Abstract
Social media mostly influences today’s world, and thus, this has been seen as a lifestyle and the latest trend in society. The benefits of social media are evidenced, ranging from connectivity and delivery of important news to sharing of daily activities between individuals across the world. But the cons of social media are also everywhere since it has led to the increase in social crimes, bad businesses such as the selling of drugs. Therefore, this has made the information uploaded on social media investigated, especially on Twitter and Instagram. To support verifying the crimes that happen on social media, the techniques are needed to perform the analysis. Hence, this research analyzes the artifacts that social media applications, including Twitter and Instagram, produce on android phones. The research that we did is helpful since it produces the benefits that analysts and practitioners so as to help in finding the evidence on Twitter and Instagram android phones, such as the account information, the chat messages, the documents uploaded, and all traces. In this research, we developed a forensic framework to extract and preserve Android on all the phone applications such as Twitter and Instagram. Examples are the names(username), mobile number, Identification, text or audio, video, and picture messages between the Instagram and Twitter users. It has shown how sensitive data posted on Instagram and Twitter can easily be reconstructed. The traces and URL links of visual messages can be used to access the privacy of any Twitter and Instagram user without their verification. The ant-forensic method has been applied on these applications and restored the application from the corrupted database file that a criminal could have used to trap the user. The tests involved the installation of some of the networking applications on the phone devices, conducting the activities that are seen to be common through each of the applications, and acquiring the logical image. The forensic analysis was aimed at determining if the conducted activities that happen on the two social media applications (Twitter and Instagram) were afterward left on the internal storage of the smartphone, if they are stored, what was the extent and the significance, the location used for storage, and that if truly they could be restored from the logical image that was on the smartphone. Digital evidence proves an increase in criminal investigations in situations of whether it’s an offense or a serious activity. Many individuals depend on smartphones and so many functions, and the digital evidence continues growing. A forensic examination on mobile phones grows daily and is seen as a research activity in analysis on the different types of phones plus the kind of information they contain. The type of information stored on the phones grows since their processing power plus the storage size always increases, and the device, therefore, functions well with social media applications. We aimed to examine all the current methods used in the forensic examinations of smartphones, especially android phones.
Introduction
Forensics is an art where science is being used in providing facts or, in short, is the application of science to law. It’s a technique used to identify, recover and reconstruct evidence. Instagram and Twitter are among the most popular social network sites that are used as mobile applications. These applications have many followers who are registered as users compared to other social networks (Pittman and Reich (2016). Social networking applications allow people to capture and share videos and photos within the platforms for exchange. The users of these sites make registrations using a unique id and password so that they can log in and get accessed to meet their friends from all over the continent; besides that, they have got options of getting their accounts with the Facebook accounts and making the same friends on Facebook find them faster thus making life to be more enjoyable. Every user of Instagram and Twitter has a newsfeed that acts as a personal notice board to receive notifications from the pages or followers they have subscribed to. The sites have also been seen providing users with additional features such as photo and video editing tools that enable users to add filters and animals to the photos and videos they create, hence more likes and comments on the users’ posts. Through such kinds of activities, the users can interact more and create more relationships. The applications provide reliable information from users to other users, which then is seen to be very dangerous. in this technological world, many people are using the two sites to meet their future wives and husbands, the couple is seen to connect freely on the sites but to forget the kinds of danger, they are being exposed to.
There are many cases of online theft that later emerge, copyright infringement, extortion, and even kidnapping/rape. This occurs in scenarios where an individual gets to trust a person they meet on Twitter or Instagram and, after that, share their personal information online. The growth of social media has resulted largely in serious cyber-crimes and many malicious activities. The instant messaging users on sites like Twitter and Instagram are being targeted by the spread of malicious codes, obtaining confidential information, thus endangering the users to losing their personal information. It’s also common to face them with separate or other smartphones during forensic analysis. Mobile devices have been viewed as the most important forensic investigation cases since they are used by people on the social media platforms like Instagram and Twitter for messaging activities and other sharing of useful information. Customized methods and techniques are to be enhanced by forensic investigators due to the difference in the mobile devices. Recently, many cases reported to the investigation agencies involving some crucial criminal activities caused by the misuse of social media platforms. Akram and Kumar (2017).
According to Lau (2017), The investigation agencies are forced to employ some of the best forensic tools to extract some vital evidence from those mobile devices of the culprits to help them get convinced while in the court of law. Unfortunately, many technologies are being developed and applications that give forensic investigators hard times for their investigation. But then this makes the forensic researchers ensure that they also keep on adding the plugins on every application and application so that the law enforcement can extract evidence from all the applications on those mobile phones, whether it’s an android phone. This paper has studied forensic tools of Twitter and Instagram on mobile phones, be it iPhone or Android. We’ve also implemented a virtual machine to automatically extract the forensic artifacts using our forensic framework environment to extract the required evidence from more than seventy different Android applications (Instagram and Twitter). The anti-forensic experiment has been discussed at the end of the paper and how it was conducted on the Android, Instagram, Twitter applications to gauge if it is effective. Finally, we have presented a few privacy issues in Instagram and Twitter applications on either Android.
Literature review
The purpose of this study is to examine what several researchers have done about the forensic analysis of Twitter and Instagram. But none of the researches has helped the digital forensics investigators reconstruct the data from the forensic artifacts available on mobile devices. Instagram and Twitter have always been successful and very many popular applications. The applications’ popularity is because of the abundant forensics artifacts it leaves behind because the forensics experts find the applications so interesting. Such applications that run alone on mobile phones can provide add-on forensics information so that it can help to identify the criminal aspects. A suspect that is near a crime and that their digital signature that is available on their installed Twitter and Instagram applications can be helpful in many cases. The applications nowadays provide a convenient one-tap login facility on mobile devices that allow someone to set the mobile phone as the users’ default device.
A forensic analysis was performed on Android phones both Instagram and Twitter applications. The focus was mainly the write-blockers than the forensics artifacts of the applications. A problem that was identified in the research is that they were not in a position to locate the actual messages on the applications, especially the database in the twitter directory “com. twitter. Android” and “com.instagram.android” of the applications where the main evidence is found. And this is the main focus of the research, to extract the messages exchanged between the victims and the accused in the applications. This will then prove how the suspects are involved directly in criminal activities such as kidnapping, murdering, bombing, raping, and financial corruption cases.
Ming (2015) used the evidence-gathering technique on the applications using the Windows operating system. His main focus is equivalent to our own research goals and objectives: to capture more evidence from the social networking devices that criminals can use in committing their criminal activities such as hacking and cyberbullying. His evidence majorly focused on relying on Firefox and google chrome by using the SQLite database and the Win Hex to find out the remnants of the users’ IDs and passwords. The researchers came out uniquely. After the criminating partaking in the criminal activity, the user tried to remove the evidence by using the Eraser portable v5.8.8.1 and the CCleaner V5.19.5633. Therefore, he performed a digital forensic analysis of the user’s hard drive to uncover any evidence. Unlike Mr. changes’ research, our research will focus on the forensics analysis of just the Android applications.
There was research on Facebook forensics conducted by a security researcher at Valkyrie-X Security Research group on the mobile applications and was done on the iPhone 3GS version 4.3, an outdated phone and very old. Another research was also conducted on social media and the instant messaging services on the Firefox OS, including Twitter and Instagram, in the year 2017.it involved using the forensic toolkit(FTK)version 3.1.2 and HxD Hex Editor 1.7.7.0 to capture and analyze the memory images on a mobile phone called the peak, running on a Mozilla FxOS. The research limitation is that the volatile memory cannot hold for longer periods. Therefore, the forensic artifacts can only be found on the phone while Mozilla Firefox is running. If the forensic analysis happens to be performed when the mobile device has been restarted, all the digital forensic evidence will have disappeared out of the phone’s memory. Every network provider has now launched its applications.
