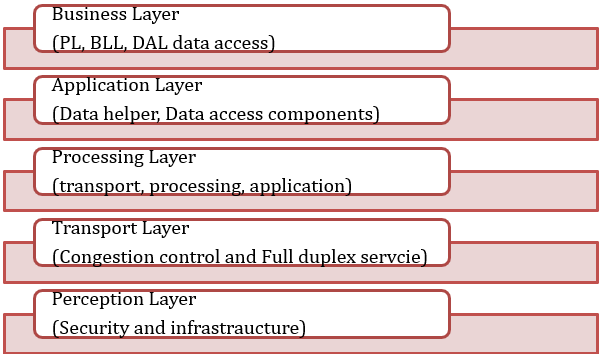
5 layers of IoT architecture
Figure 2: 5 layers IoT-based architecture with components
(Source: Self-created)
Application layers of IoT are totally based on monitoring systems of remote patients that need to be managed by using “dynamic cutting-edge technology” for serving a broad area of services.
These are discussed below.
Middleware – This layer is an architectural decision component that processes the received data in memory and contains various calculations (Zyrianoff et al. 2020). This data is then tracked, and the device is named according to its address.
Perception – This is the same as the three-tier architecture, where all devices function to collect a variety of data used by sensors such as light, temperature, sound, and humidity. This records the information and passes it to the next shift.
Network – Connect the data collected by the sensors to the next layer of elements using network technologies such as broadband, cellular networks, infrared, WIFI, and UMTS (“Universal Mobile Telecommunications System”). The transmission is confidential and is encrypted with all personal data (Rahimi et al. 2018).
Application – The application then receives the calculated data and uses it to send an email, turn the device on and off, and use the smart watch that can be made decisions by the middleware layer.
Business – This is part of the architecture that interacts with the recipients of the service (Bakhshi et al. 2018). This application can serve different types of analytics, but we are not just technology dependent.
Task 2: Risks and issues in cyber security system on te basis of IoT based architecture
Issues and risks in cyber security are considered as the degree of exposure after a cyber-attack in an organisation. This includes loss of effective data and information as well as critical assets. Besides, security analytics in IoT will help to detect anomalies in the transmission of information and data for removing security threats. The vulnerability of organisational networks is increased to a certain extension, and that can result in organisational risk (Abdullah et al. 2019). This is only responsible for the technical infrastructure of the company with its casual management. Few companies are using cyber health to serve their customers with IoT solutions. Cyber Health is interested in growing its business by servicing customers who provide IoT solutions.
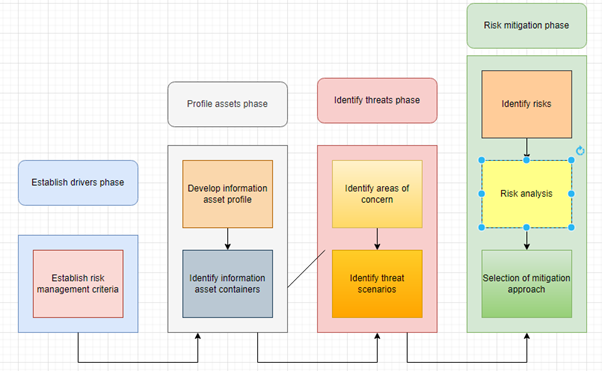
Figure 3: Framework of IoT-based “OCTAVE”
(Source: Self-created)
“Risk assessment”:
The risk of the device used for the company can be assessed using the IT risk assessment framework, which has an approach of assessing the risks associated with the technical apparatus called “OCTAVE” (“Operationally Critical Threat, Asset, and Vulnerability Evaluation”).
The issue and risk of devices used by the company can be identified by using an appropriate framework relevant to IT risk assessment (Eggly et al. 2019). The IT Risk Assessment Framework provides an approach to assessing risks associated with technical devices known as “OCTAVE (“Assessment of Critical Operational Threats, Assets, and Vulnerabilities”).
These are as follows:
Criteria to risk measurement- The associated risks of a particular application can be related to effective personal data and help to store data in the patient’s application. Apart from that, data misuse can be restricted through this process to manage cyber-attacks.
Identification of asset containers – Asset containers and the devices used are not fully enhanced, and the use of devices in unsecured supply chains can increase cyber security risks (Anand et al. 2020).