The registered users mostly prefer using the applications rather than browsing directly on the social media site it’s affiliated with on the mobile browser. The main purpose for all this is to ensure that all the users don’t have to re-login again anytime they want to use Instagram or Twitter. But rather, they use a one feature login tab. These applications have helped save the user’s credentials, such as passwords, on mobile devices. Mobile apps such as Twitter and Instagram have their credentials saved on the user’s mobile and physical storage. The mobile applications store very vital important information on the persistent storage of the device. In the research, we will examine how the complete SQL lite database file can be extracted in the different directories in both Android devices. The reason as to why the mentioned research was used in our research for review is because they had the same purpose of being able to see how social media is negatively used by criminals to spread crime and also hate speech, the forensic procedures that they took for them to reach the final step.
Digital forensic
Arshad et al. (2017) assert that this is the process of trying to recover and analyzing the content found on electronics such as computers and mobile phones etc. With the emergence of many cybercrime cases rising, plus the usage of digitalized devices, this branch of forensic has gained lots of popularity, adding to what is limited to recovery and analyzing the biological and chemical evidence during a criminal investigation. It’s an application performed by computer science and technology for proving law, hence proving high technology or crimes scientifically to obtain the evidence which would have been used against the violators of the law. Digital forensic has so many fields, one of which is mobile forensics. Thus the digital forensics is, in this case, able to find the digital evidence that can be stored on temporary computer storage and the network traffic.
Mobile forensic
This science carries out recovering the digital pieces of evidence from mobile devices using methods similar to forensic conditions (Arshad et al. (, 2017). the use of mobile phones with various types of operating systems for crime has greatly increased in number. Still, the availability of forensics for all mobile devices can help sort out criminal cases relating to mobile devices, especially smartphones. The work has focused on acquiring the best available techniques and also the forensic analysis of the devices. Different phone versions were used, plus the hardware and the software were used for the acquisition. Several methods were used for the examination, which includes the use of Hex editors and emulators. This research later gave some important concepts on forensic analysis of modern generations and upcoming smartphones; we also outlined the best technologies that were used in the correct steps and procedures and the pieces of evidence of the locations used in the storage of separate of the device that was used on the procedures. The most recent research focused greatly on the specific individual smartphones, the investigating methods that could be used in acquiring the data and analyzing the device’s internal memory, plus the data that could be used as evidence. The technique that Zdziarski developed acquires a physical –logical image of the phone without necessarily jailbreaking the phone. The best forensic method for acquiring data on a smartphone, therefore evaluated by (NIST), is the physical or logical method. The physic technique consists of obtaining add images on the smartphone or the memory inside. Thus it requires the root access of the android device, which is the SD card with specialized forensic acquisition software.
The digital evidence
This is concerning the digital crimes that help social media to commit the crime. Therefore, digital evidence is used in assisting or the persecution of all types of digital crimes. When it is not handled properly, it is vulnerable to change to affect its authenticity; therefore, all the changes will result in wrong conclusions or evidence that will not be useful.
Test Environment and Requirements
The framework below was developed in a visual studio with the help of devexpress tools being installed. These are software and hardware tools that are used in performing the forensic analysis on Android on Twitter and Instagram,
- iPhone 7plus (.12.0.1)
- Meizu Note 6
- Instagram application of version (69.0)
- iTunes application (v. 12.1)
- Android Debug Bridge (ADB)
- Microsoft Visual Studio Professional 2012 (v. 11.0.50727.1 RTMREL)
- DEVEXPRESS
- SQLite Expert Professional (v. 3.5.21.2440)
- DATABASE Browser for SQL open-source (Version 3.10.1)
- Plist Editor Pro (v. 2.0)
- Win Hex/X-Ways Forensics software
- iPhone 7 Plus a USB data cable
- Windows Photo Viewer VLC Media player (v. 2.1.3)
Methodology
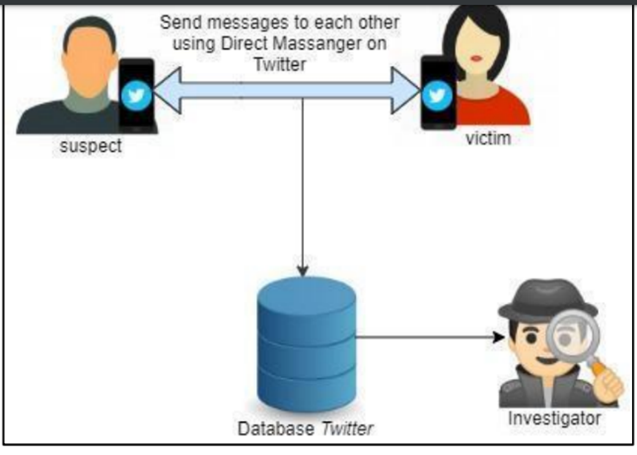
The research aims to explain the mobile forensic stages that occur on both Twitter and Instagram applications. For example, there is a research scenario where there are two people who are acting as perpetrators. In contrast, on the other side, there is a victim who is communicating via the smartphone and has previously installed the applications and therefore has conversations using the direct messenger feature or the secret chat that other users can’t use. These conditions between the offender’s phone and that of the victim are much different since the perpetrator has been rooted and the victim is not. Furthermore, the development of social media is seen as part of people’s lifestyles in today’s world. This is because there are many social media platforms, but our research bases on Instagram and Twitter. Therefore, the research focuses on looking at the artifacts of Instagram and twittering on any android phones used by practitioners to find the evidence on the mobile device.
The methodology used in the research is that of Angalano et al. it was chosen since it focused on finding the location and folder of the artifacts and interpreting the correlations of the artifacts. Manual forensic examinations were conducted on the applications and most of the virtual machines later created. Thus it was decided that the examining the differences when one is using different browsers, different scenarios are employed, and each of the scenarios employed used Instagram and Twitter with separate browser. This is Google chrome V5.0.2704 and internet explorer V11.0.010586.our research focuses on the data remnants available on mobile phones after the user has logged in, the photos uploaded, posting of messages, tagging, comments, and likes on the applications. The research tries to find out the username, password, photographs, and messages but also try to create circumstances that can stimulate the user running the portable eraser V5.8.8.1 and CCleaner V5.19.5633 to try to erase the evidence because of the many virtual machines that show several situations of situations to bring together data on the use of Instagram and Twitter activities because they are less costly.
The main objective of the research was finding out the artifacts that are produced by Instagram and twitter on the android phones, therefore the methodology mainly focused on exploring the artifacts that are produced by the android applications especially twitter and Instagram applications the stages that are involved in the explorations are as follows; performing the analysis functionalities of the Instagram and Twitter application, creation of the experimental designs one after the other, later extracting the results of the experiment design, executing designs of the experiments one after the other, and lastly exploring the results of the artifacts that were produced, interpreting and correlating artifacts.
Experimental environment
We conducted our research in a virtual android device environment, SQLite manager app, and the Titanium application that was used to stimulate the operating system of the android device within the virtual mobile device, which looks like the original one(Twitter). At the same time, for Instagram, there were two OS environments, one was Windows 10, which uses a Virtual machine since it’s not costly, it produces different virtual VMware virtual machines since it has a windows as its OS OF 64-bit. The second is Android 5.0/6.0 that is installed on smartphones and a blue stack virtual mobile device. The mobile device can therefore be adapted to the existing features of the hardware and even any of the android version, the bluestacks smartphone that operated on an environment of windows ten which had virtual computer and made the android version 6.0 to be chosen after the installation of the blue stacks virtual mobile device software on a computer. But also there must be three browser versions which are Chrome, the Explorer and Firefox were then installed on the Windows 10 operating system environment and that all the browsers both had the normal and private modes of browsing which were used in browsing of Instagram and twitter pages. Whereas the android versions 5.0/6.0 required the installation of the Instagram so as to run the feature directly.
An analysis of the functionalities of Instagram and Twitter applications is carried out, and the following were the results.
- The application was used for posting. This involved the sharing of photos and videos. The feature is useful in providing details and important information of the lifestyle of the user of these applications or as evidence of a certain crime.
- Storytelling is used to share the daily stories of the user, and thus the feature lasts for about one day, then it expires. In addition, it provides the information that is somehow related to the presence and absence of all the acts committed; hence these can be used in tracing the user of the application.
- Sent direct messages like the texts, photos, videos, and the video notes that are sent on the other accounts and when the user can video calls. The kind of feature provides detailed information on the communication of the user and also gives insight into the mind of the user of the application, which is used as evidence in finding the history and traces in situations when a crime has been committed.
- The feature is also able to share videos that are longer than a minute on the page of the user account, which is similar to that of the posting feature.
- The feature of searching and exploring which is used in finding the contents that a user might find good on the accounts on the other accounts that have no followers and that this is seen to be important in finding all the evidence of persons trying to impersonification and also the theft of the account identity hence be able to provide the information that is related to the user activity.
The reproduction of evidence in a case where there is a dead forensic analysis, among the major differences that arise among that of computer forensics and mobile forensics is the level of productivity of the evidence found in the cases of the dead analysis. This is because of the nature of the smartphones that is mostly active and its updating information on the memory that is inside the phone has been connected to the world and how it has been wired or even through a wireless connectivity. after all its observed that through connectivity that is built inside the system of the computer which are limited when they are compared to the developments of options of connections on the smartphone. This are addressed on live and dead computer forensics due to the availability of the connectivity options.;
The operating system and the file systems of the computer forensics investigators are seen to be familiar with the operating system and this makes the investigators more comfortable in working with the computer files system since they are not conversant with the Operating systems of the mobile phones the difference seen between the mobile phones and the computer is seen between the medium of the data storage. Also, a volatile memory of the phone which is used in the storage of data is riskier than the hard disks of the computers. development of the forensics in the mobile phones is always a hard task since the mobile operating systems are always enclosed except the phones that are Linux based. Most of the OS developers, forensic tool developers, and the mobile phone manufacturers are not in a hurry to give out information about the workings of the codes since they think that their source code as being a trade secret in the market.
Design experiments
These are all the activities that are based on the applications; below are the design experiments that were carried out during the research; log in to the application (Instagram or Twitter) depending on the credentials of the user, then he/she follows two other accounts, the user adds one of the accounts they follow to become friends, there is the exchange of messages personally but also in groups through the direct message feature. This consists of either texts, pictures, audio, or videos. The user then uploads photos, videos, comments on the other posts from other accounts and deletes all the messages sent directly.
| No | Artifacts | directory | path | content | |
| 1 | The account information of the user | Shared_ Prefs | /data/data/com.instagram.android/shared_prefs/com.instagram.android_prefernces.xml | User ID, account type, username, full names, the biography and the time when the user accessed the account plus the URL of the profile photo. | |
| 2 | Contact list | Following
|
Shared _prefs | /data/data/com.instagram.android/shared_prefs/com.instagram.android_prefernces.xml | |
| followers | /data/data/com.instagram.android/shared_prefs<IDaccount>_usersBoostrapSerive.XML | On the finding friend tab about user information. | |||
| close friends | |||||
| 3 | posting | photos | media | /data/media/0/Pictures/ Instagram | Photos uploaded |
| Videos | /data/media/0/Movies/ Instagram | Videos uploaded | |||
| stories | files | /data/data/com.instagra m.android/files/pending _media_images | stories and photos uploaded | ||
| /data/data/com.instagra m.android/files/render ed_videos | Stories and videos uploaded | ||||
| 4 | activity | comments | – | – | They were not seen in the local storage system of the mobile device. |
| likes | |||||
| 5 | Direct message | database | /data/data/com.instagra m.android/databses/dir ect.db | Recording messages on the Direct Message. | |
| photos | sent | cache | data/data/com.instagra m.android/cache/origin al_images | Messages send in form of photos. | |
| received | database | /data/data/com.instagra m.android/databses/dir ect.db | Use of the URL information in the message column. | ||
| videos | sent | files | /data/data/com.instagra m.android/files/render ed_videos | Videos message sent | |
| Voice notes | sent | cache | /data/data/com.instagra m.android/cache/ExoP layerCacheDir | Voice notes sent | |
| received | databases | /data/data/com.instagra m.android/databses/dir ect.db Using URL information in the message column | /data/data/com.instagra m.android/databses/dir ect.db Using URL information in the message column | ||
Dealing with deletion
The device’s local storage is used to store the deleted files, such as photos, videos, and voice notes. In contrast, on the other hand, the recorded messages are stored in the database deleted, except for the video/voice calls. Regardless of being deleted, the SQLite manager generally keeps the messages of the deleted data.1. unallocated blocks, and 2. The efforts put in recovering the deleted records are the free blocks by the use of the SQLite parse GUI by Mari Degrazia. The results show that not all the deleted data records can be successfully recovered. This happens because some deleted records are vacuumed or defragmented by the SQLite database.
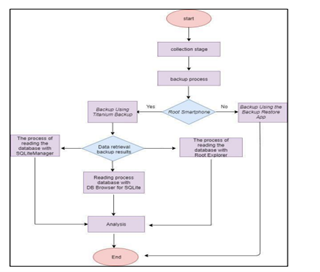
Figure 1.0: stages
Research stages
The methods are carried out sequentially following the right procedures to obtain the correct data, and the stages involve, Identification, collection, examination, analysis, and reporting.
Identification
Thakur (2013) asserts that it is a process where there is a preparation of the equipment to be used in the investigation. At this time, it’s the smartphone alongside a data cable from the victim, and the perpetrator is much secured. But, again, to protect the authenticity of the evidence. In digital forensic analysis, this is always regarded as a stage of the walkthrough of the scene where the crime had occurred. Then, after that, identified the hardware or software to be used for the collection.
Collection
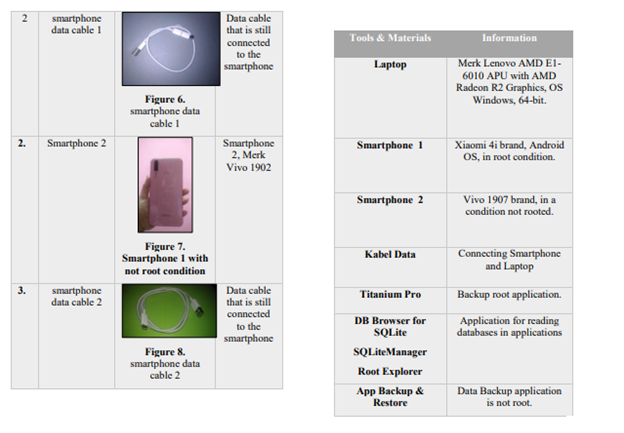
A smartphone with Twitter and Instagram applications is used as a communication tool used in investing the cybercrime. After that, a data cable is used by the perpetrator to charge the smartphone. Finally, the data cable connects the smartphone to the computer, which is used as evidence. The below table shows the evidence that is collected. It’s also regarded as a process of acquiring the disk image for the collection.
Figure 2.0 smartphone with root condition
After collecting the data successfully, the data is given to the investigator for the investigation to begin. The FTK Imager for the acquisition purpose and the for the examination purpose, the FTK imager is always considered as being fast and reliable imaging tool. The size of the disk was to be 25GM. A raw (dd) bit by bit(physical) image was also needed to be saved into another partitioned drive but just on the same system. The Identification of artifacts and its examination was carried out in a system that was considered to be live is considered important. We executed the process of examination on the storage media image so as to reflect the real picture for the purpose of integrity. Therefore, the digital hashes of the collected evidence were used for integrity. The monitoring process was done initially to get the locations of the artifacts; the collection was specified to certain folders which the process monitor identified, but we used the image that was from the disk image because our biggest intention was studying the space that was not allocated for the deleted artifacts as well.