Developing profiles of assets – It is necessary to identify Risk profiles for developing according to the anticipated risks, and all these are required for the application’s technical aspects.
Identification of schemes of threat – Various threats are included within the IoT application, and that is caused by the cyber attackers due to API, cloud, and network as well as unsecured management (Eggly et al. 2019).
“Identifying concerned sectors” – Based on the characteristics of the application, data protection must be protected by an encryption system that indicates the risk lies in the data management of the application.
Recognition of risks – Issues in the selected applications can be investigated based on the identified sectors and schemes that indicate threats to IoT applications (Anand et al. 2020).
Examination of risks – Risks can be investigated using an application and its affected sector identification and simulation tests.
Cyber Health Ltd. is a Teesside-based provider of cyber security solutions with network and cyber security solutions for business environments. Few companies are using cyber health to serve their customers with IoT solutions. Cyber Health is interested in growing its business by servicing customers who provide IoT solutions.
Task 3: Explain with examples how you would analyse the end-to-end (E2E) security vulnerabilities or concerns
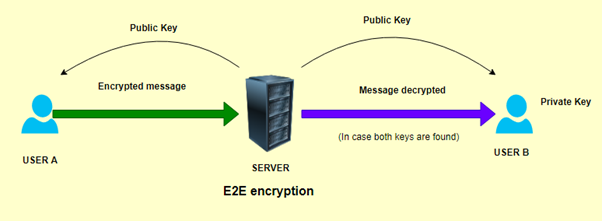
This selected application and security management for 3 layers IoT architecture will be managed through E2E encryption, and that will be kept as data protected activity. For managing risk assessment, this encryption can help to recognise different areas of vulnerability (Peralta et al. 2019). All these considering layers are actively discussed below in an appropriate manner.
The measurement of 3 layers and 5 layers IoT based architecture can use to measure the best monitoring system. The Internet of Things (IoT) is one of the best moments, with millions of devices connecting to the Internet to communicate with the manufacturer’s servers and then with us. The data generated by the IoT is encrypted to some extent when it is transferred over the Internet. However, it is important to have consistent protection from start to finish.
Figure 4: E2E encryption system
(Source: Self-created)
Perception:
The application you choose has a device that collects a variety of data and sends it to the architecture-related network. To minimise the potential vulnerabilities of data breaches, devices involved in the application’s architecture must be encrypted using an E2E encryption system while the data is being processed by the device. Cross-domain design works here where applications and connections are involved (Peralta et al. 2019). In this case, the application of choice is a mobile or web application that allows the patient to enter a variety of records, such as bank details and other highly sensitive and vulnerable personal information. This is vertical security that flows from the application to the hardware of the architecture.
This data can be leaked through loopholes in cryptographic systems and become vulnerable. Therefore, the data provided by the patient should be encrypted using a cloud-based security system. This ensures that your application does not have problems with unenhanced devices that can lead to problems related to data vulnerabilities. This data can be compromised if the device is not E2E encrypted (McPherson and Irvine, 2020). For example, if a patient enters personal information in a form that is used before scheduling an appointment and getting a medical history, the patient also enters the payment details used to pay the invoice. For the extended “domain level security management” of the selected application, you need to create an accurate “asset inventory”.
Network:
The selected application involves sending sensitive financial and personal data over the network being used. These data are vulnerable in modern digital environments. This should be done using a variety of security management tools and techniques, such as logging, access control, network security, and key and certificate management. Before you start your application, you need to decide whether to make “connection level security” dependent or independent (Staudemeyer et al. 2018). For example, if an application sends patient data to various sources for processing, a secure access control system should be deployed to protect the data as needed. From the requirements of the application, it can be analysed that data management and transmission are to be “E2E encrypted” for ensuring proper “data security” and keep this particular application from being vulnerable to cyber-attacks.
“Machine learning analysis needs to be used in “network systems” to make it significantly more secure for further development of the entire architecture. After that, the automation of the network system is limited to make the security check more thorough (McPherson and Irvine, 2020). Applications in the Covid 19 era are more fruitful because they are the most vulnerable layer to cyber attackers, with more E2E encryption of data that can be performed more accurately on network systems. The selected application monitoring system is continuously and frequently accessed by the sole “Cyberhealth Ltd”, which makes the entire application monitoring process more secure and minimises vulnerabilities. Health-related applications contain data from helpless patients who need help and support. Remote networks that are vulnerable to security systems that are underestimated by the application are used.