Examination
According to Thakur (2013), This stage checks the data on the electronic evidence of the cybercrime. It is carried by performing the data backup process that exits on the smartphone. The process is where the data backups using the Titanium backup tools for rooting the mobile device and app backups and restoring non-rooted smartphones. The picture was viewed for Instagram and Twitter artifacts. The collected artifacts therefore were checked and differentiated by analyzing their importance/usage in the contemporary world, the results are as follows;
Instagram artifacts
Most of the Instagram artifacts were seen from the location as in windows 8.1. the number of SQLite database files, including the friends, stories, friend requests, messages, were from the \AppData\Local\Packages\Instagram. Instagram 8xx8rvfyw5nnt\Local State\* Instagram ID\DB. Many of the files are readable through the DB Browser for SQLite. the interesting message body is found in plain text, and thus the only sender was visible in the database for messages, but the recipient of the message and their Identification could easily be done with the help of the threads. DB in corroboration. The location of the senders was also seen in the messages .db.stories that the newsfeed was seen on the timeline of the user and that the list displayed the permissions given to the people ,be it that they are required to send the friend request.
Twitter artifacts
Every user is associated with their profiles and information that has their name, status line, and a picture. The profile of each of the users on the application is then stored on the central system, which can be downloaded with the other users that are included. Twitter keeps all the texts that were sent or received into the database msgstore.db because the analysis results in ensuring that all things are possible to be reconstructed during the time when the user had exchanged so as to help in knowing the time when those messages were received by the receiver. The data carried with it, the set of users that are involved in that conversation, and lastly, whether and when the mentioned recipients have received it. the android application was having two files that contained data which would be of importance to the examiner eb8899d553cf563080453f9a366600de1dcf6286 and f77282c60c3cee3ffce4a8bba2760fd954d4921f.the first file that held the user information of the Twitter application included the username, the URL link that is seen on the profile of the user and the tweets and stories that were earlier posted plus the timestamps, whereas the second file had all the information of the user of the account with his details that had been taken from the profile pages. Also the folder artifacts had two files that had data that was significant to the examiner; SQLite file 48598f280bb577d1e68aaddadccba35c54acbb48 and file e5cb579c7bdf12b996bd865ecf6290ab94374abd.the SQLite file had the username of the user and the comments that the user had posted earlier on the pages of the other users.
The Android’s forensic examination
This is a section that describes the acquisition and the forensic analysis of the android phone. After rooting the phone, the data files were accessed easily and even backed up the programs that could be important to the investigation. The installation of a rootkit (CF-Root XW) allows the user to have the privilege over the Android operating system, therefore, helps in bypassing some of the limitations that the manufacturer had placed on the phone. A phone that is rooted always allows a person to access all the folders that have been protected by the system which is holding the data of the user. Example data/data.directory) and all the backup files in the directories which are in the phone. they mentioned files therefore have a potential of holding very large files, which are useful in the investigation. android phones lack a management that is somehow unified and also the backup of the device on the SD on the server of the phone. The kind of application used is MyBackup of version 2.7.7) which is well installed on the android phone that is undergoing the test. a New microSDcard was inserted on the phone and therefore the MicroSD Selected for the purpose of storing the files after backup has been completed, after backup, the Micro SD CARD is removed from the phone and then attached to the workstation so as to allow examination to begin on the files that have been backed up and lastly analysis .My backup application was used in acquiring the files that are associated with the twitter application and hence the creation of a backup directory on the MicroSD card. below is the path that was used \rerware\MyBackup\AllAppsBackups\[AppsMedia_yyyy_mm_dd] \Apps. This had a directory com.twitter.android-134.zip and its associated with the twitter, its examined and known that it has a folder that is called databases which also has Three SQ files. the first one was 342525691.dB which was having interesting data that stored all the records of the tweets that were posted earlier plus the photos, friends, users, and the other data that is associated with the events that occur on the twitter application. The records were used in storing the ID of the user, the timestamp, and the contents of tweets posted earlier plus the posting on those websites.
The structure of the chat database
The msgstore.DB database contains the following three tables:
- The messages that contain a record of any message that had been sent or received by the user of the application, we made things easier by classifying the fields of the records; \
- Those for storing the attributes of the message
- The chat list that contained a record or any of the conversations that were held by the user (the conversation consisted of set messages that are exchanged by a certain contact)
- SQLite sequence, which is used in the storage of the housekeeping data used internally by the Twitter application since there is nothing that was reported here, thus no evidence value.
The twitter generates copies of the msgsstore.Dg database. All the backups are full copies of the information found on msgstore.DB but yet to be synchronized with it. hence this is always important when it comes to a point when investigation is being conducted since they store messages that might have not been deleted earlier in the chat database; therefore, the backups are encrypted with AES 192.
Analysis
This stage of writing the results obtained from the investigation process and the data obtained from all the investigations. This report contains the Identification of the extracted image file from all the evidence of the smartphones, both rooted and not. This report will be brought to the trial process and thus must conclude all the evidence found in the physical form obtained from the forensic process.
Reporting
These are the results that are obtained using the DB Browser for SQLite manager, the root explorer. This data was then obtained successfully and thus acted as digital evidence from the smartphone attached to Twitter and Instagram applications.
A research of the finding evidence that occurred on social media Twitter and Instagram in situations where a perpetrator sent hate speech or abuse to a victim through the messenger and the investigator revealed the evidence.
Examination
This stage is where the backup stage is installed on the perpetrator’s smartphone and the victim involved in the crime.
A backup process on the rooted smartphone (twitter application)
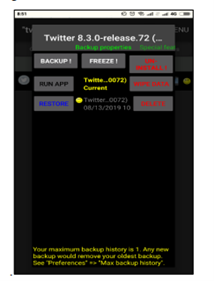
The use of the titanium application does this. The process of backup runs successfully by the use of the application, as shown below.
Figure 3.0 use of titanium application on Twitter
The user can only see the process of the Twitter 8.30 version.
A backup process on the phone that is not rooted
The app used in performing backup on phones that are not rooted is referred to as the App backup restore application. This is an application that can be used to backup and restore the installed apps.

Search for evidence on the rooted smartphones
The main reason for carrying this process is to obtain evidence in the form of a conversation between the perpetrators and the victim involved and the evidence that can be identified.
The process of searching for evidence with DB Browser for SQLite
Below is the evidence that is obtained using the DB Browser for the SQLite applications mentioned application also successfully obtained evidence of the conversation between the victim and the perpetrator;
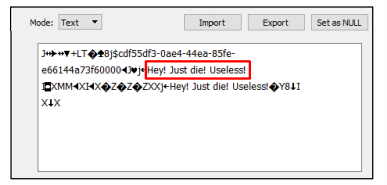
Figure 4.0 messages sent by the criminal
This shows the utterances that were made by the perpetrator sent to the victim. It was hate speech, and it was not the only evidence as there was hate speech, as shown below.
Figure 5.0 list of messages containing hate speech
That was a piece of evidence that the offender had sent to the victim after the hate speech.
The process of searching for evidence by the SQLite manager.
The applications manage to get the evidence in the form of conversation with a profile of the perpetrator, as seen below.
Figure 5.1 SQLite manager extracting evidence
The evidence above was obtained from the conversation between the perpetrator the victim when the perpetrator sends the messages to the victim. The above conversation was in the form of hate speech, and it’s a very important piece of evidence that can be used to prove that the crime occurred. Furthermore, the hate speech obtained as evidence can strengthen crime in hate speech committed by the suspect to the victim.
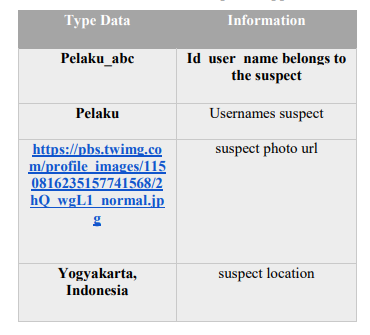
The process of searching for evidence with the root explorer
The application is installed in the form of the user identification, image, URL, and the location where the suspect is situated, as shown below.
Figure 7.0 the use of root explorer
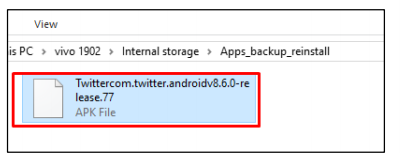
Process of finding evidence on Smartphones that are not rooted
No evidence was found from a conversation on a smartphone that is in a non-rooted condition; this was because when the backing-up was being conducted, the backups are only in the forms of applications and not the databases.
Figure 8.0 finding evidence on a phone that is not rooted
This the
Therefore, this proves that evidence found on a non-rooted smartphone in the form of an APK file.
Thus it’s possible that during the reporting, the investigator can approve that all the results /information was obtained accurately from two smartphones by the use of the DB browser, SQLite manager, and the root applications, as shown below.
Forensics analysis of Android-based application(Instagram)
The installation of the Instagram application was the first step on s smartphone,
NIST defined any digital forensics cases that are in different stages as follows: Identification, collection, organization, and lastly, presentation. The first stage, which is Identification, is where the evidence is received, then carved and later followed by trying to reduce the amounts of certain data . The organization stage, the data that had been carved, is then examined after that is similar to that of the crime scene to conclude. Finally, the stage of presentation ,this deals with bringing data in a way that a jury can understand easily.
Extraction of data from the android devices
This involved the pull command of the Android Debug Bridge(ADB) that was so helpful in extracting the contents of “com.instagram.android” this was done to perform that manual analysis of the changes in the contents of the package when the different activities were being performed, like the creation of the user, sending of messages and sharing of pictures via the Instagram application.
Manual analysis was so important to locate the files of interest creation of two usernames to help generate the forensic artifacts in the Instagram mobile application database. The examination of the Instagram on android phone (com. Android. Instagram) in the data app stores all the directories and the needed files. The database directory and the shared _ prefs directory contain XML files that have the user’s full names, their Identification, and all the other important information of the Instagram account user. The data directory contains all the messages that are directly exchanged between the user and the other Instagram users,
The anatomy of the “com.instagram.android_preferences.xml” file and, therefore, the snapshot of the file has been presented below and the listing of the important forensic artifacts.
Figure 9.0 snapshot file from the artifacts
The XML file above contains very important tags used in storing the information that the user of the Instagram application. This information was stored in a key-value pairs format since it was easily extracted using any programming technique. In our procedures, we ensured that we utilized the Visual studio tool to program the extraction of the forensic artifacts. The XML files and directories contained the information of the app user and the cookies. The other directory of our interest was the database directory, which had all the direct messages and was in a file named as ‘direct. DB, which was exchanged between the user and the other Instagram users, was of help in giving the forensic information. The investigation of the artifacts left by the application and the tools that assist in extracting the artifacts. Zellers have been used to examine the tags that are created in the other Myspace source-code pages and are used in creating the focused artifacts keyword searches. Most of the social applications are connected with phones, especially the social networks, so as to give the forensic examiners a position to find out what is relevant evidence on the suspect’s smartphone. The database on the memory of phones is used to store the names of friends, ID numbers, and the phone numbers on the list. Some directories are related to the Twitter application are also seen in the database. The folders are for storing information about the attachments that had been sent on the tweets, the user name and all the tweets, plus the images and the time when the posts were posted on the twitter application. A forensic examination on the image of the phone showed that the friends information is always kept in the database that has contacts (contacts.DB) since the phone saves the updates on the application with the phonebook. Its evidenced that the phone stores all passwords plus the updates that are happening through the application. All the activities that are performed on the application are then stored on the phone device. More researches that are focused on recovering of the vital information that is related to the usage of the applications. The previous one was fixed in recovering information related to the use of the social media applications like twitter and Instagram.
Analysis of IM applications on the smartphone has great works that have been published in literature. comparison with the earlier works, its evidenced that our contribution has been of importance and considers all the artifacts generated on Twitter and Instagram but also presents complete analysis of the mentioned artifacts. Lastly we explained the artifacts are correlated so as to come up with types of information and have a value to the actual places after being sent by the user account, if at all the user had joined or Had left a group after a long period or if the user has been added to the phone list of the user of the application in question.
We observed that the message-id and the user id are the ones which are the current user used to identify the current Instagram use of the mobile application, since Instagram stores a copy of all the contents on the server-side. Therefore, every message typed on the application is assigned a server item-id as the contents that reside in the Instagram application directories are therefore assigned the client –item-id. This means that the recipient-id timestamp is used when the message has been well received. The message type is for distinguishing whether it’s in the form of text or audio-video message. If it’s a text message, it is stored in a text field, or if it’s an audio-video message, then the link of the multimedia message is stored in the message field. The text is kept empty since it has no value that has been store in the message field is an important element since it is used in storing the most valuable forensic information for any messages regardless of whether it’s a text or an audio-video message.
Figure 10.0 messages from the user account and the victim
The above information is stored in JSON format. Once we identified the available information in the different files and different directories, we extracted the information in our digital forensics ready framework software. We then created our local database to store the forensic analysis artifacts in the directory. We’ve shown below how we managed to extract the valuable information from those files to be stored permanently in our workstations as the database evidence.
Figure 10.1 extraction of forensic analysis from artifacts
Forensic and anti-forensic tools
Different forensic and anti-forensic tools and software for the different situations that were used. For the post experiments of a web version, a detailed forensic analysis was prepared by the of the WinHex on the VMDK, VMEM on VM and the DB files of VM were then analyzed. The physical smartphones use a normal SQLite editor in reading and analyzing the DB. Files that were on the mobile devices. The information in the folder was all removed to carry out anti-forensic analysis using the Eraser portable software. A thorough cleaning was also performed on the environment, including the cookies and the index.dat, the history files and the internet cache, network temporary files, and the memory dump was also accomplished by the CCleaner software; hence a forensic analysis was done by the WinHex and the DB Browser for SQLite.
Elaboration of the experiment
The experiment was separated into five scenarios as per the browsers or an Instagram app so as to ensure that the integrity of the evidence so as to avoid interference between the pieces of evidence. Designing of the environment in the previous section, we were able to run the application and the features, including the log in, the pictures were uploaded.
The first scenario
Google chrome
The VM was installed on the google chrome application and we logged into Instagram so as to be able to run some features while using the normal mode of browsing and later private mode so as we could be in a position to identify the evidence and later the VMDKL file plus the virtual machine were in a position to search for the evidences that the user of the application had left behind on the phone while using the applications.
The second scenario
Internet explorer
We used an internet explorer as the browser and the experimental environment, and the steps are the same as the one in scenario one.
The third scenario
Mozilla Firefox
Mozilla Firefox was used in this scenario as the main browser and that the steps were repeated as the way they had occurred in step one.
Free Opener
A file that was versatile that was supporting the documents and the multimedia formats, an eraser that is portable Data removal tool V.5.8.8.1 CCleaner to delete temporary or the unwanted files of version 5.195633 Recuva portable in restoring accidentally files that were deleted of version 1.52.1086
The fourth scenario
There was a VM virtual machine in this environment; the blue stacks virtual device was used to install virtual devices using the blue stacks. So, therefore, we logged into the Instagram app to run various features and identify and analyze the VMDK file and the VMEM file of the virtual machine and search for the virtual machine that the app users left.
The fifth scenario
Android smartphone
We managed to log in the Instagram application on the smartphone that had been installed on android version 5.0, and we run several features so as to manage searching for any material that would act as evidence that was left by the user.