Application: Different encryption systems for security purpose
The layer of architecture, which is the actual interface for interacting with the patient, should be based on a well-constructed security system. This refers to a vendor-based authentication system that further relies on the security of the hardware and devices that make up the overall vulnerability of the application. Use different types of authenticators and security gateways to more strongly encrypt your application’s identity management and protect your application from data breach vulnerability (Neisse et al. 2019). The threat intelligence of the selected application should be based on the application’s interface built into the various provider-based communities. You can develop various automatic authentication systems for your E2E cryptosystem to help manage your application’s identity. For example, if a patient uses the application, they need to authenticate the patient’s information that they protect from the perspective of vulnerabilities.
“Task 4”: Discuss countermeasures for the identified security concerns of the sensing layer of the selected patient monitoring system
The media of Heterogeneous selection can be effective for managing different factors like patient status, sensor trigger sources, IoT device capabilities, media availability, and several temporal information .
Cyber Health Ltd. is a Teesside based cyber security solution provider with Networking & Cyber security solutions for the business environment. Few companies are using Cyber Health to serve their IoT solution customers. Cyber Health is interested in growing its business by servicing customers who provide IoT solutions.
The effective measurements of IoT security of particular applications are dependent on various sensors within the system.
These are such as:
Password protection – To protect the data from misuse of various sensors by the patient, the patient’s password must be protected by E2E encryption of the data.
Design – Security issues can also persist when designing sensors with various hard-coded passwords. This can be resolved by using a device with a secure boot and a controlled user interface (Yin et al. 2019).
Implementation – Application sensor implementations can be vulnerable and can be protected by various software development processes such as the Microsoft Security Development Lifecycle. This eliminates errors in coding application sensors and their features.
Deployment – Sensor safety issues can also occur during the sensor installation phase. This issue can be addressed by embedding a unique code and password in the system that protects the system from various forms of cyber-attacks (Nayyar et al. 2020).
“Task 5”: Discuss and make informed comments on emerging applications of IoT in healthcare, demonstrating an understanding of the social and commercial context
IoT-based health applications range from a variety of applications that can sense the temperature required to deliver a vaccine to a patient. In addition, most of the diagnosis is performed by remote sensors installed in the patient’s place of residence, making patient treatment more comfortable and cost-effective. Some applications transfer medical data from one source to another. In addition, it will emerge as another new industry dealing with remote health surveillance and will generate more income for the country from the health sector. These applications are also based on the capabilities of sleep monitoring and efficacy tracking systems (Peralta et al. 2019). The social reasoning of these applications is based on the efficiency with which patients can be treated at home and do not have to leave the place. This is a problem for some types of patients. In the case of healthcare applications, triggering of data collection mainly based on recording of parameter, current frequency, and medical professionals with effective categorical acquisition methods.
IoT-based health applications will increase the sales of applications that increase the sales of medical institutions. Medical care for patients has become easier, and the use of the system is increasing (Eggly et al. 2019). The potential of the application has created the need to monitor the strength of specific sensors. Also, more and more programmers are being used to develop applications and their cryptographic systems. More and more doctors are getting patients who have increased their income. The commercial conclusions of the application relate to the revenue generated from the deeper niche markets of the healthcare segment. It is implemented to improve the comfort of patients who are struggling to move away from their place of residence (Staudemeyer et al. 2018). Smart health systems have also concluded that the use of applications by other types of patients who want to avoid seeing a doctor because of their lifestyle is increasing. It has also spawned other industries, such as the manufacture of sensors and devices.
Conclusion
From the above discussion of the entire study of architectural IoT based security, it is seen that Cyber health Ltd. developed this IoT application for security purposes. This is helpful for remote monitoring system five-layer architecture can manage E2E encryption for maintaining vulnerability related to financial and personal data of patients. The architecture also includes various authenticators in the sensor of the device that can be used to protect data from cyber attackers. Thus, a weakness risk assessment was also performed using the OCTAVE framework. Therefore, the healthcare development and medical management can be properly organised through measuring IoT-based application and monitoring systems. Hence, the layer based IoT architectural designing system for remote patients are really helpful for managing the healthcare activities and Cyber Health Ltd. Tries to implement IoT based architecture in case of Healthcare services to patients.