Findings of the scenarios
Scenario one which was the use of the google chrome
In normal browsing mode
The WinHex was used in searching for the keyword www.instagram.com/ plus the name of the experiment account; this resulted in finding out the nickname of the account which was used during the experiment. The keyword Gramblr and then the photos were later uploaded on the application and hence found in the path C:\ProgramData. In addition, the images and the photo that had earlier been modified. The keyword /?Taken-by the URL which had been used in uploading of the photos was the one that was found, but the URL that was for uploading the photos was seen to have a fixed format https://www.instagram.com/p/photo coding/? Taken by=photo account. There was another search by the keyword gramblr.DB which displayed the location of the database in which the Gramblr is found in the computer in a path named as C:\ProgramData\Gramblr\gramblr.DB and that this kind of file is only seen by the DB Browser for SQLite hence the password for the account that was used for experiment could easily be traced. A search by that keyword showed all the history/traces of all the comments and posts that were left by the user of the account either on the pictures of the photos of the account owner. Its very hard to locate the evidence by the use of the time in which the photos were uploaded and also the contents that were posted with the behavior of the user through tagging of the other users plus following other users accounts in situations where the WinHex was used in searching of the keywords, time, timestamp, tag, follower, like, label and the other accounts.
For the situation of the VMEM file on the memory of the device for the forensics analysis, the experiment that we performed above resulted in some of the evidence as the same as that of the VMDK file. But in case the search had be done by the use of the keyword evidence hence the timestamp liking’ by the account used for the experiment could have been founded easily.in the case of the LIVE deleted data anti-forensics all of the files folders of the account used for experiment account under the Gramblr path were deleted by the use of the eraser portable and then the Gramblr was deleted and permanently removed from the control panel. But also the cleaner that was used in performing the cleaning of the data like the cookies, index. Data, the windows logging files, the history records, internet cache, network, temporary files, memory dump, and any other important information. The very same forensics that had been performed in procedure 1 and 2 was repeated, and the results proved that there was a decrease in the list of evidence found. The memory was seen to keep the paths of the original photos that were uploaded and the files which were later modified. But then the real photos were deleted, and hence the contents which were original would not be accessed if the experiment could be repeated. The final results proved that the evidence could not be recovered from the memory that was used.
When the mobile device was powered off and later restarted, the analysis proved that the remaining of the evidence that were present in the user account like the nickname, the paths of the original and the uploaded files thus the forensic analysis showed that the evidence except that of the nickname could no longer be traced and thus this was followed by the deletion but the photos had all been cleared and that the contents that were original and were existing earlier were not accessible.as the case of the memory, the results of the forensics were still the same and lastly the Recuva Portable was used to restore all the data that had been deleted plus all the files. The nickname could no longer be located on the memory. The keyword www.instagram.com/ in the efforts to find the remnants of the user account and the password for the account .hence the experiment account plus the nickname had been found as shown below.
The Keyword,gambler.DB is used in finding the remnants of various locations on the C/program Data\Gramblr.DB.The account and the password were then found on the configuration table of gramblr. DB as shown below
The use of the Keyword gambler to find the remnants of the photographs on C\Program Data\Gramblr\pomeloojiayi is shown.
The photographs shown can only be found by using the keyword “/? taken by=.”
The Keyword for the text that was used in finding the remnants of posting the text was(TEESTT) as shown.
We also used a different keyword at such a time, timestamp, tag, like, and label, in finding the remnants that could not be found with such keywords.
A google with an eraser and a CCleaner
During this, we restarted the virtual machine and logged in to Instagram. Uploading of photos, posting on the application, and all the other actions are deleted. The Gramblr data of the application are therefore deleted with a portable eraser. We tried to run the CCleaner to delete the browser data remnants with the password, cookies, and history. The remnants are used in finding www.instagram.com Keyword.
Private browsing mode
Immediately after completing performing the experiment on the private browsing mode, the memory forensics analysis showed that the main contents were on the normal browsing mode but had then disappeared later. But the evidence of posting the contents and the tags were left behind. The other evidences were similar in the normal and also browsing modes. We observed that in the memory there was the content of posting and the hashtags that were found in the private browsing mode while not in the normal mode. The experimental account had a nickname that was present in the normal mode of browsing but also disappeared in the private mode of browsing. Recuva was used for the purpose of recovery all the files that were deleted, and also there was a repeated analysis that proved that the evidence which had been deleted could not be recovered into the memory. There was also performance of steps of deleting the browsing mode and the analysis proved that the memory had paths from the original and also the files that were uploaded earlier. The evidence also had the experiment account which had the posting and the content history such as the hashtags and the websites that had been uploaded like the photos and texts but had been deleted from the memory. The smartphone was then powered off and then restarted only to discover that the contents like posting of photos, comments made on other accounts, texts, and hashtags were still seen on the hard disk, but also the evidences were removed from the memory of the phone. Completion of the process of deleting its observed that both the memory and the hard disk had the evidence hence concluded that the recovery process cannot retrieve the deleted evidence.
Finding scenario 2
The internet explorer in the Normal mode
The VMDK file which was in the computer memory that was used in forensics analysis and there were the keyword searches that were used in the WinHex which revealed the evidence was on the Chrome browser. The browser was also helpful in finding the information that was very vital in regards to all the posts in comparison to the Chrome browser. The use of the keyword text proved that there was no evidence that could be found in the comments sections; hence there were searches by the use of the keyword like timestamp, tagging, and liking which could not find the evidence in the behaviors of the users of the account.
Whereas the VMEM file which was based on the memory of the computer of forensics and the same evidence was in the memory as added tag of TRAIN hence the name of the user of the account who was responsible for sending the photos or messages was obtained. Keyword text was used in finding the comments that were left on the account for the experiment the evidence found includes the comments, timestamp, and the person’s name that had left a comment on the account. In the situation of LIVE data for the anti-forensics, both the Eraser portable and the CCleaner are used in clearing of the data. Upon completion of the analysis, its observed that the memory had the remnants of the Instagram account, the nickname, the browsing traces and the URL that had been used for uploading photos. The photos had been observed to be deleted, and therefore the original content could not have been known. lastly, the Recuva portable is important in the recovery of the evidence that had been deleted and cannot be retrieved. After powering off the device, the memory forensics showed that the account used for the experiment, its Nickname, the website used and the uploaded files were not able to be known and that there was no any kind of sign that there existed any kinds of information to be used as evidence in that memory.in the recovery of the files that had been deleted earlier, the Recuva portable was used hence the results proved that at the beginning of the experiments there were no traces of the browsing history.
Private mode
Completion of the experimenting with the use of the private mode it was found that the memory and the experimental account shared the Nickname of the user account, the history of browsing like the photo uploading and that the memory contained some evidences that was in the experimental account like the ID of both the original and the revised photos. The memory revealed that the account used in the experiment, the Nickname, and the photos that had been uploaded, but the pieces of evidence in the experiment account that was originating earlier had all been deleted. After the Recuva portable had been used in recovery of the files that were deleted, the analysis proved that the data pieces of those evidences could therefore not be recovered, but after we shut down and restarted the memory was seen contain the evidence of the website and the browsing history of the photos that had been uploaded earlier. But finally the main evidence that was in the memory had all disappeared, after the process of LIVE deletion, the experiment result was still the same as the previous thus the evidence that had been deleted earlier could be retrieved through the procedures of recovery as mentioned earlier thus this was discovered that could not have retrieved the evidence that was deleted.
Findings of the Third scenario
Mozilla Firefox (Normal browsing mode)
The data that was behind the equal sign could be helpful in ensuring that the data could be used in determining if a user uploaded the photo or he/she had browsed some other photos from the other accounts, hence the password of the account used for the experiment could be viewed plus the exact time when the photos was uploaded and the contents that was in the sent texts but also the behavior of the user like tagging others and leaving comments but also following the accounts of the other users and this could be searched by the use of WinHex by the use of keywords like timestamp, tag, liking the follower and the account number of the other users. All the searches then could not find the availability of any of the evidence that are leaving the comments and that of the likes of the posts, likes and also following the account used for experiment by any other account that had been left on the memory but also the evidence found on the hard disk but also has an extra message which is found by clicking the like button on the other user like posting. The L/p/photo Encoding sequence/? Taken by + Experiment account which has a description that is much unique meaning that the user himself/herself like the video that had been uploaded during the experiment. The memory only contained an Instagram account, the number, the Nickname and the browsing history.
Findings of scenario four
The Bluestacks virtual device
In a virtual machine environment being installed on the virtual device by the use of the bluestacks, we then managed to log into the Instagram application so as to run various features so as to be able to analyze the VMDK and the VMEM which was from the virtual machine but also be able to search for the virtual device that the user had left behind.
- In the L/p/photo Encoding sequence/?taken by =the experiment account there were cookies and the data files from the web which were found and thus the files were only to be viewed by the help of the SQEditor on the experimental account, the password and the android version number that was found in the cookies but observed that there was no evidence found in the file data.
- Completion of the deleting the photos that had been uploaded on the application the smartphone then remained with photos from the path SD/card/pictures/Instagram this is after the clean files were found in the path sdcard/Android/data/com.Instagram.android/cache/’ but none of the mentioned files had any form of evidence.
- We then copied the Instagram files and the bluestack from the virtual machine and placed them in an environment so as to undergo an analysis. An app.json file is seen in the path bluestack/userData/Gadget,” which had an account that was used in the experiment plus the password and the version number of the android phone.
Findings of scenario five
Android smartphone
On the path “data/data/com.instagram.android/app\_webview /” showed the cookies plus the web data database and the SQLite Editor was used in viewing the files and hence there was no sign of any kind of evidence from the files. Because of the high demand on the digital forensics in the normal browsing modes for investigators, we tried to draw a table clearly which showed the three browsers and the nickname of the account name can easily be found in the keyword www.instagram.com but tracing the Instagram word cannot be found but we found a keyword viewed garbled its thought that will eventually bring a password. The keyword used in uploading the photos was Gramblr and /? taken-by= as for evidence of the timestamp and the other users that were tagged were found. We also found the Instagram history on the browser but none of the browsers showed the last login except the Firefox browser. The comments were then looked in the keyword by the text and /? Taken by=. And for the like details so as to click the Instagram users and what they had posted earlier. Google chrome was found by pressing the keyword ‘like’ whereas Firefox through L/P/ and the internet explorer L/P/, IE but could not be found. The three browsers were not in a position to find anyone following the account of the user, but just the internet explorer had the evidence of all the users while making the posts and all the comments on the accounts of the others and the like button on the posting. The browsers also were not able to find out anyone who was following the message of all the other users who were following the account that was used for the experiment. But the case of the Virtual smartphone device, there were there evidences which was found that included the last time the user of the account logged in, the exact path where the pictures were stored, but this is just possible for the smartphone devices only.
A social media experiment
Our main focus in the experiment was to investigate the applications(Instagram and twitter) but also the three social media web. There were images that were successfully captured and some of the forensics evidence was worth trying to recover and later trace i.e. then began tracing the artifacts that had been brought about by the mentioned applications and all the URL that were used in those websites. Our second step was trying to find the ID name which was captured during the login process in the application.
Phone images
The images present on the android phone was opened by an access data forensic toolkit(FTK) of version 3.1.2 plus the HxD Editor of version 1.7.7.0 we conducted the analysis in a manual process by searching keywords which are seen to relate to the experiments that had been conducted earlier in a forensic manner. There was a binary search that occurred by keyword of an application. The above search gave rise to the application, and it was well installed by the Mozilla Marketplace. We were not in a position to locate any keyword from the images because the factory settings were not from any of the applications that were installed earlier. This is what was seen when we had the first search on the twitter application.
Figure 11.0 twitter keyword
The second search was also performed to find the URL for the social media mobile web. Mobile web is much different from an application. We did not have to install it but only needed to browse using preinstalled Firefox browser, the table Twitter URL was found in the images, and the results have also shown that the person who had visited and the time plus date.
Figure 11.2 persons who visited the account
The third search was to find our profile name and the user ID once we logged into the application. The profile name was seen to be different from a username. The username was used for logging into the social media with a profile name, which was the same as the one displayed in the account. The figure below shows the profile name, user ID, and Instagram profile path we managed to find.
Figure 11.3 profile name and the ID of the user account
According to Anglano et al. (2017), One of the most valuable information that everyone wants to protect on Instagram and Twitter or any other social media site is the account credentials. In an event where the account credentials fall into the wrong hands, one can therefore log into the account and then pretend to be us. They might commit crimes using those accounts; persecutions will be on us and not them since they have not conveyed their own identity. The next search was to find the username and password used all along during the login process. The rules for username were a bit different between social media. Instagram and google + accepted only one email as a username, while Twitter can accept either email or a selected string.
The activities and communication on social media have been important to forensic investigation due to the important information they provide. For example, the communication pattern experienced on Instagram and Twitter can identify any kind of cyberstalking. We are also capable of investigating if there is any sexual harassment had occurred. In the next search, we were trying to find the activities that could be recovered in the experiment; we used a certain communication from some images that shows a communication string that was used earlier in the Twitter experiment, which was appearing in the search results.
The search process was executed by using a detailed step with the phone images accordingly. If the above information was found and therefore recovered successfully, we considered it as right. After all the searches had been completed, the findings were recorded as shown below.
Figure 12.0 findings
In general, all the social media applications keywords will appear in the search upon the installation; the experiment results show that changes were made in the application during the installation. The same search occurred to the web URL keyword. After visiting the web, the Keyword will be stored in the history of browsing, and that includes the date and time stamp after selecting the login tab. Unto the selected social media, all the profile names were recorded on the phone except that of Google + mobile web. As for the social media username, Twitter application and Twitter mobile web were able to retrieve the messages and the photos posted earlier. There were no passwords seen on any of the social media, but also in concurrence to that, all of the communications and activities only appeared on Twitter application and the Twitter mobile web, and that there were no activities that were seen on Instagram and the Google. Therefore, some of the data remnants were retrieved from the Instagram and the Twitter application, respectively.
Phone and memory images from Instagram and Twitter applications
There was an analysis of the images on the memory that were the same as the previous analysis. We have been able to perform the keyword search by the use of the preparation steps. The search we repeated severally but only for the value that does not appear in our first using the phone images. The memory images were also opened using AcessData FTK and HxD Hex Editor. For this analysis, we focused, more so, on the social media credentials and communication activities, but because most of this part was not recovered from phone images for analysis. The table below the Twitter credentials that were used in the login in our search attempt.
Figure 12.1 Twitter credentials used before
The search continued more and more on the social media credentials and communications activities. The table below shows what evidence can be retrieved from both the images and the memory images.
The analysis showed that all the credentials especially the passwords could not be seen on the phone images but still we tried to retrieve in the memory images but except that of Google+ of all the communication activities but all in all we could not find the keyword that was matching the Instagram and twitter application. We checked Instagram and Twitter so as to find any details; hence the result of the study was suggesting that all the activities that are associated with communication on the applications for FXOS had been encrypted on had been stored on the servers only.
Instant messaging investigations
An application that is first in instant messages on the mobile web was acquired so as to help in the instant messaging experiments and the investigations. We therefore explored all the artifacts that had been generated by the two applications and the URL that was involved on the mobile website. We then tried to find the phone number of the user of the application which was used during the registration process. Lastly, we aimed at getting the registration codes and all the SMS or the call verifications that were recently on the phone during the registration process. Fourthly we tried tracing all the activities that had occurred and that had been captured in the images, and lastly, we checked for the data that had remained after the completion of the uninstalling of the application in use and if there was any of the history left in the folders.
Instant messaging Phone image
The phone images were opened separately by the use of the access data forensic toolkit(FTK) of version 3.1.2 and also the HxD Editor of version 1.7.7.0.the search was conducted manually on the several keywords that are related to the experiments that had been performed previously in a forensics manner. The first search, which was in a binary way, was performed on the application by the use of a keyword search that was executed immediately after the application was selected it was successfully installed in the Mozilla marketplace. But then we could not find any of the keywords that were selected for instant messaging from the base images since the factory settings that we used were only from the preinstalled applications and yet none of them were used for the investigation.
Memory
The remnants of the memory can also be located on the memory but except a URL used in uploading photographs. The remnant of the label (|TRAIN) can be traced with the pameloojiayi Keyword. The accounts that have the like option can only be traced with a keyword like. The posting of text and the time stamp can also be found only with keyword text, as shown below.
Results of the research
The artifacts for the Instagram application were identified, and the main focus was the memory and the hard drive artifacts. The experiments showed that the Instagram application on the volatile memory has proved that the critical data of the application is always present in the Random assessment memory(RAM). Thus, it could be extracted if further analysis was needed. Furthermore, our analysis has proved that the Instagram application activities always remain artifacts in different locations. Thus, this indicated that records remain in the application folder when the user has used the application. The examination of the physical memory captured indicated that the memory dumps could recover the caches of the Instagram application in the plain text; we, therefore, performed all of our research inside a Virtual machine, and thus it gave us the advantage to download the executable files hence there was no any form of any worries about any of the executable affecting the host machine, our forensic data was not in way leaked to the outside world, and thus a different environment was organized to hold all of our files in a secure place.
Below were the findings
| Category
Actions |
Google Chrome | Internet Explorer | ||
| Hard Drive | Memory | Hard Drive | Memory | |
| Password | X | X | X | X |
| Account | V | V | V | V |
| Nickname | V | V | V | V |
| Location of Uploading photograph | V | V | V | V |
| #Posting Text | X | X | V | V |
| #Label | X | X | X | V |
| Tag | X | X | X | X |
| URL of uploading Photograph | V | X | V | X |
| Comments | V | V | X | V |
| Like | X | V | X | X |
V mean found while X Means None
We identified the important information that could serve as one of the potential evidence, and we then extracted evidence from the applications. The Instagram forensics was implemented in the forensics ready framework as a dynamic to the link library. An identifier was created, and the forensic data of each Instagram and Twitter application was saved in a different folder named according to the corresponding application.in our case the Instagram, for example, was named as IMINSTAGRAM directory was used to store a copy of the files that were originally extracted from the Instagram application
The forensic software extracted and made a different copy of the files that contained the forensic artifacts (“com.instagram. Android, “direct.DB” and “burn. Instagram for the android smartphone into a folder named as an Instagram directory as shown below. The software was then used to store the database file that contained all the reports of all the relevant information and some direct messages that were exchanged between the current user of the application and the other Instagram users. The figures below show the exhibit of the extraction of the current Instagram user’s information and the messages exchanged between the other users in the application.
Below is a list view and XML of the bplist that was extracted from the BLOB object of the archive column in the messages directory
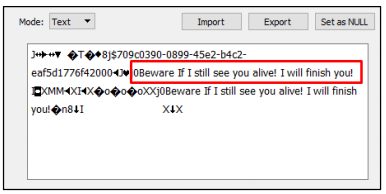
In the android devices, if one is suspected as a culprit of the currently employed digital forensics techniques could make them be convicted. The culprits may get away with their criminal activities by corrupting the directories in the application. This may be done by extracting the database located in the “\com.instagram.android\database\direct.db” path in the Instagram application. After that, the contents and later save them back into the same directory. We then stipulated the scenario and then changed the contents in the text messages placed in the directory in “direct.db,” and saved them indirectly. DB file into a path “\com.instagram.android\database\direct.db.”
We sent a message from an android phone that was hosting a “dark2539” user to Mohammed, who happens to be the other Instagram user.
Message: I am DerkTest
Later we found out that the message was located in “\com.Instagram.android\database\direct.DB” file, after we extracted the “direct. DB” file and opened the database software, we hence changed the contents that were there to “I am Wangle” after that, we restored the altered “direct.DB” file back to the android phone. After the successful restoration of the file, we connected the phone to the internet and opened the application to see whether the message that been altered was still present; Instagram maintained the original text,” I am Darkest ‘hence this proves that Instagram maintains a copy of a chat for their servers and that and thus updates the data when the user appears online. Therefore, a criminal may act smartly by leaving their phone offline; however, another reason confirms the anti-forensics technique is the “direct.DB” file that displays the actual date it was modified, the data that was changed, and this is the best evidence to a forensic analyst. The research also found out about the web version and the app versions of Instagram used in conducting the forensic analysis of the user behavior on the android phone environments. We found out that the different browsers, due to the differences in the personal issues they can lead to discrepancies in recording the user behaviors on the same social network, and this is in terms of practicing the user data, The Mozilla Firefox was seen providing the highest protection which was followed Google chrome and after that Internet explorer which provides the lowest protection on the user data. The forensic analysis on the applications is almost identical to the Virtual and physical smartphones. The differences in the framework space cause the differences that are in the storage capacity. The difference is because of the structural identity of the physical smartphones that are running in their operating systems .in the processing of investigating the cybercrimes on the applications, and we recommended that the first goal should be trying to find the account number, the Nickname, and the password of the criminal in suspect. The use of the suspect’s account number, the suspect’s operational behaviors on the Instagram application can well be searched, such as through the uploading of the photos, posting, commenting on the different posts, timestamps, added tags, and all the browsing traces. Based on the contents of that operation, the activity that is regarded as a crime or a victimization practice can thus be deducted or estimated well. Using the additional accounts of numbers discovered using the process of gathering evidence, the scope of the investigation could be expanded to find the possible victims or the criminals.
Conclusion
Globally, with the recent increase in technology usage, communication is regarded as one of the rights of human beings because communication itself is embedded in nature. The inventions of the fastest communication channels such as Instagram and Twitter on portable mobile phones. The increase in usage has led to several cybercrimes, which have resulted in several forensic analyses on those applications. We succeeded in identifying the artifacts produced by the Android-based Instagram applications and twitter; they include the user information related to those accounts of the user, the number of followers, those following, and the close friends. The data that was obtained went through an examination both automatic and manual. The analysis revealed that a couple of files relating to the Instagram path, one of the files stood out to contain a list of the followers of the user account, including all their usernames and the links to their profiles.
In contrast, the rest of the file had a list of all the Instagram users the followed by the user account that we used for the investigations. Such information is very important to forensic analysis by the investigators since it helps prove the relationship between the individuals following each other on the application. There was also another folder that was discovered that was containing the stings of the application. The hashtags, the topics searched, and all the log on when the feeds were being refreshed. But also the traces of exchanging user accounts both in messages, photos, videos, and sound recordings. The video uploads created stories, and photos were located on the device storage. As for the other things obtained during the research and the media plus messages received through the direct message were not stored in the local device storage. Still, the efforts to locate the media message that was received can only be viewed through the URL link information, which has an expiry period.
On the other hand, the files that were containing data to the path were few. Yet, a similar test on the android phone revealed that almost all the activities performed on the application, that only a single file containing the locations posted on the path was the one identified from the phone local storage. The traced data were observed related to the comments and the likes but were not stored on the local device storage of the phone.
It concluded that some of the activities carried out on these applications are always recorded on the local phone storage. Still, the data can only be retrieved during the collection of forensic evidence. Hence more studies explain why such data on the path cannot be retrieved on the iPhone devices easily but on Android in a simple way. Other studies have addressed forensic analysis and the recovery of all of the activities performed on the networking applications on those smartphones. Still, they are limited to access to the recovery of the basic information related to the use of social networking applications (Twitter and Instagram). Our study focused mainly on the recovery of the artifacts and the traces related to the use of the applications on a variety of smartphones by using the different operating systems. We aimed to observe if the activities performed through these activities are stored or recovered from the memory of smartphones.
The study explored the forensic acquisition and the examination of the logical backup copies of the smartphone. It also consisted of installing the social networking applications on the smartphone and therefore conducting an activity that is seen to be common from each of the applications and later performing forensic analysis on each of the logical images that have been acquired from the databases. The results proved valuable data that would be recovered on the android phones by the forensic investigator. In addition, we documented the nature of the social networking data, which would later be recovered from each of the devices and their locations from the backup files.